To Attack or Not to Attack: Targeting the Healthcare Sector in the Underground Ecosystem
Victoria Kivilevich, Threat Intelligence Analyst
Following the news of the first patient death due to a ransomware attack, KELA analyzed cyber threats and ransomware attacks against healthcare institutions and explored what ransomware operators state about targeting healthcare institutions, along with darknet chatter on the matter.
Key points:
- In August-September 2020, more than 20 healthcare organizations were compromised either in ransomware attacks or via the sale of remote accesses to their networks.
- Some new ransomware gangs emerged in the last two months stating they won’t target hospitals and healthcare organizations. However, these promises were broken “by mistake”.
- Triggered by the news of the first patient death, users of underground forums engaged in debates on whether or not these ransomware operators were guilty, and if all cybercriminals should avoid profiting off of targets in the healthcare sector altogether.
Statistics: Ransomware Attacks and Sales of Entry Points
During August and September 2020, at least 11 organizations from the healthcare sector were targeted by operators of Sodinokibi (REvil), Maze, Netwalker, Conti, SunCrypt, and Ryuk. Most of these institutions were published on their respective blogs because they didn’t take part in negotiations and/or didn’t pay a ransom (some victims were taken from public reports). However, as many victims may pay the ransom in order to avoid being shamed on the ransomware gangs’ blogs, we cannot confirm the real number of healthcare organizations targeted that have truly been targeted by ransomware.
These victims included:
- Australian organization providing support for families, carers, and people with mental health issues (attacked by Sodinokibi)
- US fertility and gynecology practice (Netwalker)
- US medical center (Maze)
- US health network with six hospitals included (Sodinokibi)
- US hospital (SunCrypt)
- US hospital (Conti)
- Two US dentistries (Conti)
- Canadian college of nurses (Netwalker)
- UHS Hospitals (Ryuk)
- Duesseldorf University Clinic (DoppelPaymer)
Moreover, 11 “accesses” to healthcare organizations were published for sale on underground forums from August to September 2020. Threat actors use this term to describe multiple different vectors, permission levels, and entry points that enable attackers to compromise the targeted network and perform malicious actions, such as deploying ransomware. These accesses are usually being sold by initial access brokers and can be bought by ransomware affiliates, who are working directly with ransomware operators and use their malware in exchange for profit-share from paid ransoms.
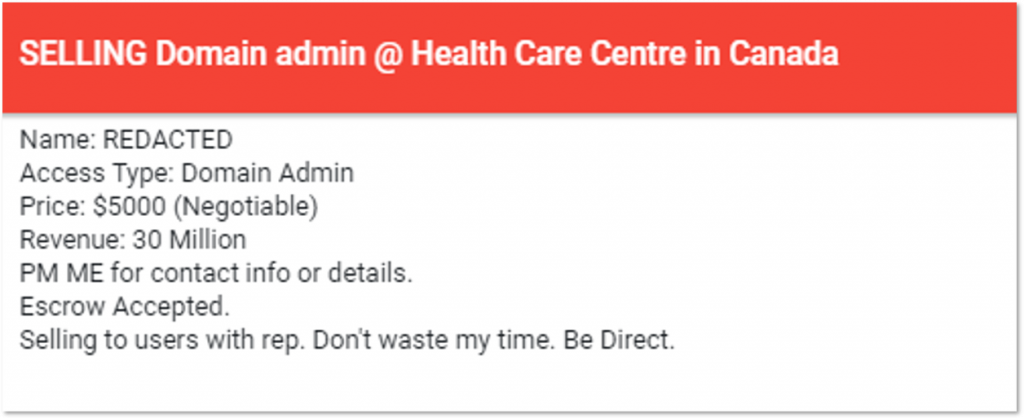
For example, the most expensive access was on sale for $5,000, while the average price was around $2,700. A threat actor that posted the offer claimed that it provides buyers access to the network of a Canadian healthcare center. Upon further analysis into this, KELA’s researchers were able to identify this victim as a community health center providing various healthcare services. Interestingly enough, the offer, posted on September 8, is now deleted. The deletion of this listing could be due to one of the three possible reasons:
1. The actor decided to stop the sale altogether;
2. The deal was made (though usually the actors would state this in the thread)
3. The listing received unexpected attention from media or researchers.
As KELA’s DARKBEAST caches all data that is crawled, we were still able to access the post of the now-deleted Canadian health center offer
When looking into the most active threat actor targeting the healthcare sector, KELA’s researchers detected a threat actor who has published access to at least four different healthcare organizations across the US, UK, and China. These targets were compromised as part of a larger compromise of organizations using RMM software called ManageEngine Desktop, where a threat actor published more than 50 compromised network accesses for sale, including those previously listed in the healthcare sector.
Ransomware Gangs and Pandemic: To Attack or not to Attack
In March 2020, when the pandemic was globally declared, some ransomware operators stated they will not target hospitals during the coronavirus outbreak, while others claimed they never attack medical institutions. However, these promises were not fulfilled. For example, Maze that published a special press release on the matter was still spotted exposing the US medical center as a victim in August 2020. Usually, the ransomware operators state that attacks on hospitals are solely by coincidence, but in this case, it’s hard to believe in coincidence when the Maze operators published the victim on their blog and publicly demanded ransom instead of providing a free decryptor.
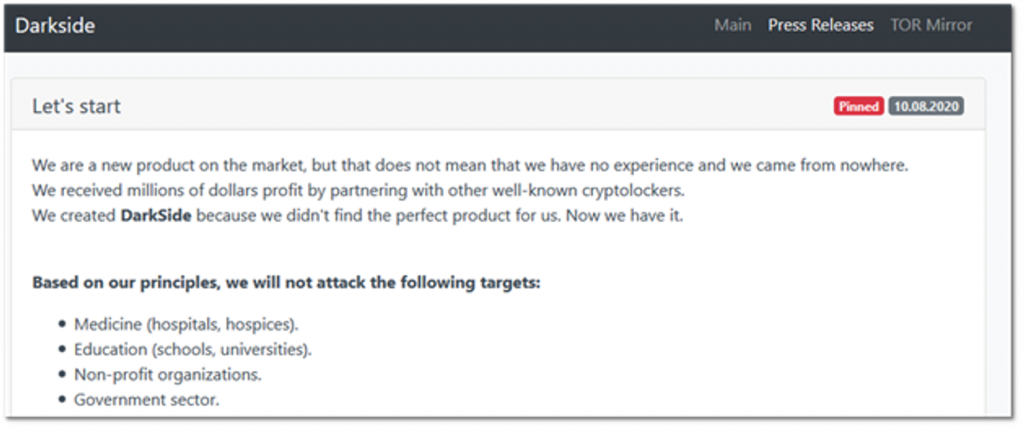
During the summer, new ransomware groups emerged – some of them declared the same policy, where they will refrain from targeting medical institutions. For instance, DarkSide claimed it won’t attack hospitals and hospices, alongside schools and universities, and non-profit and government organizations.
From DarkSide’s blog
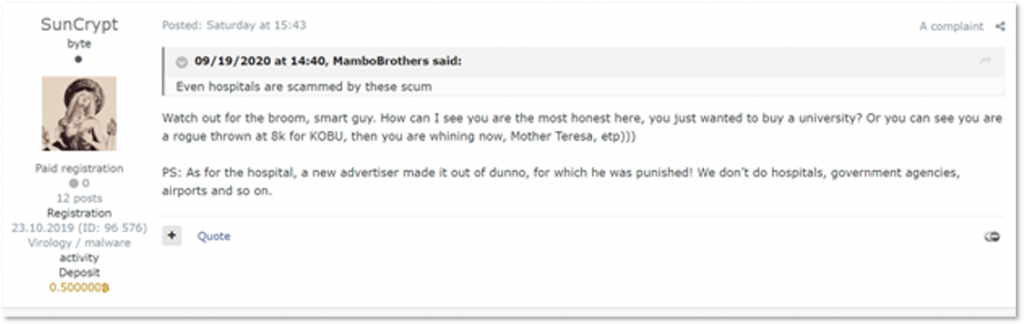
SunCrypt, another new gang, also stated it doesn’t attack hospitals, as well as government institutions, airports, and some other targets. However, this statement was made in discussions regarding the SunCrypt attack on a US university hospital – which was described by SunCrypt operators as an accident that occurred due to the fault of a new affiliate.
From SunCrypt’s thread on a Russian-speaking underground forum (auto-translated from Russian)
As for Conti – one more fresh ransomware gang – they didn’t mention anything about targeting (or not, for that matter) medical institutions on their blog and apparently have no moral dilemma with it: at least three victims from the healthcare sector are already in Conti’s list. Mount Locker and Egregor also didn’t express special policies regarding healthcare organizations.
Darknet Chatter Full of Judging
Across different underground forums, members frequently disapprove of attacking healthcare institutions. When seeking accesses for sale or ransomware affiliates, some of them state they do not take offers related to healthcare organizations. One recent example illustrates how these discussions can escalate and actually make some users delete such offers.
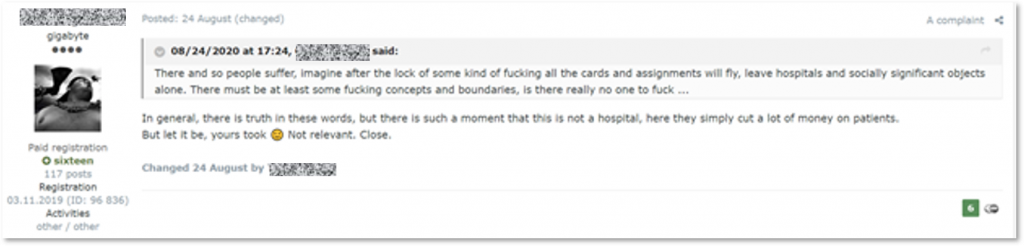
On August 24, a member of a Russian-speaking underground forum published for sale admin access (meaning it has the highest privileges) to a “center for the treatment of psychological illnesses and drug addiction”. Instead of questions from the buyers, he received negative feedback: another user suggested to “leave alone” hospitals and other valuable institutions for the society, stating to refrain from causing them damage. In response, the seller closed the thread – showing that public opinion about attacking medical organizations can matter.
The seller chooses to close the sale (auto-translated from Russian)
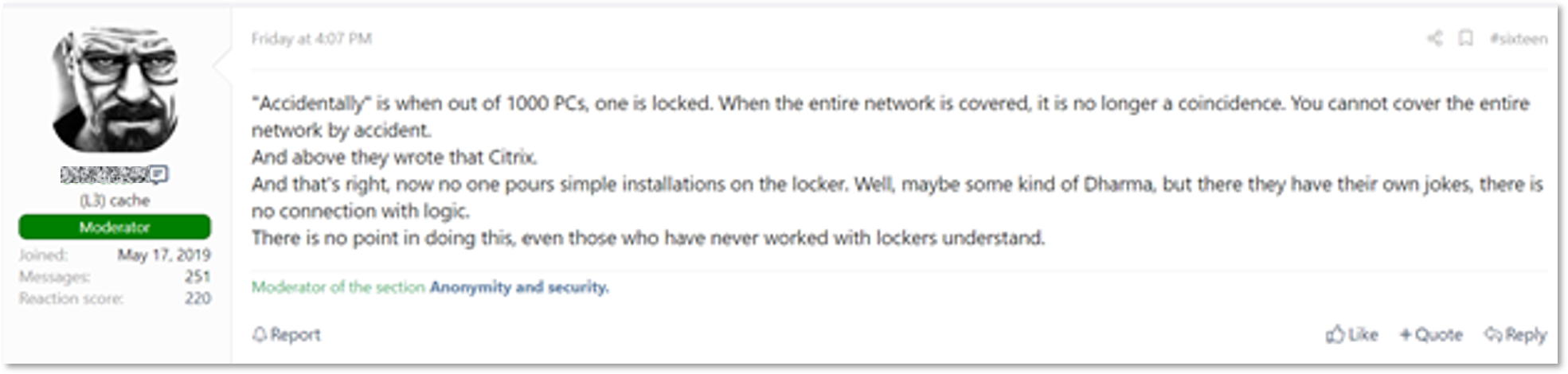
Recent discussions on the subject are related to the news of the first patient death caused by a ransomware attack. In one thread on a Russian-speaking underground forum, opinions are divided: while some state that hospitals got infected because of automated ransomware attacks, others claim that in the case of the German hospital, it is more similar to a targeted attack. They refer to the exploitation of the Citrix vulnerability (CVE-2019-19781), which was reportedly an infection vector for the attackers.
A forum user states that the attack is not an accident because the whole network was encrypted (auto-translated from Russian)
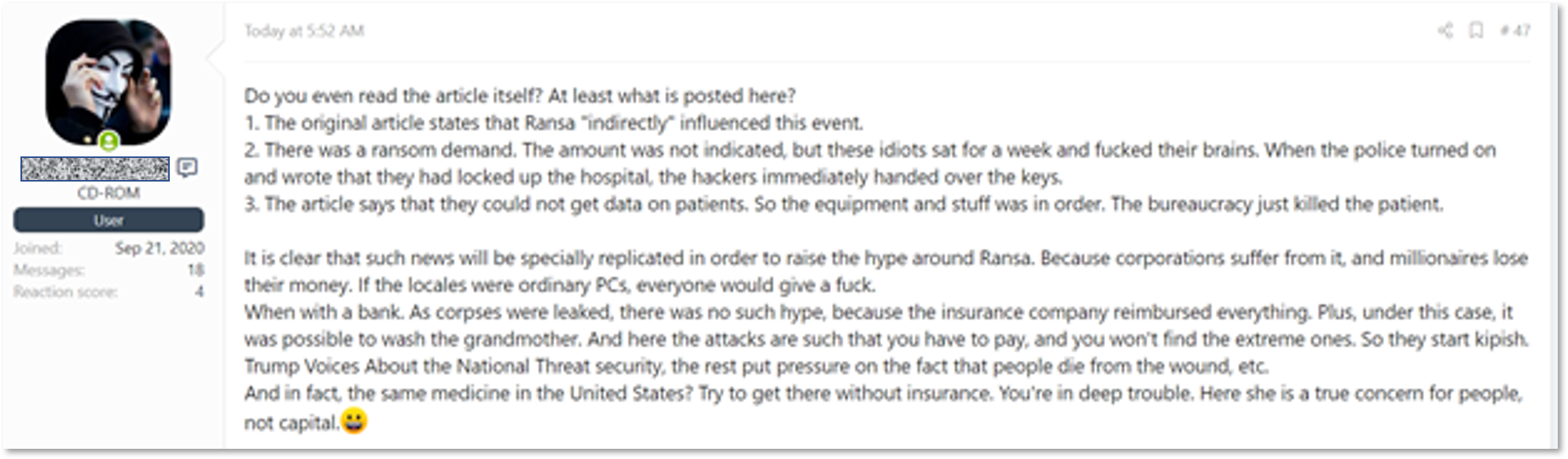
The exploitation of the flaw raised another discussion – who is indeed guilty, the attacker, or the administrator that did not patch the vulnerable software. Finally, some users are not sure it’s even unethical to target hospitals due to different circumstances and the capitalist nature of medicine in certain countries.
Auto-translated from Russian
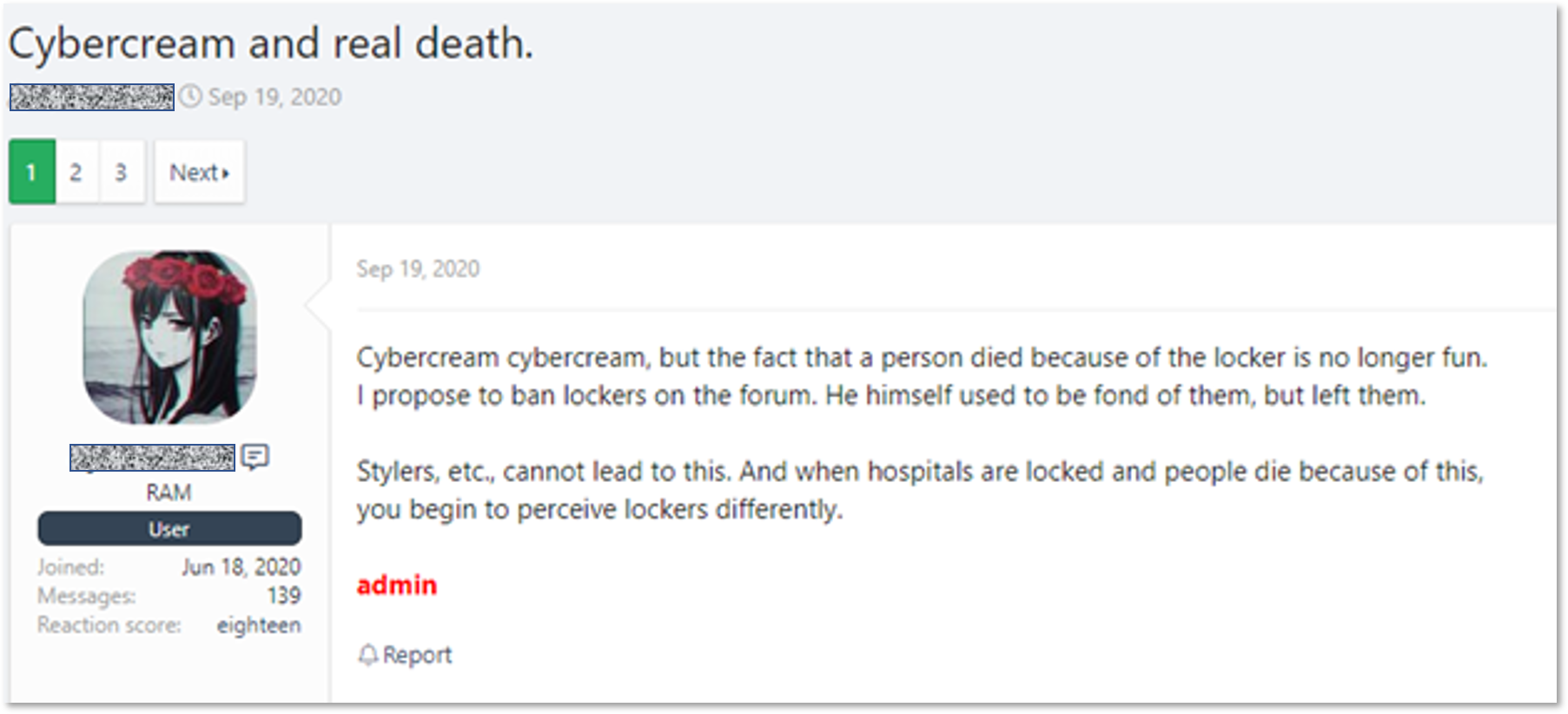
Some users even suggested banning ransomware operators and affiliates on the forum. However, this is a fantastic outcome of events, because ransomware gangs are one of the main buyers of accesses sold on underground forums. They operate significant funds, as it was recently proved by Sodinokibi (REvil) when the gang made a $1 million deposit on a hacking forum.
All in all, the darknet chatter about targeting medical institutions is very active. Hypothetically, some united policy can be adopted by threat actors, as seen in the case of targeting Russia and CIS countries. It means Russian-speaking cybercriminals prefer not to attack organizations from these countries, while underground forums’ admins tend to delete offers related to CIS. However, it’s hard to assume if the recent news will lead to such a policy regarding healthcare organizations since public opinion is quite scattered.