The Secret Life of an Initial Access Broker
Victoria Kivilevich, Threat Intelligence Analyst and Raveed Laeb, Product Manager
Recently, ZDNet exclusively reported a leak posted on a cybercrime community containing details and credentials of over 900 enterprise Secure Pulse servers exploited by threat actors
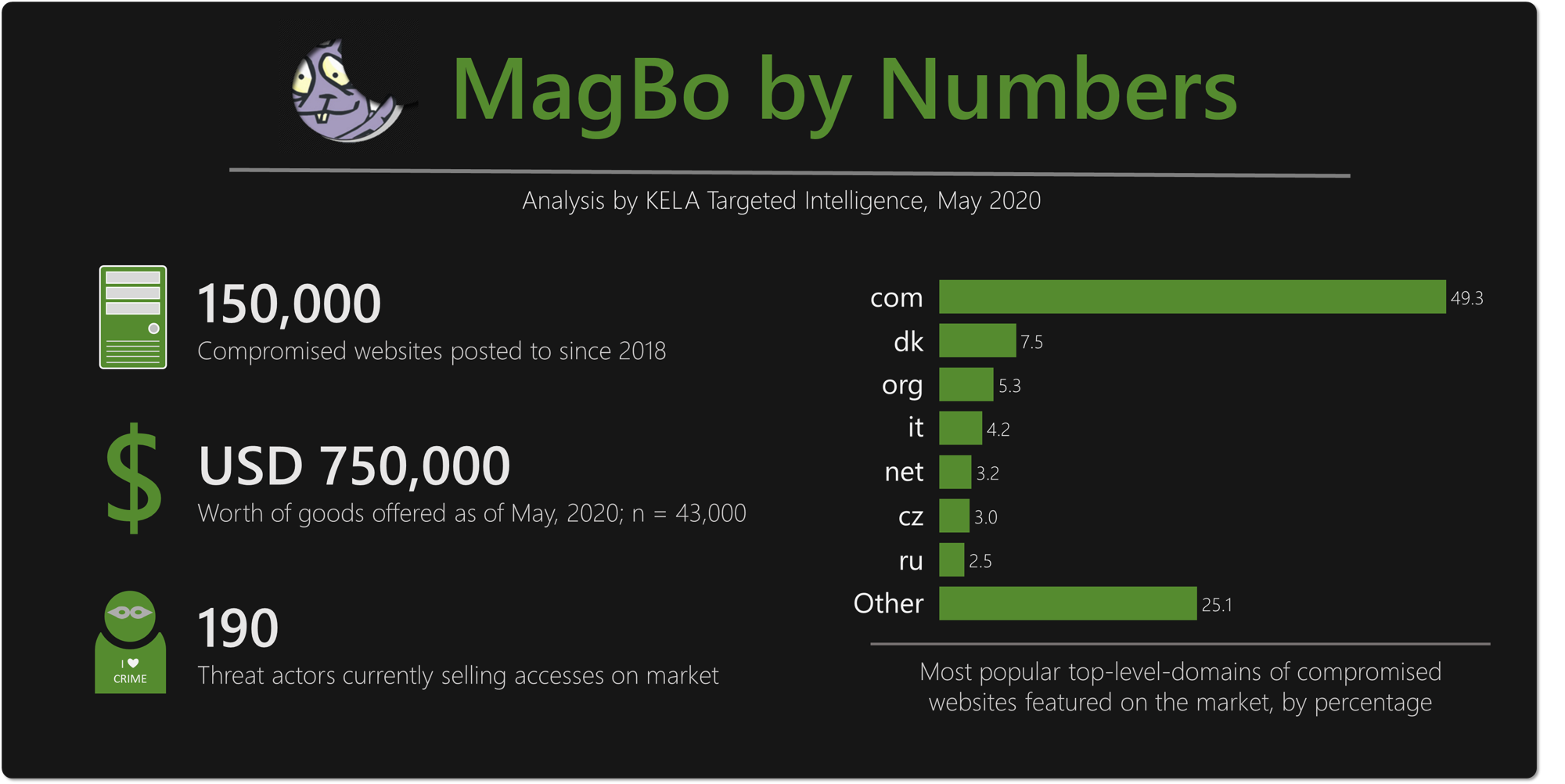
Since this leak represents an ever-growing ransomware risk, KELA delved into both the leak’s content and the actors who were involved in its inception and circulation
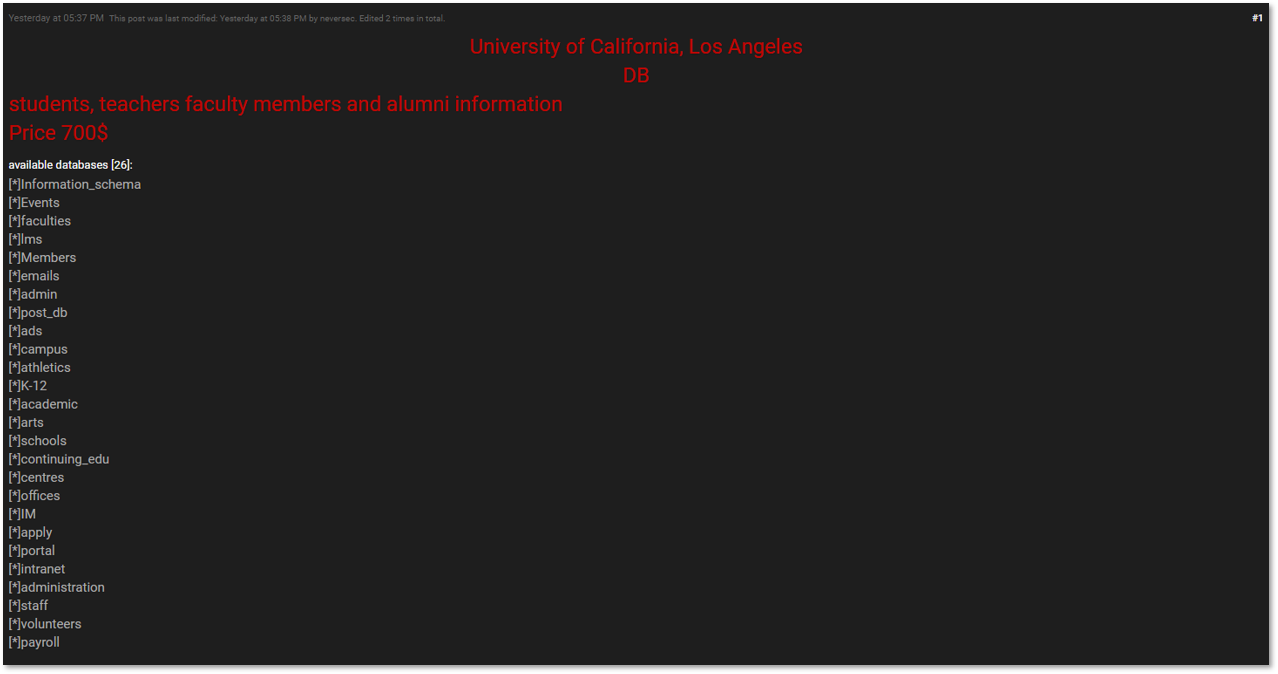
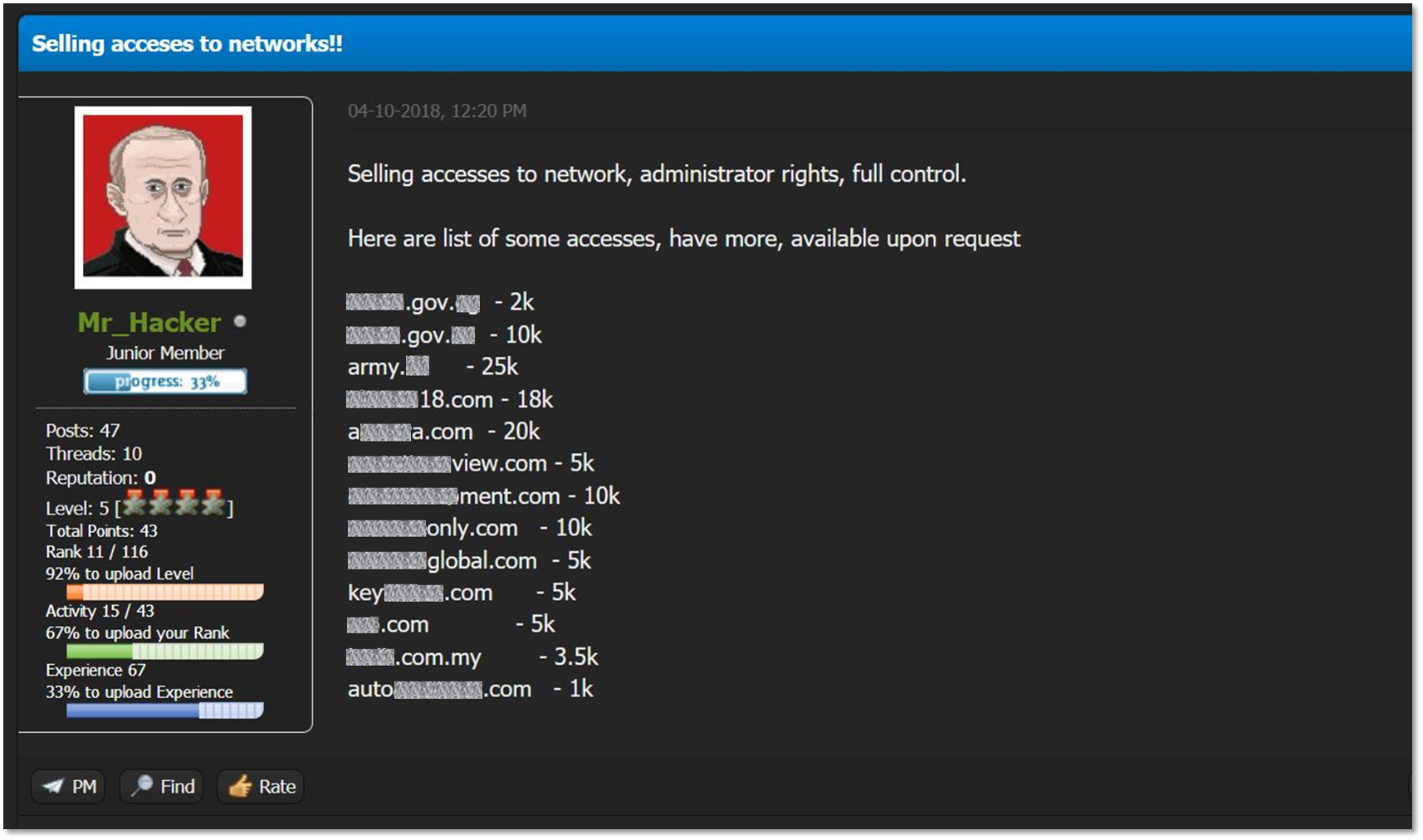
This short research targets a specific tier of cybercriminal actors – Initial Access Brokers. These are mid-tier actors who specialize in obtaining initial network access from a variety of sources, curating and grooming it into a wider network compromise – and then selling them off to ransomware affiliates
With the affiliate ransomware network becoming more and more popular and affecting huge enterprises as well as smaller ones, initial access brokers are rapidly becoming an important part of the affiliate ransomware supply chain
The list leak mentioned above seems to have been circulating between several initial access brokers in cybercrime forums, and have been exposed by a LockBit affiliate who regarded the actors as unprofessional
This event showcases the breadth of information that’s exchanged on cybercrime communities and, in KELA’s eyes, emphasizes the need for scalable and targeted monitoring of underground communities