THREAT ACTORS
Gain insights into cyber threat actors’ in-depth intelligence: motivations, fields of activity, geographies, handles, contact details, and more!
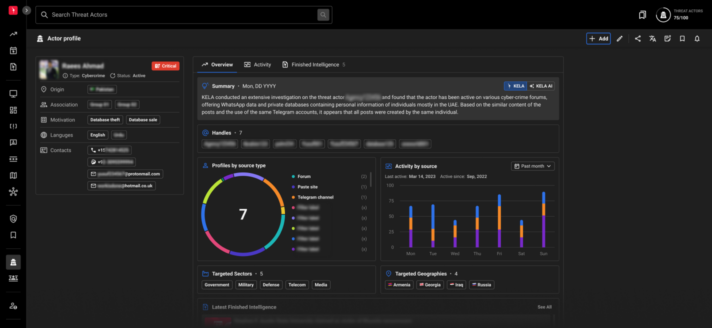
KELA’s Threat Actor module offers a holistic profile of individual threat actors, consolidating their online personas into a unified view.
By cross-checking multiple layers of data associated with the same actor, Threat Actor Module goes beyond analyzing published data and posts. This comprehensive approach provides a broad understanding of both the threat actor’s activities and characteristics.


UNDERSTAND THE ADVERSARY MIND
Empowering Enterprises, Governments, and Law Enforcement Agencies with Advanced Threat Actor Analysis
Outpace threat actors' plans and empower your security teams with robust resources for in-depth analysis of both relevant and specific threat actors. With an extensive data lake, advanced filtering, and high-quality finished intelligence from KELA's intelligence experts, the Threat Actor module enables proactive and effective cyber defense strategies by leveraging interconnected data sources.
Stay ahead of nation-state attacks, hacktivists, and other malicious actors targeting your nation with the module's precise investigative techniques. Identify suspects, uncover criminal activities, detect threat actors, and trace them through comprehensive cross-data checks and expertly curated finished intelligence, ensuring a comprehensive understanding of a specific target of interest.
HOW IT WORKS

SEARCH ALGORITHM
Easily narrow the investigation effort down to a specific Threat Actor with the Advanced Search algorithm.

ADVANCED FILTERING
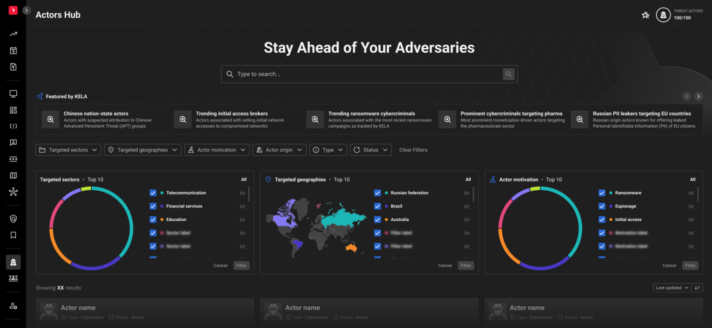
Conduct in-depth research through interactive advanced filtering to identify actors posing potential threats to your organization. Leverage geographies of activity, threat actor types, time spans, and sectors to narrow down relevant information.

FEATURED BY KELA
Benefit from KELA’s Cyber Intelligence Center’s recommendations regarding emerging and top-priority threat actors.
KEY CAPABILITIES

PRECISE FOCUS
Utilize advanced filters and targeted search capabilities to focus on the most relevant or specific threat actors

COMPREHENSIVE SEARCH
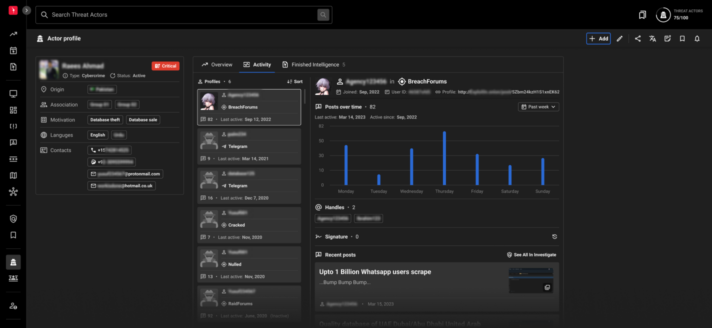
Easily search for a threat actor's profile by their handles on cybercrime underground sources, as well as by additional identifying details - social media accounts, bitcoin wallet numbers, names, and more.

UNIFIED PROFILES
Access consolidated profiles of threat actors' based on their personas on different cybercrime underground sources.

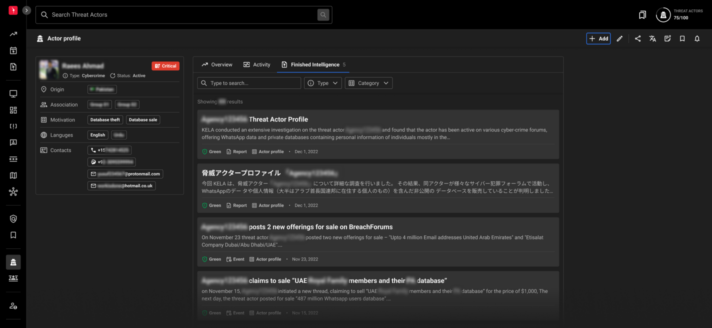
EXPERT INSIGHTS
Leverage KELA's Threat Intelligence Analysts' recommendations and proactive insights both on initial investigation level and on individual threat actor’s overview pages.

AI PROFILER
Utilize KELA top-notch AI capabilities to generate advanced summaries with a single click.

SEAMLESS INTEGRATION
Streamline API integration with in-house databases and tools for comprehensive investigations.

EFFORTLESS NAVIGATION
Navigate smoothly across KELA's Cyber Threat Intelligence Platform modules for enhanced investigation.

VISUAL ANALYTICS
Obtain comprehensive data aggregation and visual graphs to gain a wide-angle view of threat actor profile metrics.