Protect Against Compromised
Assets and Identities
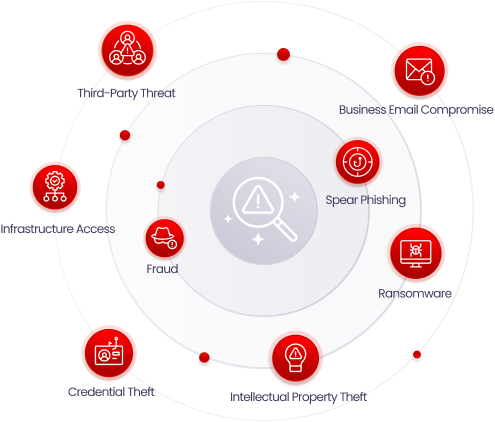
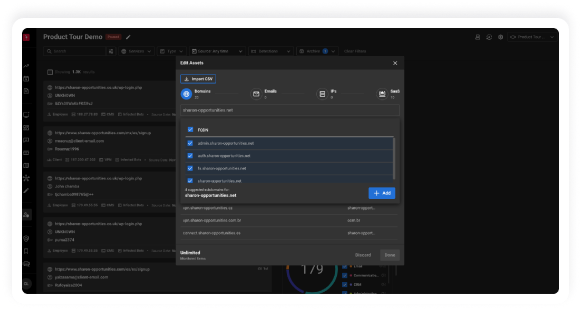
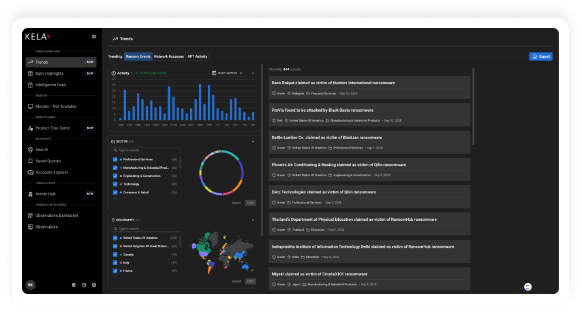
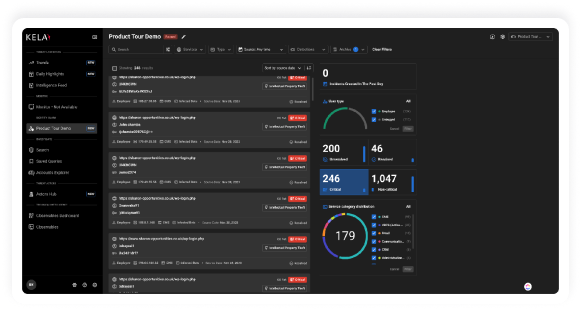
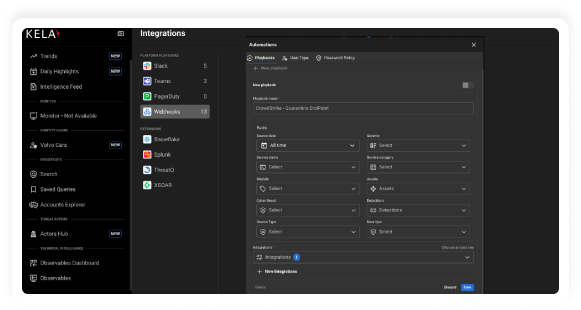
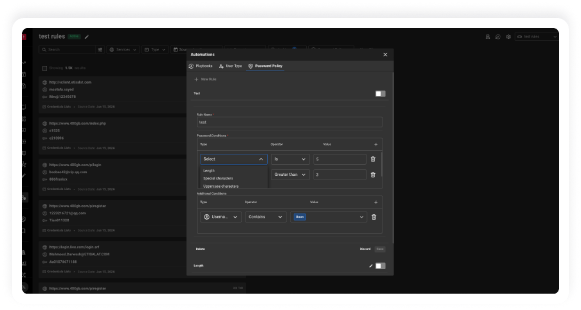
Valid account abuse has emerged as the leading initial attack vector used by Cybercriminals,
responsible for nearly 50% of cyber attacks. Defending against this threat is straightforward
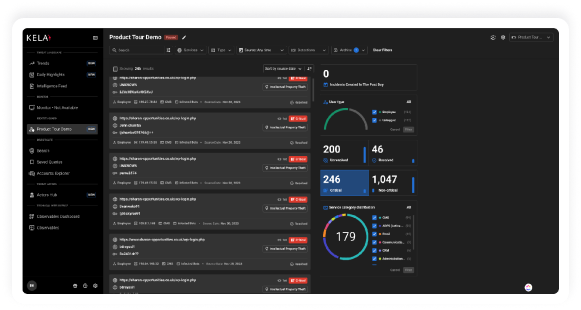
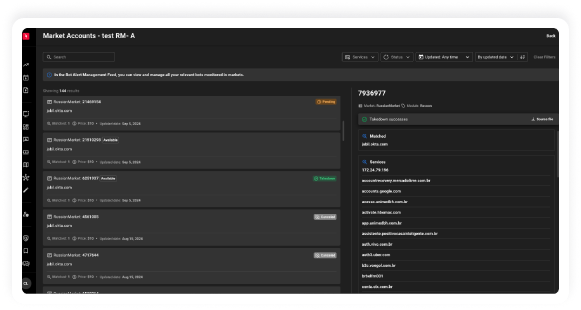
with KELA’s Identity Guard. Our solution mitigates the risk of cyber attacks by identifying
compromised accounts linked to your organization’s digital assets in real-time.