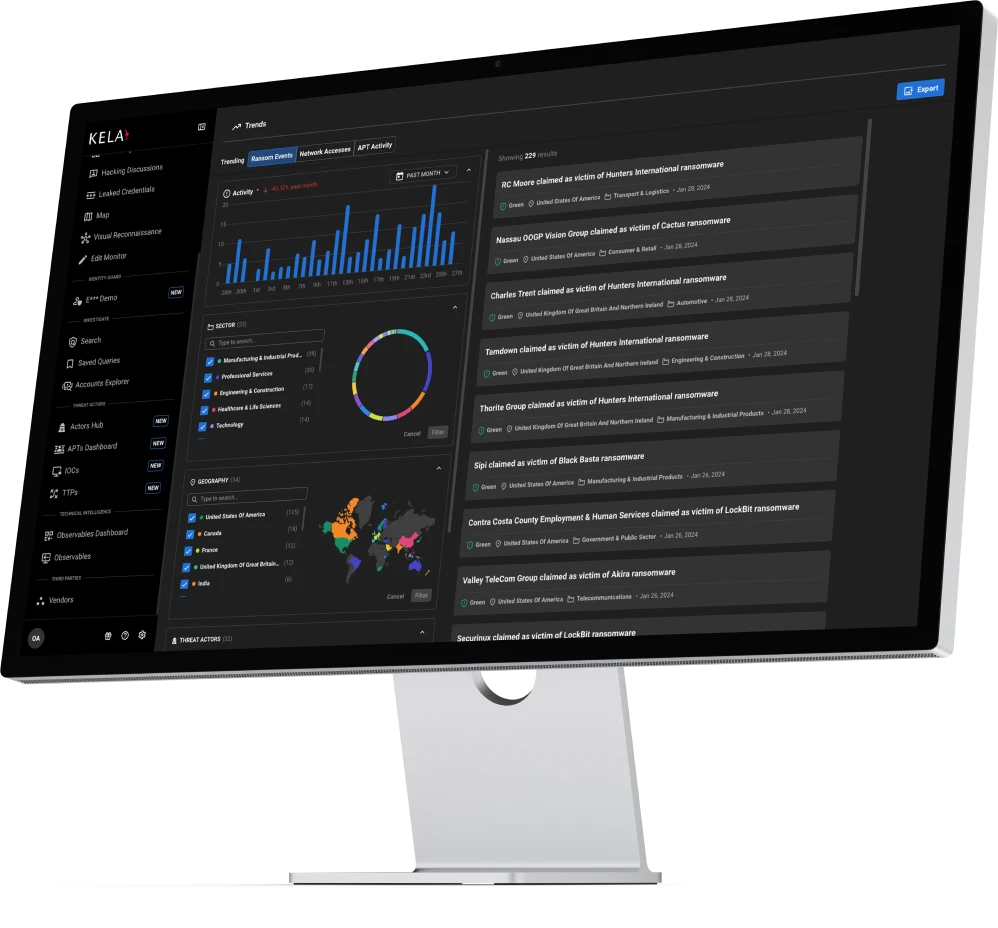
Proactive, Real-Time Defense Against The #1 Cause of Cyber Breaches
- All-Round Exposure Intelligence: CTI, DRPS, EASM and TPRM
- Discover Compromised Assets & Identities
- Eliminate the #1 Cause of Cyber Attacks
- Proactive and Automated Defense
Get Started for Free
Want to talk to an expert first? Book a Call
Due to the sensitive nature of the intelligence we handle, we are required to conduct a brief verification before activating your free trial account.
Who Are Our Clients?
Businesses
Enterprises
Law Enforcement
Government
GenAI Developers
Why Our Customers Love Us
- Stop Real Attacks Before They Happen
- Exposure-Centric with Actionable Intelligence
- Automated and Easy to Use