Have a SAFE ride – Cyber Threats in the Automotive Sector
Published September 12, 2023.

In recent years, the automotive industry has been undergoing a rapid transformation of digitalization. As new technologies become increasingly prominent in the automotive sector, they open the door to a wide range of cyber threats and high interest from cybercriminals to attack automotive companies.
The automotive industry includes a wide range of stakeholders. Beyond the big original equipment manufacturers (OEMs) that manufacture the cars, there are also Tier 1 and Tier 2 suppliers and third-party service providers. This enables cybercriminals to find the weak points through different parties and leverage them for their own gain. For example, in January 2023, a person was able to unlock Electrify America’s charging stations and posted two videos showing how easy it is for threat actors to breach the chargers’ security network.
In this blog, KELA delves into the landscape of automotive cyber threats, uncovering potential risks to the industry. The cyber threats can include leaking brands’ data, deploying ransomware, and launching distributed denial-of-service (DDoS) attacks. The interconnectivity of vehicles also results in exploiting vulnerabilities in automotive products and trading of hacking tools such as keyless devices designed to facilitate stealing cars.
Remote hacking and unauthorized access
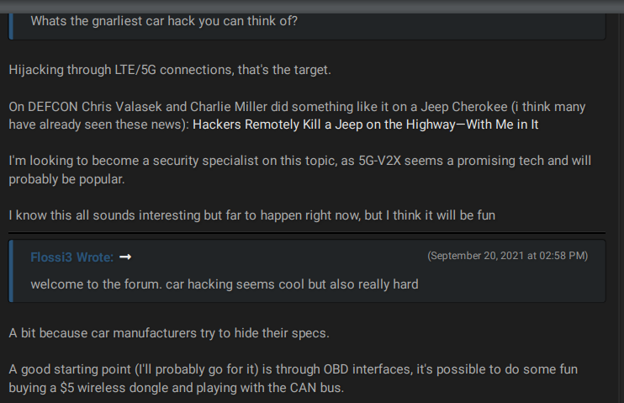
With the increasing use of technology in the automotive industry, car hacking has become a big concern for both OEMs and suppliers. Cybercriminals aim to hack into cars and gain unauthorized access to a vehicle’s computer systems. This could allow them to manipulate vehicle controls, steal personal data, or take control of the vehicle itself.
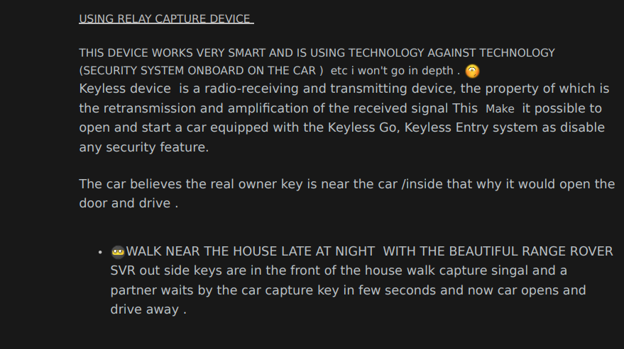
Researchers found that in 2022, remote keyless vehicle thefts and break-ins accounted for almost a fifth of all incidents in the automotive industry. Remote keyless entry systems are radio remote controls capable of unlocking a car and starting the engine. Cybercriminals use several devices to amplify and transmit the signal from the owner’s key fob to the vehicle’s entry system, tricking it into unlocking the car.
KELA observed a high interest in keyless devices among threat actors. Those devices allow actors to conduct keyless entry attacks, manipulating the key fob to unlock and steal the car.
An actor explains on a German-speaking cybercrime forum how to launch relay attacks using a keyless device.
Threat actors sell keyless devices on cybercrime forums for car theft. For example, an actor offered equipment for stealing Lexus and Toyota cars for almost USD 4,000. The actor also offered for sale “Game Boy,” which can unlock and start vehicles, for around USD 22,000. The device is built from devices similar to the old Nintendo Game Boy, the handheld gaming devices popular among teenagers. Game Boy can be used to record data from a car, and the vehicle’s system will then recognize it as an authorized remote to control its entry and ignition. KELA also observed demand for Game Boy devices that fool the car’s keyless entry system.
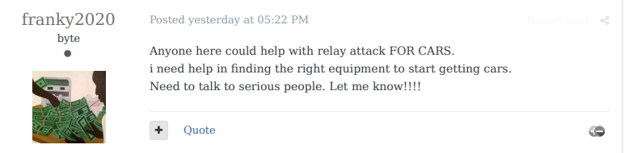
An actor is looking for assistance to hack a car.
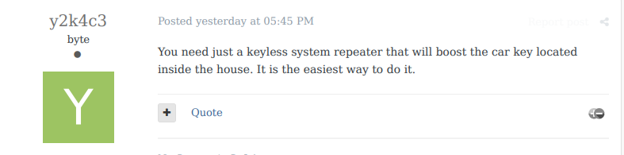
An actor replied that a keyless repeater device would be useful for that.
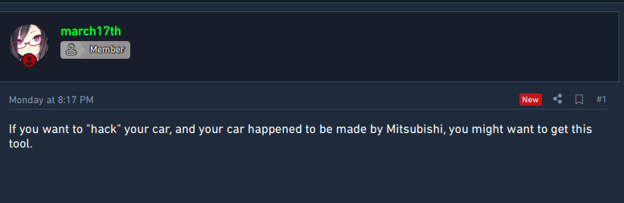
An actor shared a tool for changing the coding and diagnostics of Mitsubishi vehicles.
Vulnerabilities in industry-related products
The automotive industry’s complex supply chain involves numerous suppliers and third-party components, increasing the risk that components can be exploited and that threat actors can find a potential entry point for cyberattacks. Vulnerabilities can affect OEMs; Tier 1 and Tier 2 suppliers that produce software and hardware modules; and third-party providers of products such as fleet management systems and aftermarket devices. Vulnerabilities that aren’t patched on time can affect millions of vehicles.
In January 2023, researchers discovered vulnerabilities in the API endpoints that vehicle telematics systems used, which potentially allow a threat actor to send and receive text messages, retrieve live geolocation, and disable hundreds of millions of SIM cards installed in the biggest car brands, including Tesla, Subaru, Toyota, and Mazda.
In April 2023, researchers identified a security vulnerability tracked as CVE-2023-29389, which allows criminals to steal vehicles using the controller area network (CAN) injection method. CAN bus network is a communication protocol, used in vehicles and other industrial systems, to allow different electronic components to communicate with each other. In a CAN injection attack, the actor accesses the vehicle’s internal network and crafts a CAN message, tricking the car’s security system into unlocking the vehicle.
Users recommend manipulating CAN bus through the on-board diagnostic interface, which allows vehicle performance to be monitored.
Recently, Ford warned of a buffer overflow vulnerability (tracked as CVE-2023-29468) in its SYNC3 infotainment system, which could allow remote code execution. SYNC3 is a modern infotainment system that supports in-vehicle Wi-Fi hotspots, third-party applications, and more. KELA tracks vulnerabilities and exploits discussed on cybercrime sources, enabling organizations to assess their risk exposure and make informed decisions.
Ransomware attacks
Ransomware groups have targeted the automotive industry, attacking OEMs, suppliers, and third-party vendors. A ransomware attack against one supplier can significantly affect the supply chain and global operations of all the players and customers involved. In recent years, big automotive brands such as Honda, BMW, and Toyota and their suppliers have fallen victim to ransomware attacks.
KELA has been monitoring ransomware blogs, negotiation portals, and data leak sites, where ransomware attacks are claimed. Since 2021, more than 200 ransomware attacks have targeted the automotive sector. It’s important to note that other ransomware attacks against automotive component suppliers can be classified under the manufacturing sector.
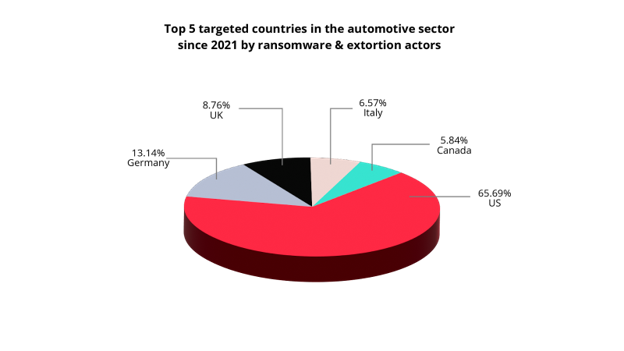
The US tops the list of countries where ransomware attacks in the automotive sector have occurred, followed by Germany, the UK, Italy, and Canada. The top ransomware group is LockBit, which is responsible for more than 20% of ransomware attacks in the automotive industry.
KELA has also been tracking the activity of initial access brokers, which play an important role in a ransomware-as-a-service supply chain. These actors, who attempt to gain access to compromised networks, and sell it to other users, giving them the chance to perform various attacks including espionage and deploying ransomware, were also seen targeting automotive companies. The countries where most of these attacks have occurred since 2021 are the US, China, India, Canada, and Australia.
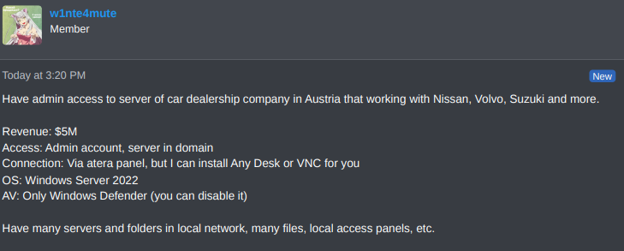
Recently, on August 6th, KELA detected a valuable offer when the threat actor Totemchikkkk was observed selling access to a China-based automotive company with a revenue of USD 3.3 billion. The access was offered for sale for USD 4,000. Just a few weeks after, on August 29, another actor was selling access to an Austria-based car dealership company that, according to the actor, works with Nissan, Volvo, Suzuki, and more.
An actor is selling RMM access to a car dealership in Austria.
Data breaches
Threat actors can steal internal automotive data that is then shared, sold, and traded on cybercrime forums and through various other channels. This data can include corporate credentials, internal documents (such as financial), source code, customers’ personal identifiable information (PII), and more.
In the past years, some of the big automotive companies such as Mercedes-Benz, Volvo, and Audi suffered data breaches, and their internal data has been leaked and circulated on cybercrime forums. Some of the databases are reposted on cybercrime forums and reused by threat actors for further malicious purposes.
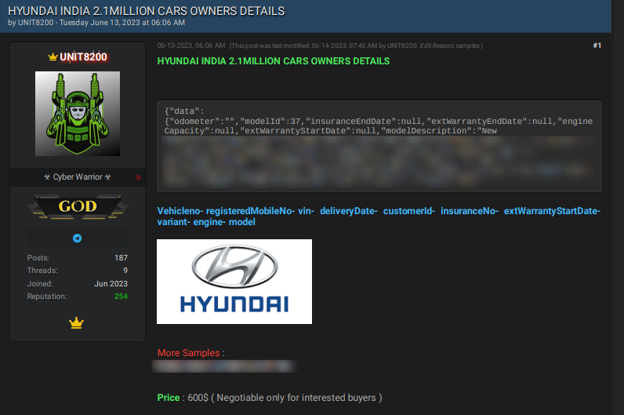
For example, on February 6, 2023, a threat actor offered a Hyundai India database for sale. According to the actor, the leak exposed 2.1 million company records, including information on car owners, such as insurance end dates, engine capacity, mobile phone number, and vehicle number. The database was offered for sale for USD 200. Interestingly, the same database is still being sold by the same actor on another forum, now for USD 600.
The recent offer of Hyundai India’s database.
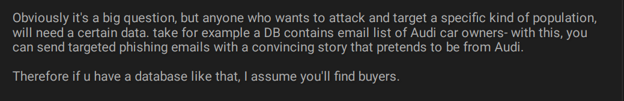
The cybercrime chatter suggests that threat actors use valuable data for phishing campaigns, targeting a specific audience like car owners, and tricking customers into providing sensitive information.
An actor explains how to make money from leaked data of Audi car owners.
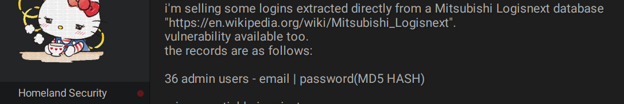
An actor is selling login credentials and vulnerability to the Mitsubishi Logisnext database.
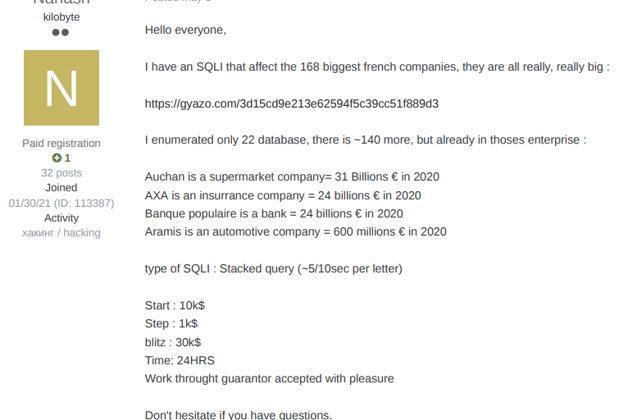
An actor is selling an SQL exploit to download databases of an automotive company.
Automotive companies’ corporate information is also in demand by cybercriminals. In June 2023, an actor who was interested in Honda’s database that was leaked in 2019 included 134 million documents related to the internal network and computers. In addition, the company also suffered another cyber incident, in June 2023 it was reported that Honda API flaws exposed customer data, dealer panels, and internal documents. In July 2023, an actor was interested in an Audi and Volkswagen leak. The breach was reported in 2021, while the data – which was stolen from a vendor used by VW, Audi, and some of their dealers – had been gathered between 2014 and 2019.
These examples show that threat actors continue to look for sensitive credentials for phishing campaigns and further cyber attacks, and therefore it’s crucial to be aware of previous data breaches and disable employees’ credentials.
DDoS attacks
DDoS attacks are a threat to a number of industries, including automotive. DDoS attacks aim to disable web servers and prevent customers from accessing essential resources. Companies can suffer DDoS attacks due to various reasons, with some attackers targeting specific businesses, while others, such as hacktivists, DDoSing websites more opportunistically.
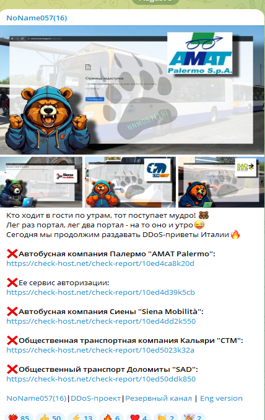
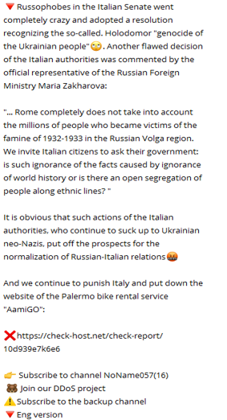
For example, due to the Russia-Ukraine war, pro-Russian hacktivist groups conduct DDoS attacks against countries that support Ukraine. In this regard, a pro-Russian hacking group, “Noname057(16),” took responsibility for DDoS attacks against Italy and also attacked automotive websites such as AmiGO, a car- and bike-sharing service operating in Palermo, Sicily:
How can OEMs and automotive suppliers defend themselves against cyber threats?
- Implement robust security practices: Automakers and suppliers need to adopt best practices for secure software development, including regular code audits, penetration testing, and adherence to security standards.
- Monitor cybercrime sources: Organizations must actively monitor cybercrime platforms, from cybercrime forums and marketplaces to Telegram channels, to get valuable insights into emerging automotive threats, exploits, and hacking tools.
- Update and patch software: Organizations must address software vulnerabilities through regular updates and patches to prevent exploitation by cybercriminals.
- Enact secure communication protocols: Encrypt communication over networks and implement intrusion detection systems to monitor for unusual communication patterns.
Click here to create a free KELA account and uncover threats directly aimed at your automotive organization.