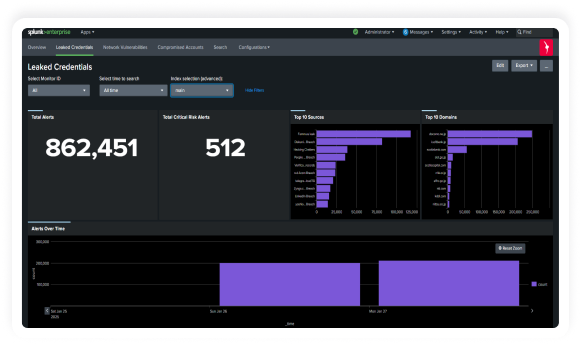
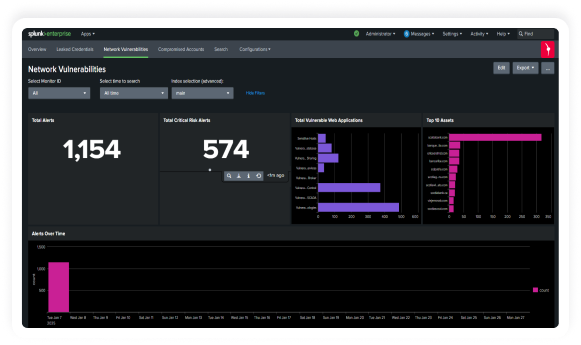
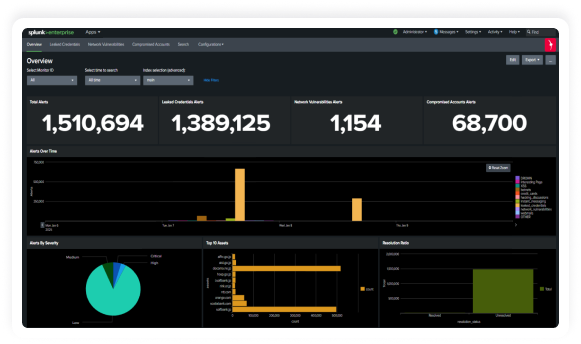
Bolster threat detection and response capabilities,
monitor and protect identities, and access enriched data
Inside your Splunk environment – powered by KELA.
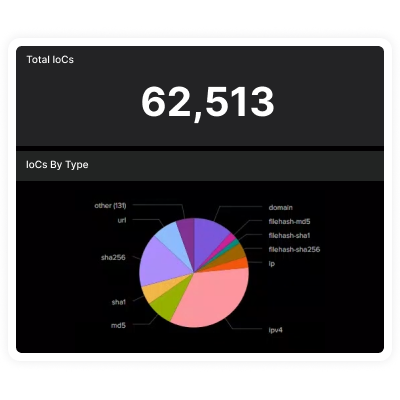
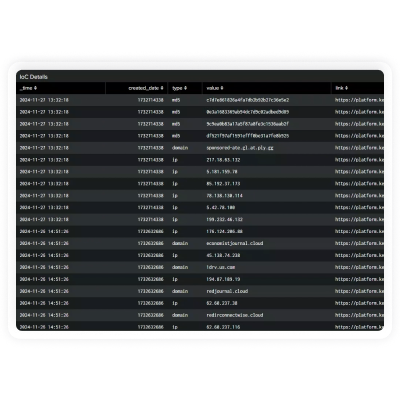
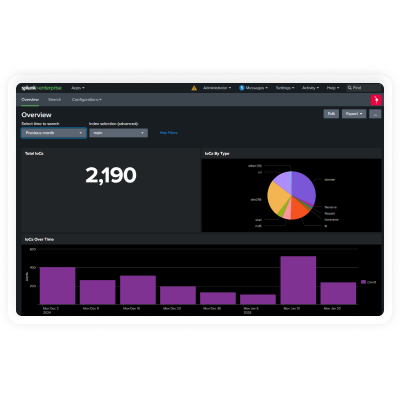
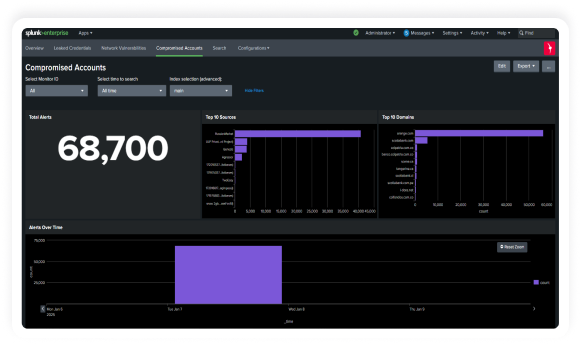
Empower your Splunk environment with KELA’s cutting-edge threat intelligence to enhance
proactive threat detection and risk mitigation. KELA’s integration with Splunk provides real-time
intelligence on compromised assets, cloud applications and identities, enriching your security event data
with attacker-driven insights to deliver contextual, risk-driven defense