5 Questions About Hamas-Israel War
Updated December 19, 2023.

As we approach the end of 2023, the Hamas-Israel war still rages on, and so do cyberattacks accompanying it. KELA selected 5 questions out of those we’ve been asked by our clients and partners (aside from “how are you?”) in the past 70+ days, and represent the cybersecurity angle of a physical war.
Why Should I Be Concerned About Cyberthreats if This is a Physical War?
Unfortunately, hybrid warfare has been around for multiple worldwide geopolitical and military conflicts in the past 20 years (give or take). Hybrid warfare blends traditional military warfare actions with cyberwarfare and irregular warfare in the pursuit of political goals. The cyberwarfare accompanying the Russia-Ukraine war has demonstrated that a sophistication of a nation state actor is not required to cause inconvenience and interruption of services. KELA has observed over a hundred hacktivist campaigns, predominantly pro-Russian, carrying out different cyber attacks with varying levels of complexity against Ukrainian target organizations.
Similar trends are seen by KELA in the Hamas-Israel war – perpetrated by pro-Hamas and pro-Palestinian collectives. While much of the targeting falls onto companies and organizations (governmental, military) in the war-participating sides, KELA also observed significant targeting of third parties, especially if those or the countries they’re active in are involved in the support of the opposing side. Hence, unfortunately, this war is not only physical, and organizations are definitely concerned.
Does Hamas Pose a Cyber Threat or Has Serious Cyber Capabilities?
Over the years, there have been several activity clusters attributed by researchers to Middle-East threat actors, whose interests allegedly align with those of the Palestinians (meaning anti-Israeli or supporting intra-Palestinian goals). Some have stated that three of them, namely Molerats, APT-C-23 and the group behind Operation Parliament, are subdivisions of Hamas’ cyberwarfare division also known as Gaza Cybergang. Some suggested that Iran is also involved in the operations or support of these groups. Since October 7, several cyberthreats against Israeli entities by those groups were reported (with some activity preceding the war): a new variant of the SysJoker backdoor, an initial access downloader named IronWind, a Linux wiper named “BiBi-Linux Wiper”, and a Pierogi++ backdoor malware.
While all of the above suggests that Hamas does have cyber capabilities, it is worth remembering that it is backed by Iran (that operates notorious APT groups), and that other “hacktivist” campaigns also joined in on the “fun” such as pro-Russian Killnet and Anonymous Sudan. So, the threat is not only stemming from Hamas.
What Types of Cyber Activities Do You See Related to the War?
Aside from the attacks reported by different cybersecurity researchers in the aftermath of an observed campaign, such as the ones above, KELA monitors claims by various hacktivist groups that are mostly advertised over a myriad of Telegram channels, as well as on the X (formerly Twitter) network through proof screenshots, claims of attacks, threats to attack and planned attacks.
The activities perpetrated by pro-Palestinian hacktivist groups and campaigns active in the Hamas-Israel war fall into the categories of different cyber attacks with varying levels of complexity. KELA observed website defacements, DDoS campaigns, claims of breaching of servers and databases, leaking of documents deemed sensitive for the victim, and doxxing of individuals. We also observed claimed hacking of components made by Israeli companies, such as Unitronics water pump system. Some tampering with mobile alert systems of missiles such as the Red Alert app was claimed in the beginning of the war, with some glitches experienced by Israeli citizens. We also observed alleged Israeli attacks on organizations and facilities in Iran, Gaza and pro-Hamas telegram channels. Alongside those, disinformation campaigns in the Hamas-Israel war is reported to be one of the highest in modern history. While not a cyber attack per-se, it is used to exert psychological influence in addition to dispersing misinformation about the targeted sides.
Will I be Targeted if My Company is not Located in Israel? Does it Matter Where I Operate?
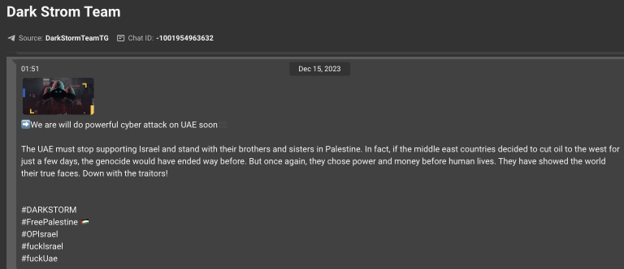
As mentioned earlier, while much of the targeting and attacks falls onto companies and organizations (governmental, military) in the war-participating sides, KELA also observed significant targeting of third parties, especially if those are involved in the support of the opposing side. As such, we have seen the targeting of UAE-based organizations on the basis of a claim that UAE is not supporting its Muslim brothers in Palestine but instead is working with Israel; targeting Indian organizations and companies due to the Indian government standing with Israel and others.
A pro-Palestinian hacktivist group Dark Storm Team claims to target UAE (screenshot via KELA platform)
Unfortunately, geopolitical conflicts are now spilling outside of the direct sides they involve and companies in countries that publicly express support for Israel (with the US being the biggest partner and supporter) might become a target. Moreover, as we mentioned – some attacks targeted components manufactured by Israeli companies (for example, in the Unitronics water pump system), so a supply chain risk gets a somewhat new meaning here. Companies might get affected even without being directly targeted.
How Can I Protect my Company from Those Types of Attacks?
This is perhaps the most important question you can ask after understanding that you might become a victim. Below are a few suggestions:
- Monitor: a cybercrime intelligence platform like KELA’s alongside additional monitoring capabilities will help to detect whether anyone is targeting your company or yourself. You can also familiarize yourself with the recent TTPs of the threat actors and what are they talking about.
- Invest in DDoS protection solutions and make sure they guard against the changing threat landscape in this area.
- Make sure that all of your attack surface, privileged accesses and databases are accounted for, protection wise, and implement needed restrictions and tools to prevent threat actors from getting access to your data. Make sure MFA is implemented on all sensitive assets.
- Employee education: phishing emails are always a threat, but in times of war, they even more get tailored to companies, organizations and many times contain lure themes related to the war. Social engineering is another threat, and clicking on any kind of link you shouldn’t receive is always a big no-no! Employees should be very cautious and verify each sensitive request with the real person at the company.
- And just a general note on spread of misinformation – don’t blindly share everything you see. Verify for yourself – or just don’t share if you’re not sure!
Get notified about threats targeting your organization in real-time. Try KELA’s Cyber Threat Intelligence Platform for Free.