DarkForums Chronicles: A Look into the Forum's Leadership
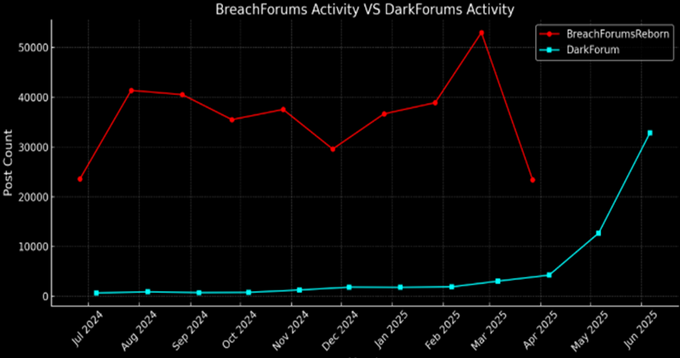
DarkForums, originally launched as "DARK4RMY Forums" in 2022, has skyrocketed in activity, with a 600% surge in activity between April 1 and June 30, 2025. It swiftly absorbed much of BreachForums' user base, adopting its design and expanding its reach. Now operated by the administrators AnonOne and Knox, DarkForums has evolved into a major hub for data leaks, malware distribution, and hacking tools.
Published July 23, 2025

No time to read? Listen here:
When BreachForums' administrators were arrested in April 2025, a significant gap in the cybercrime world was left in their wake, one quickly filled by DarkForums. The platform, originally launched as "DARK4RMY Forums" in 2022, has skyrocketed in activity, with a 600% surge in activity between April 1 and June 30, 2025. Stepping in to claim the throne, DarkForums swiftly absorbed much of BreachForums' user base, adopting its design and expanding its reach. Now operated by the administrators AnonOne and Knox, DarkForums has evolved into a major hub for data leaks, malware distribution, and hacking tools.
The full report, including exclusive and full details not covered in this blog, is available to KELA customers upon request.
Background
In July 2025, following the arrest of BreachForums’ suspected administrators by France’s Cybercrime Brigade, the cybercrime scene shifted toward DarkForums, despite the presence of other established forums like XSS, Exploit, and Leakbase. Launched in 2022, DarkForums rapidly transformed into the successor, absorbing some of BreachForums’ user base and activity. As BreachForums went offline without the usual FBI banner in April 2025 and fake revival sites emerged, DarkForums filled the void, expanding into a major hub for data leaks, malware trade, and hacking tools. It adopted a tiered membership model and exclusive Telegram groups, including BreachForum’s Telegram group, and its design was revamped to mirror BreachForums. The forum, operated currently by admins AnonOne and Knox, was once related to a hacking group called “D4rk4rmy” (DarkArmy). In this blog, KELA analyzes the individuals behind DarkForums.
DarkForums Emergence
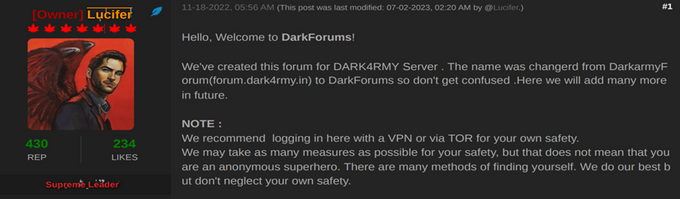
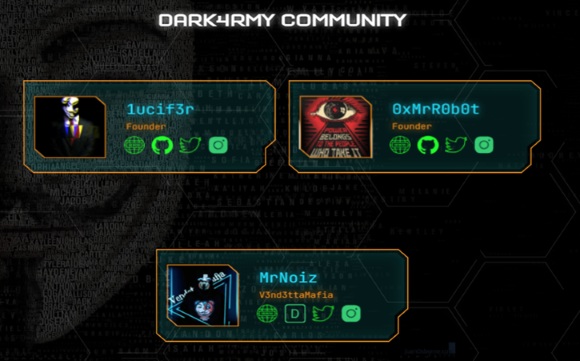
In one of the earliest posts on the forum from November 2022, the user “Lucifer”, one of the site’s original owners, revealed that the platform began as “DARK4RMY Forums”, created for a group called DarkArmy, before being rebranded as DarkForums. The post mentioned the initial domain (forum.dark4rmy[.]in), and later darkforums[.]in. During its early phase, the forum was run by Lucifer (1ucif3r) and MrRobot, with AnonOne as administrator and moderators including Scrap, RKSAINI, MrNoiz, and Jigsaw. However, this original leadership phase was short-lived, as Lucifer and AnonOne remained. Unlike the operators of BreachForums, these individuals appear to lack sophistication, display weak operational security, and are not believed to be major hackers themselves. In addition, the DarkForums also suffered from a data leak that exposed most of its userbase in 2023.
The DarkArmy Group
The roots of the forums were found to be related to the DarkArmy group. The dark4rmy[.]in website, launched in March 2022 and using an Indian domain, represents a self-described white-hat hacking community active on Discord, Telegram, and a dedicated forum. The group was led by Lucifer (1ucif3r) and MrR0b0t (also known as 0xMrR0b0t), who acted as the founders and main operators, while MrNoiz, linked to another group called V3nd3ttaMafia, served as a moderator. Their online infrastructure included a chat portal, a now-inactive GitHub profile listing hacking tools attributed to Lucifer, and an associated Microsoft account under the name “LUCI FER.” OSINT revealed additional email addresses linked to the group, such as d4rk4rmy18@gmail.com and d4rk4rmyofficial@protonmail.com, the latter appearing in the 2023 DarkForums data leak as “Forum Bot.”
DarkForums Admins
Lucifer, AnonOne and Knox
The founder of DarkForums, Lucifer, active since at least late 2022, presented himself as a “student, programmer, and ethical hacker” based in India on the archives of his GitHub profile. His primary role was managing the forum and sharing a wide range of leaked databases, hacking tools, and educational materials, mostly reposted from other threat actors rather than original hacks. His digital footprint was extensive, spanning inactive websites, archived GitHub repositories, and multiple social media profiles, many now defunct but preserved via web archives.
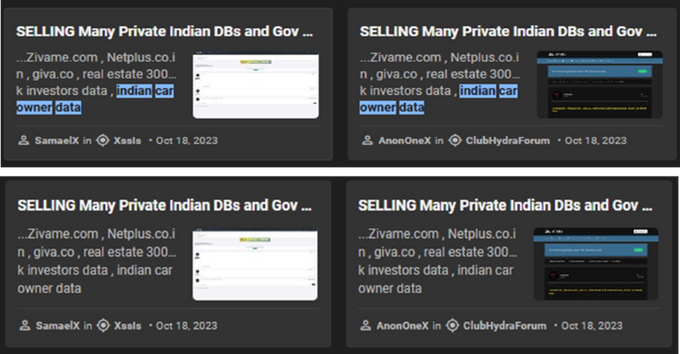
Through careful OSINT analysis, KELA traced his identity to an individual based in the city of Balangir, India. His various emails and usernames, such as "0x1ucif3r," "iamBOTXD", and "SamaelX", appeared across DarkForums, BreachForums, XSS, and other underground platforms. Despite his early prominence, his activity on the forum allegedly ended after he declared his retirement in August 2024, transferring the admin role to a user named “Knox”.
Another early administrator emerged around the forum’s launch during its DarkArmy phase, operating under a moniker evocative of the Anonymous group, is “AnonOne”. This individual was far less active on the forum’s Telegram groups, posting only a handful of messages. His presence spanned multiple forums based on shared contacts, including HydraMarket and BreachForums, where he used a variety of aliases such as “Alexa69”, “YourAnonOne”, “HumanError”, “Xolo666”, “LostSec”, and “FlashLethal.”
The activity patterns of “Lucifer” and “AnonOne” strongly suggest a connection between the two accounts. Lucifer maintained consistent activity from late 2022 through August 2024, with particularly high engagement during 2023. After Lucifer ceased posting, AnonOne’s activity increased a bit, extending into 2025. Notably, their most active periods between the two never overlapped. Both accounts frequently posted nearly identical content in multiple forums, including greetings, pointing to either direct content reuse or coordinated messaging. Moreover, emails and the analysis of the DarkForum leak indicate a potential connection between the two, with several possible connected email addresses, as detailed in KELA’s full report.
Although this evidence does not definitively prove they are the same person, KELA’s analysis suggests that AnonOne was possibly a constructed persona created by the forum’s administration to boost credibility and public image, However, this has not been confirmed.
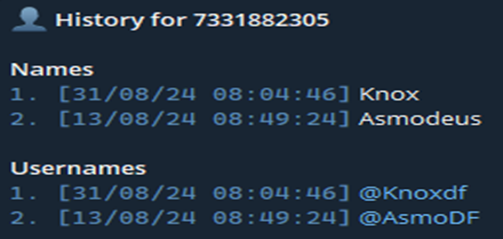
In 2024, a new figure called Knox assumed ownership of DarkForums after Lucifer resigned. This individual uses several encrypted messaging platforms and opened an X account in August 2024. Their activity on the forum largely mirrors that of past administrators, focusing on reposting data breaches from other sources rather than original content. Moreover, they registered on the forum in mid-2023 under the username “admin”, a few days after the forum’s leak, and made only one post in 2023 before reappearing more actively shortly after Lucifer stepped down in 2024.
The timing, usernames, and thematic branding suggest this new identity may be a rebranding effort, possibly representing previous owners under a different persona or a close associate created as a contingency following the forum’s breach. In addition, KELA noticed that his former username was “Asmodeus”, which is connected to the Lucifer TV show and mythology. It is important to note that there are unconfirmed claims suggesting this person may be from Indonesia. Some sources on the dark web link them to various aliases and activity across multiple platforms, but no solid evidence supports these claims as of now.
MrNoiz and MrR0b0t
Originating from India, MrR0b0t was one of the initial administrators of DarkForums and was tied to multiple online identities and platforms, based on the archives of the DarkArmy website. His digital footprint included Instagram, GitHub, and X accounts, and emails found in both GitHub commits and a leaked DarkForums database led to further OSINT discoveries. These included profiles on HackerRank, Fiverr, Docker, and others, as well as a real name and phone number associated with a location in Haryana, India. While once active on the forum and known for reposting breached content, his role diminished over time, and it's unclear if he remains involved under other aliases.
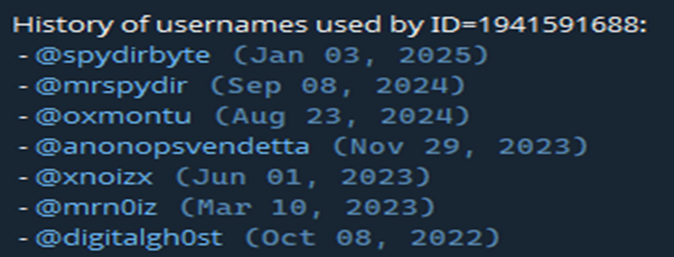
MrNoiz was another early staff member of the forum and the group, this time from the United States, and began as a moderator on both DarkForums and the DarkArmy group. His online activity largely revolved around selling custom hacking tools, and he used handles across platforms like GitHub, ClapperApp, Vimeo, and TikTok. OSINT links tied him to a new alias, “SPYDIR”, which appeared on Telegram, Instagram, and DarkForums, confirming a transition in his digital identity. Analysis of credentials leaked via infostealer logs further revealed a likely real identity: an individual from California infected with Raccoon malware, whose device exposed over 100 accounts.
Conclusion
KELA's analysis reveals that DarkForums' operators lack the sophistication of their BreachForums predecessors, functioning primarily as content aggregators rather than original threat actors. The extensive digital footprints and operational security failures of administrators like Lucifer, AnonOne, and Knox, combined with evidence of potential persona management, indicate that while DarkForums represents a less mature threat, its growing influence in the cybercrime landscape warrants continued monitoring.
As the cybercrime ecosystem continues to shift with emerging forums and operators, understanding the threat actors becomes increasingly important for cybersecurity professionals. Identifying and tracking the digital footprints, behaviors, and affiliations of these individuals can help organizations stay one step ahead in the fight against cybercrime.
With KELA's Threat Actor module, security teams can gain a more comprehensive view of the actors behind platforms like DarkForums. By consolidating data from multiple sources including regions, sectors, IOCs, and mapping to the MITRE framework, it provides deeper insights into the motivations, tactics, and connections of these cybercriminals. (You can try Threat Actor for free!)
KELA’s full report is available to customers and includes more details on the timeline and member activity. For non-customers, contact KELA to access the complete DarkForums Chronicles and get proactive with your cyber defense strategy.