The Handala Hack: Telegram Breach of Israeli Officials
Handala targeted Israeli officials by compromising Telegram accounts - not devices - likely through session hijacking and social engineering . The incident exposes critical vulnerabilities in session management, requiring stronger defenses like Multi-Factor Authentication .
Updated January 1, 2026

The Attack: Handala Targets Israeli Officials (Bennett & Braverman)
In December 2025, Iranian linked hacking group Handala claimed to have fully compromised the mobile devices of two prominent Israeli political figures. However, KELA's analysis reveals the breaches were limited to Telegram accounts only, not complete phone access.
The first target was former Prime Minister Naftali Bennett in "Operation Octopus." Handala claimed to have hacked his iPhone 13, releasing contact lists, photos, videos, and approximately 1,900 chat conversations. The leaked materials included contact information for senior Israeli officials, journalists, and business executives. Bennett initially denied the breach but later confirmed unauthorized Telegram access while stating his phone remained secure.
Shortly after, Handala claimed to have breached Tzachi Braverman's iPhone, Netanyahu's Chief of Staff. The group alleged possession of encrypted communications, financial records, and corruption evidence, threatening to expose materials tied to political scandals. Published data included contact lists of senior officials, videos from public events, and unclassified documents. The Prime Minister's Office denied the breach.
KELA's technical analysis revealed most "chat conversations" were empty contact cards auto generated by Telegram during synchronization. Only approximately 40 contained actual messages, with even fewer showing substantial exchanges. All contacts were linked to active Telegram accounts, confirming the data originated from Telegram itself rather than the underlying devices.
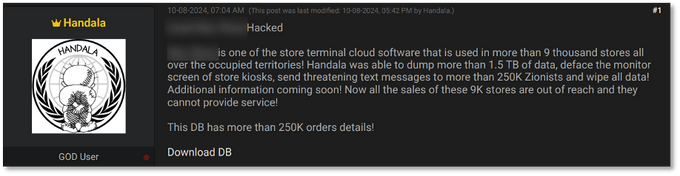
Some of the leaked data by Handala
Actor Profile: Who Is the Handala Hacking Group?
The group first emerged in December 2023, named after an Arabic comic character, and had an active presence across several cybercrime forums. According to KELA's data lake, Handala posted approximately 140 posts across platforms including BreachForums, Ramp, and Exploit during this period. The group also operated multiple Telegram channels and Twitter profiles that were repeatedly shut down and reopened under new names. Handala also used Tox for secure communications and leveraged various defacement platforms to attack websites, while also running their own site to publish breached data. Their operations focused mainly on Israeli companies and organizations, and the group consistently demonstrated support for Iran and the Palestinian cause throughout their campaigns.
Most of Handala’s observed operations rely on phishing campaigns that impersonate trusted vendors, deceiving targets into installing malicious software or fake updates. These high credibility lures are used to deploy wipers and infostealers capable of compromising both Windows and Linux systems. Additionally, the group has leveraged Telegram as a C2 channel, exfiltrating victim data directly to private Telegram channels under their control.
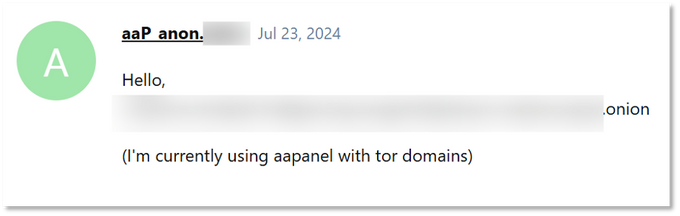
Based on KELA’s OSINT research, the group has used multiple email providers, including ProtonMail, and Outlook. Although their websites were taken offline several times by hosting providers, KELA observed that the initial domain was registered under the name “Roxie Collins”. The group’s sites ran on WordPress and, at times, left administrative login pages exposed, revealing a primary user account, “vie6c”, responsible for operating the site. Additionally, the group appeared to struggle with maintaining its Tor onion service and was observed seeking assistance through the aaPanel platform.
Based on a research by the Iranian blogger, Nariman Gharib, Handala appears to operate as one of several affiliated fronts within an Iran’s cyber ecosystem linked to the Ministry of Intelligence (MOIS). Open reporting associates Handala with the cyber group Banished Kitten, alongside related brands such as Karma Below and Homeland Justice, which are used to leak data and amplify psychological impact. On August 2025, the identity of some members of Hanalda has been exposed by Iran International TV.
Modus Operandi: How Handala Breaches Telegram Accounts
The following compendium outlines the diverse array of sophisticated tactics and exploitation methods currently employed by threat actors to compromise and hijack Telegram accounts.
SIM Swapping and SS7 Protocol Exploits
A SIM swap allows an attacker to assume control of the victim's phone number and receive Telegram login codes without accessing the physical device. Additionally, sophisticated attackers can exploit SS7 protocol vulnerabilities in telecommunications infrastructure to intercept SMS messages at the network level without needing SIM swaps or carrier cooperation.
Multi Vector OTP Harvesting and Telegram Account Takeover
Attackers can combine multiple OTP harvesting techniques to take over Telegram accounts without compromising the device itself, including triggering verification via voice calls and extracting the one time code from voicemail by abusing unchanged default PINs, impersonating Telegram support or trusted contacts to socially engineer victims or their staff into disclosing login codes under urgency or authority pretexts, and operating Telegram bots or third party services that masquerade as security or verification tools to directly capture OTPs and immediately reuse them to authorize new sessions.
Phishing via Fake Telegram Login Pages and QR Code Exploitation
Attackers use phishing pages that mimic Telegram's official login interfaces to capture phone numbers and one time codes. Additionally, malicious QR codes can be presented through phishing or fake "security audits" that, when scanned, instantly establish an authenticated session on an attacker controlled device without requiring SMS codes.
Absence or Weakness of MFA
Telegram’s cloud password is optional and not enabled by default. If disabled, possession of an OTP alone is sufficient for full account access. Even when enabled, the password may be compromised through phishing, keylogging, social engineering, or password reuse from leaked databases.
Session Hijacking via Telegram Desktop and the tdata Folder
Telegram Desktop stores active authentication material in the tdata folder (Telegram Desktop session files), which grants full account access when copied. If obtained from a compromised laptop, shared workstation, or cloud synced directory, an attacker can restore the session elsewhere without triggering OTP or MFA challenges.
Compromise of Cloud Synced or Backed Up Telegram Data
If Telegram data or the tdata directory is included in system backups or synchronized via cloud storage (such as iCloud or institutional backup systems), unauthorized access to those backups enables account takeover. This vector exists outside Telegram's security perimeter and leaves no traces within Telegram itself.
Malware, Custom Clients, and Device Compromise
Targeted malware can capture Telegram session data, log keystrokes, or exfiltrate the tdata folder. Custom or infected Telegram clients disguised as enhanced versions can silently steal OTPs, session tokens, and messages. Compromised secondary devices or workstations used by associated personnel remain plausible vectors.
Exploitation of Known and Unknown Telegram Vulnerabilities
Telegram has addressed historical CVEs affecting session handling, local data exposure, and media parsing. One such example is CVE-2024-7014, where malware was disguised as legitimate video files. While these don't enable silent takeovers alone, chaining them with weak operational security reduces effort. Additionally, Handala may have access to undisclosed zero day vulnerabilities or bespoke exploits enabling stealthy access.
Is Telegram Safe?
Telegram's default settings create significant security gaps. The platform enables tracking through permanent account IDs that persist despite username changes. OSINT bots exploit these IDs to correlate activity across groups, link messages, identify memberships, and sometimes expose phone numbers. Combined with Telegram's open API and third party archiving, this creates extensive profiling opportunities even for privacy conscious users.
Past breaches underscore these concerns: in 2020, a 900MB database containing millions of users' phone numbers and identifiers surfaced on the dark web, while a separate incident exposed 42 million records of Iranian Telegram users via an unsecured database. Additionally, standard chats aren't end-to-end encrypted, they're stored on Telegram's servers as "cloud chats." True encryption requires manually starting a "Secret Chat”, which only works on single devices and can't sync across platforms.
KELA's Assessment of What Happened
Based on the forensic evidence of the leaks, KELA assesses the breach was restricted to Telegram account access only, likely utilizing the same modus operandi observed in Handala's previous campaigns. The most probable attack vectors include social engineering or spear phishing targeting for passwords and OTPs, the exfiltration of Telegram Desktop session files (tdata) from compromised workstations, or unauthorized access to cloud backups. While the scope of the breach was likely exaggerated Handala, the incident highlights the critical need for session management and MFA, even on "secure" messaging apps.