How Scary is that Data Leak, Really? According to Cyber Threat Intelligence, You Might Be Able to Sleep Easy
Published April 7, 2024.

Threat actors — such attention seekers, #amiright? Always coveting the spotlight by doing diabolical deeds like stealing and compromising information, from passwords and usernames to social security numbers, emails and more. Of course, stolen databases are a genuine worry for security teams, as when a stolen database is sold or leaked for free by cybercriminals, attackers can use them to launch attacks or gain a foothold into their organization. So it’s no wonder that when a threat actor claims to have stolen data from a “big name” company, it attracts a whole lot of interest and fear.
But, is there always a reason to be afraid? From false claims and exaggerations, to readily-available data scraped from public sources — here are three reasons you might want to question the next flashy database dump headline.
The Boy Who Cried Database Dump
In March 2024, threat actor Ddarknotevil boasted of a breach of 3,800 customer support users, data belonging to cloud solutions provider, Okta. The attacker claimed to have obtained PII such as user IDs, full names, phone numbers, addresses and more.
As Okta had experienced a security breach in late 2023, this claim was easy to believe, but after KELA analysis, it was thoroughly debunked. Based on analysis of the sample lines which Ddarknotevil shared, it became clear that the database belonged to an alleged database dump from the National Defense Information Sharing and Analysis Center, claimed by the threat actor IntelBroker back in July 2023. The sample lines were identical, and the full list shared for users to download is exactly the same size. Not to mention that Okta later confirmed that it wasn’t their data. All Ddarknotevil had done — was rebrand this data as belonging to Okta. So much for that 782 reputation score.
I Found a Database that was This Big
While it’s easy to have a knee-jerk reaction to news of a database leak, it’s always important to wait for the smoke to clear and see what the real situation is before raising the alarm. In late January, MOAB hit the headlines, which cleverly stands for the Mother of All Breaches. Many media outlets reported this database dump as a leak and a potential threat, the largest of its kind ever reported, with 12TB of information, and containing 26 billion records.
There were many reasons to question this leak:
- There was no evidence that anyone outside of security researcher Bob Diachenko and trusted parties had accessed the dataset.
- The data was unavailable on any cybercrime forums.
- The leaked dataset was mostly information from past breaches such as 360M records from MySpace, 281M from Twitter, and 153M from Adobe.
Despite those facts, the sheer numbers involved struck fear into the hearts of many CISOs.
However, it’s worth having all your information before you panic too much. Just days later, data breach search engine service, Leak-Lookup, confirmed that they owned the misconfigured server that contains the MOAB dataset, secured the server, and reiterated that there was no threat actor involved at all. Mother of All Blunders, eh?
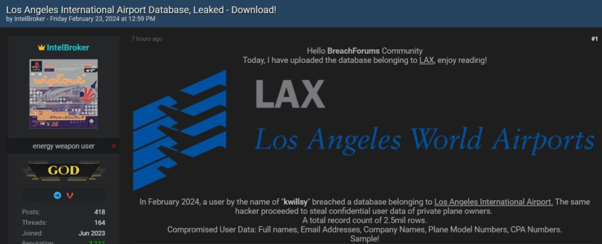
Believe it or not, even when a real attacker is involved — you can’t always trust your initial instincts. In February, IntelBroker claimed responsibility for a breach against the Los Angeles International Airport. IntelBroker said they obtained a total record count of 2.5million lines of sensitive data belonging to private plane owners.
When KELA took a closer look however, we found the leak exposed roughly 16,600 unique email-containing records, and the 2.5M number was related to the lines, not the number of sensitive records containing all the data that was initially claimed by the actor.
We Knew That Already
Finally, when a database dump attracts attention, it’s always worth checking to see if it’s actually a scraped database, presented as a breach of new stolen data, but actually taken from publicly-available sources.
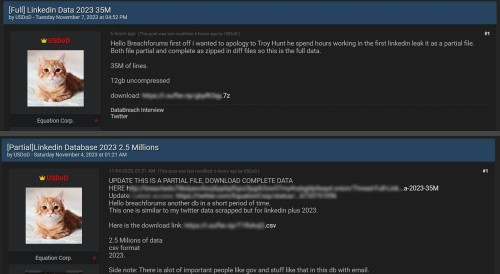
In November 2023, user USDoD leaked a database on BreachForums which they claimed to include 12GB of data over 35M lines. In reality, this appears to be scraped information from publicly available LinkedIn profiles, as well as email addresses which seem to be fabricated entirely, using a specific format.
Scrapers can be difficult or impossible to distinguish from legitimate user traffic, making scraped data an ongoing problem. Back in 2021, 700M LinkedIn records were offered for sale after a scraping incident where KELA uncovered data was obtained via an API offered by search company GrowthGenius.
While scraped data dumps do not signal a breach or a leak, scraped information can still present a risk, infringing user’s privacy rights, and violating the terms of service of websites or social networks.
The Real Deal: Identifying Database Dumps that are Cause for Concern
Database dumps can be alarming, especially as media outlets need to report information in the moment, and information about data breaches usually evolve and deepen over a matter of days or even weeks. Top tips to stay informed include:
- Don’t believe everything you read: Media outlets get eyes on their content with exciting headlines and big numbers. Always question what you see, and practice trust but verify with a respected third party.
- Monitor cybercrime forums: Cybercriminals often buy stolen credentials on cybercrime forums. By keeping visibility into threat actors’ activities, you can stay aware of evolving threats.
- Onboard threat intelligence: A threat intelligence platform enables security teams to gain profound insights into the tactics, techniques, and procedures (TTPs) employed by threat actors, so you know what to look for.
Looking to boost your threat intelligence so you aren’t taken for a ride by threat actors looking for attention? Request a Free Trial of KELA’s Cyber Threat Intelligence Platform.