Is GDLockerSec Really Targeting AWS?
Published January 27, 2025.

Background
In January 2025, a new alleged ransomware group named GDLockerSec emerged, sharing details of a few victims on their website. Interestingly, the group made the bold claim of targeting a high-value entity, Amazon’s AWS. KELA has investigated this assertion.
Who is GDLockerSec?
Emerging in January 2025, the group appears to operate as a ransomware organization, featuring an onion website and a Tox chat ID, similar to the methods used by major ransomware groups. Previously known as “GhostSec-Devil”, the name hints at a potential connection to the GhostSec team and the GhostLocker ransomware. However, no evidence currently supports this link.
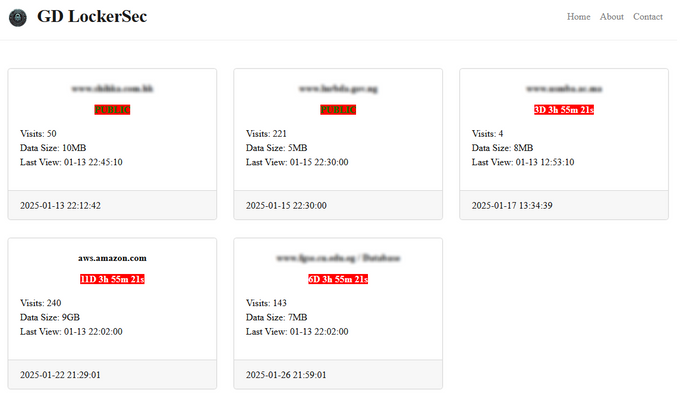
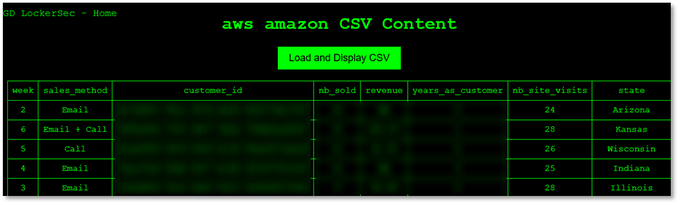
The design of their website seems heavily influenced by the infamous RansomHub ransomware group, with the “About” section replicating phrases directly from the RansomHub website. The group has published four full victim data dumps, Each file is under 10MB, which is relatively small for typical ransomware operations, originating from Hong Kong, Nigeria, and Morocco, with some published before on cybercrime forums by different users. Their fourth alleged victim is notably more high-profile: Amazon’s AWS services. The group claims this dataset, scheduled for release in a couple of days, is their largest yet at 9GB. While relatively small for such a claim, they have provided a downloadable CSV sample to substantiate their claim. As investigated by KELA, the CSV sample is public and is not related to sensitive data owned by AWS (see the analysis below).
The group operates on X and Telegram, with a small Telegram following of around 100 subscribers sharing database dumps. Their channel appears to have support from “Bjorka,” the alleged Indonesian hacker, though it’s unclear if it’s the real Bjorka or an impersonator. On X, the group uses the handle @SGaming66355, registered in April 2024. Early posts were deleted, suggesting the account may have originally been for personal use before being repurposed. A BreachForums account for the group’s name exists as well, however without any messages.
The group’s ransomware website
OSINT Traces
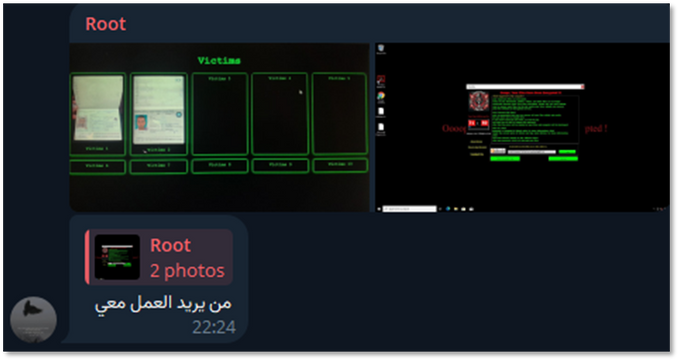
Using KELA’s platform to search for Telegram messages, KELA identified a user associated with this group (@Admfudhsvdg, ID 6527700340) who actively promoted the group on various Telegram groups related to data breaches and previously used the username @GDLockerSec. Analysis of Telegram tools revealed that this user also operated under various usernames and aliases, including @vfsstart, @Bodasec, @vth3darkly, @tradervalide and @ghostsadmines. Additionally, the individual adopted multiple profile names such as “Root”, “tt_signal”, “th3darkly”, “Anonyme GHOST” and, nearly two years ago, used the name “Amin” (Surname was redacted by KELA), which could potentially be their real identity.
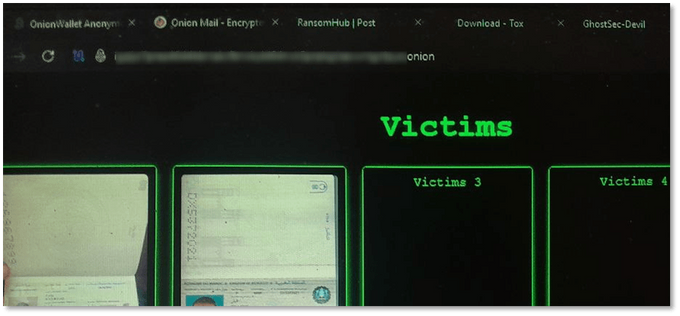
@Admfudhsvdg Looking for partners involved with the ‘GhostSec-Devil’ onion site screenshot, identical to the same address as GDLockerSec, and with an open tab for RansomHub ransomware
Postings identified by this user revealed two additional Telegram accounts associated with the group. The first, @GDLockerSec (ID 8116056430), previously used the usernames @vulneralockersec and @m012ll and had the profile name “VulneralLockerSec”. The second, @ronablox (ID 7165377444), formerly operated under the usernames @freemasonry30 and @livarisx, with profile names including “GhostSec”, “DarkSpider”, and “Adam” (surname redacted by KELA). As evident, the group’s members frequently change their aliases and usernames.
All three users are actively involved in various communities and groups reflecting their interests in cybersecurity, hacking, artificial intelligence, cryptocurrency, and programming. These groups focus on discussions about cyber threats, hacking techniques, and security tools such as Kali Linux and WifiSlax, with a notable emphasis on Arab and global hacker communities. They are particularly active in the Moroccan Cyber Army Hackers Telegram chat. Additionally, they shared VirusTotal files in these chats, with telemetry indicating origins in Algeria and Morocco.
Their poor operational security practices were exposed in a Telegram post by one of the members, where a shared screenshot unintentionally revealed a personal Gmail address. Further investigation using reverse OSINT email tools connected the email to an individual named Saad from Morocco. This email was also linked to the management of the @SGaming66355 X account, highlighting a clear example of their careless approach to maintaining anonymity. Additionally, a now-deleted Facebook account called “GD Locker Sec” was discovered in several Arabian Facebook groups, including Moroccan Hackers.
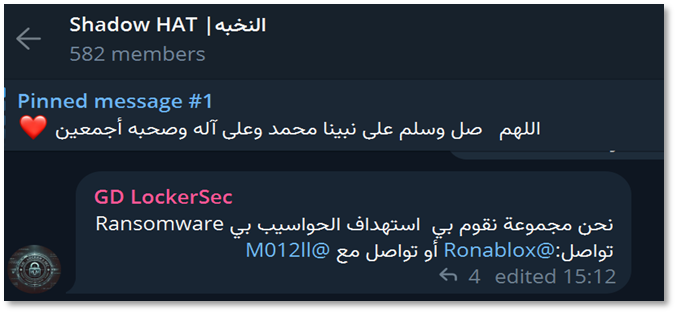
A message that was written in December 2024, translated to: “We are a group that targets computers with Ransomware. Contact: @Ronablox or contact @M012ll”
GDLockerSec inactive Facebook profile found in “Moroccan Hackers” Facebook group
The Truth Behind the AWS leak
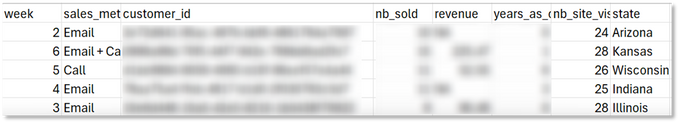
Upon KELA’s review of the data, it has been determined that the data in question originates from an S3 bucket. The dataset appears to be a training set, primarily focused on data science education, and is not connected to AWS beyond being hosted on their platform. Importantly, there is no indication that this dataset constitutes a breach or leak of sensitive data from AWS itself. Furthermore, the same dataset is also publicly available on Kaggle, a well-known data science community platform where such training sets are commonly shared for educational purposes. These findings strongly suggest that the claims linking this data to an AWS security incident or breach are unfounded and not legitimate.
A comparison between the leaked sample file and the open-source file, highlighting their identical content
Bottom Line
KELA’s investigation indicates that GDLockerSec is an amateur group that relies heavily on exaggerated claims to inflate its reputation within the cybercrime ecosystem. The group’s tactics suggest a lack of sophistication, with poor operational security, copying another ransomware website, and unverified claims being a recurring pattern in their activities. Their reliance on self-promotion, rather than verifiable achievements, underscores their struggle to gain legitimacy among more established ransomware groups. Further analysis points to potential ties to both Morocco and Algeria, as inferred from user aliases, messaging activity, and possible geographical indicators linked to the group’s members.