The Initial Access Broker's Toolbox – Remote Monitoring & Management Tools
Updated September 18, 2020.
Conclusion
Update: October 8, 2020: Zoho's statement added
- With the rise of initial access brokers and an increase in threat actors selling remote access to compromised networks, RMMs (remote monitoring and management tools) have become lucrative targets.
- KELA noticed that a cybercriminal active on Russian-speaking forums had recently been selling a lot of access via an RMM tool, and discovered that the RMM tool in question was Zoho’s Desktop Central product – which suggests a threat that organizations face.
- Monitoring what type of network access initial access brokers are selling provides important intelligence for IT and cybersecurity teams defending an organization's network.
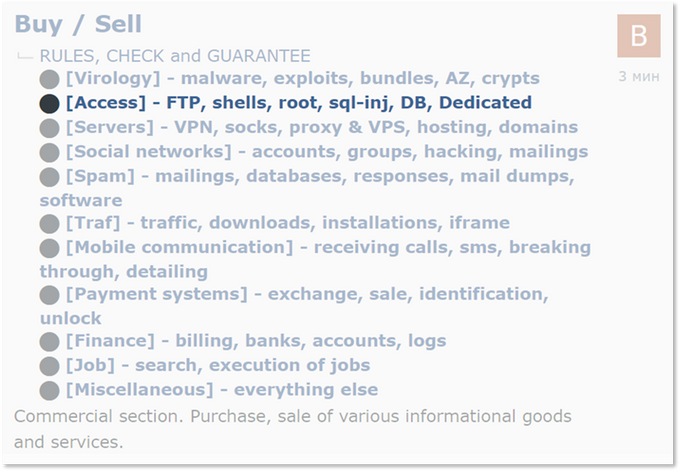
Diverse network access
Remote monitoring and management (RMM) software is a product that helps IT professionals manage networks, allowing them to gain access to multiple machines and escalate privileges. As you can imagine, this type of access is very attractive to malicious actors. As a result, managed service providers (MSPs), which are the driving force in the use of RMM, continue to be targeted by ransomware actors . KELA has recently noticed that some initial access brokers are targeting RMM software, either directly or through MSPs , as part of their unauthorized access portfolio . First , a brief explanation of the term "network access" as used by KELA and threat actors. The term "network access" itself is very broadly defined, and threat actors use it to describe a variety of attack vectors, permission levels, and entry points. A look at a subforum dedicated to buying and selling unauthorized network access on a well-known Russian-speaking forum will give you an intuitive understanding of what "network access" means in the underground.
As can be seen in the diagram above, threat actors use the term “access” to describe multiple attack vectors and techniques, including everything from SQL injection to RDP access. There are also many different types of network access for sale, and each offers different levels of knowledge required to gain access and what the actors can do after gaining persistence. Therefore, different actors may be interested in different types of access for different monetization TTPs . For ransomware gangs, the goal is to steal data or execute malicious scripts across the network, but for actors who are looking to steal personal information, database access is the “king” of chess, and having access to endpoints is useless. This is why credentials for some cloud apps and third-party services are extremely popular products, while other accesses tend to be less interesting . Recently , KELA found a perfect example of how RMM access is becoming part of the ransomware-as-a-service ecosystem. This case illustrates exactly why actors make MSPs a prime target .
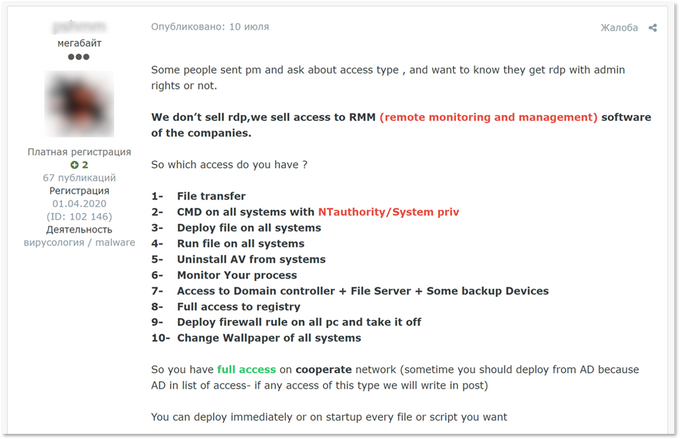
Information from a person with direct knowledge
In September 2020 , a threat actor put 36 accesses up for sale on an underground Russian-speaking forum . The total selling price was $ 98,400 , although some of the accesses were subject to price proposals from potential buyers . The actoralsoput up a dozen accesses for sale in July, bringing the total number of accesses up for sale to 53 , with a total value of$ 153,850 . The actor has alreadysold 10 accesses , with asking price (final price unknown)of $ 33,800.
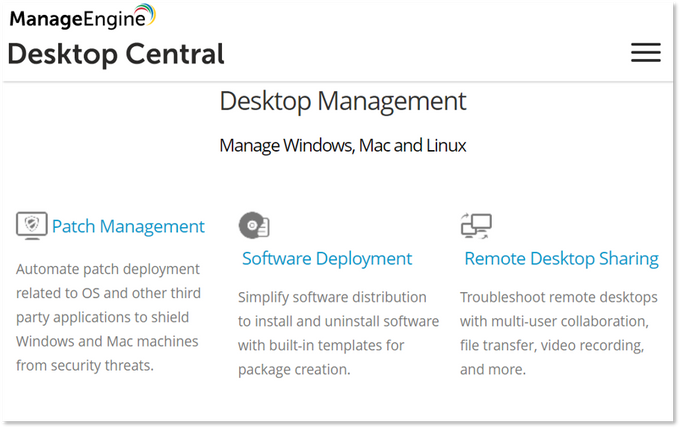
After analyzing multiple posts published by this threat actor, we believe that the targeted RMM software is a ManageEngine product developed by Zoho , specifically Desktop Central . By examining some of the features of Desktop Central, we can understand why it is so attractive to threat actors, especially ransomware gangs. It allows for a variety of actions, including remote control of the host machine, and perhaps most importantly for ransomware gangs, the remote execution of custom scripts against a set of computers and devices at the edge of the network.
Some of Desktop Central's features that may be attractive to ransomware actors (Source: ManageEngine )
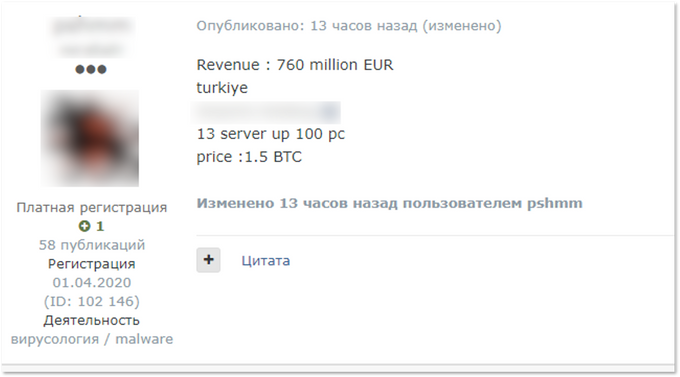
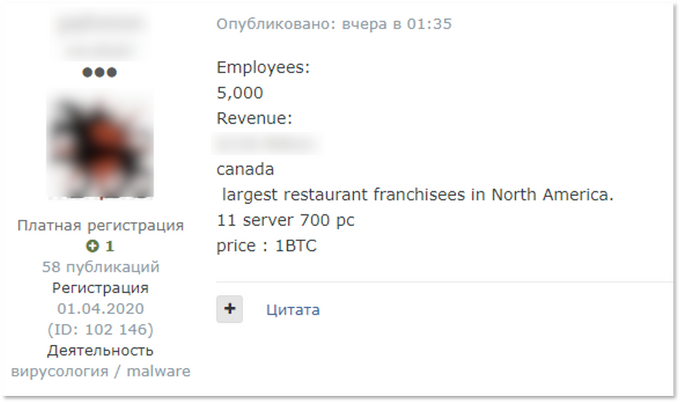
For example, some ransomware types require human interaction to execute Powershell scripts . RMM software allows ransomware to be deployed across a network without the hassle of bypassing pesky Windows protections - a perfect living-off-the-land attack in the cloud. With this in mind, it is easy to see why RMM access is so attractive to ransomware actors. KELA identified victims of the two most expensive accesses sold by the threat actor and indirectly confirmed their use of the software in question. One of the two victims was a Turkish company with $221 million in revenue, and the other was a Canadian company with $338 million in revenue. The price of each access was set at 1.5 BTC for the Turkish company and 1 BTC for the Canadian company, with the Canadian company's sale being completed within a few hours of the sale.
But how?
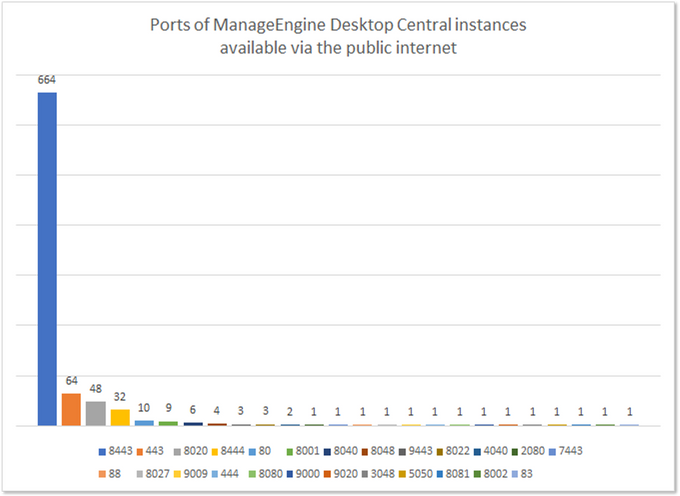
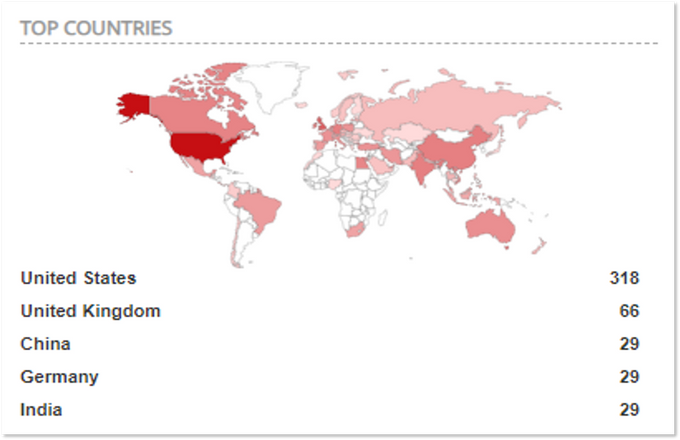
Now that we know that Desktop Central was likely used to provide access to over 30 organizations, the next question is how RMM was compromised. Generally speaking, there are two possible hypotheses: 1. MSP hack: An actor compromised one or more MSPs and gained access to the RMM software installed in the MSPs’ customers’ environments, which gave them direct access to the customers’ (victims’) networks. 2. Direct attack: The targeted organization’s Desktop Central instance was directly compromised using phishing, credential theft, social engineering, or other techniques. To further narrow down the hypotheses, KELA used Shodan to investigate the prevalence of Desktop Central instances on the Internet. At the time of writing, about 900 servers use Desktop Central, making this RMM platform a popular target for threat actors. For actors looking to obtain credentials for the cloud version of Desktop Central, it’s a sure bet.
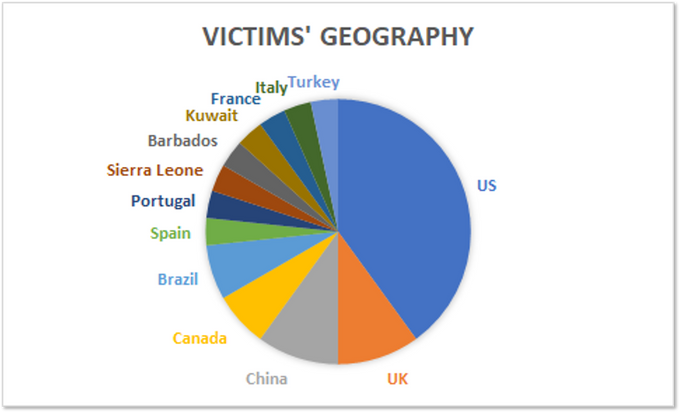
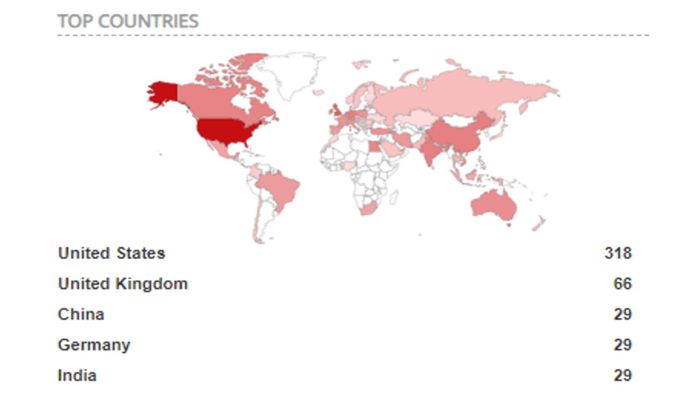
Based on publicly available data, we verified the victim profile, and while the majority of the victims were based in the United States, the attacks were widespread and geographically diverse . As the actor claimed, the nationalities of the affected companies were the United States, the United Kingdom, Canada, Spain, Brazil, Portugal, and others, and the sectors were IT, education, construction, manufacturing, law, healthcare, and others. The actor also sold access related to government organizations in Arkansas and Barbados. Our intuition is that, given the geographical distribution of the victims, it is unlikely that a single MSP was the victim of a concentrated attack (although it is possible that multiple MSPs were attacked), and it is more likely that the victim organizations were directly attacked or that their instances were directly exploited.
Top 5 countries with Desktop Central instances found online (surveyed via Shodan)
This is not the first time Desktop Central has been targeted. In March 2020, a remote code execution vulnerability (CVE-2020-10189) in the product was reported to have been exploited in attacks designed to install malware . However, the access discussed in this blog is likely unrelated to the remote code execution vulnerability (CVE-2020-10189) as the software was accessed using legitimate credentials. Nevertheless, the fact that Desktop Central has been targeted suggests that threat actors are interested in RMM software as an attack vector.
Update (October 8, 2020): Following this blog and the press , KELA was contacted by Zoho's information security team . We have identified multiple victims based on the threat actor's postings selling RMM access and provided Zoho with information on victims that we believe may be linked to Zoho products . After investigating, Zoho has concluded that the identified victims used weak credentials for their ManageEngine products, which is likely the cause of the compromise. Additionally, the hypothesis that the vulnerability tracked as CVE-2020-10189 may have been used to create shadow accounts or persistent backdoors has been deemed unlikely based on the circumstances of the victims investigated .
The summary of Zoho's investigation response is as follows: Based on the evidence we have seen so far, we strongly suspect that the cause of the attack was the use of weak credentials . Therefore, we have taken the following measures:1. Implementing swift action to address the issue , such as preventing logins using weak credentials in the future2. KELA has issued a security advisory to all customers to ensure that appropriate security measures are taken when installing products . KELA will continue to track the activities of the actors and known victims to better identify the TTPs used in this breach . Regardless of whether the root cause of this breach is indeed weak credentials, as Zoho concluded , or whether spear phishing or other methods of credential theft may have been used, we advise IT and security teams defending organizations' networks to keep in mind that Internet-based applications are certainly attractive to , thus expanding the attack surface on the cloud.