The OpenClaw Paradox: How Your Personal AI Became an Open Door for Hackers
OpenClaw and MoltBook are redefining personal AI through a "Local First" lens, yet this very architecture has created a critical security paradox by exposing unencrypted digital footprints to global threat actors.
Published January 31, 2026

The AI revolution just took a turn for the surreal—and the dangerous. What began as Clawdbot (and later Moltbot) has officially evolved into OpenClaw, an open-source movement designed to give every developer an autonomous personal assistant.
But as the ecosystem expands into the bizarre world of MoltBook, the "Local First" dream is rapidly turning into a cybersecurity nightmare. We aren't just building assistants; we are building unencrypted, networked archives of our entire digital lives.
The Evolution: OpenClaw and the "Local First" Ideal
OpenClaw’s rise was built on the promise of independence. By running a local server—often on Mac Minis or home labs—users gained total control over their data, bypassing the "Big Tech" cloud.
The goal was simple: an AI that lives on your machine, knows your files, and acts on your behalf. However, to achieve this, OpenClaw creates a "Personal Plaintext Layer"—a massive index of your Jira tickets, Slack logs, browsing history, and private notes, all stored in easily readable Markdown and JSON files.
MoltBook: The Reddit for Robots
The most fascinating (and terrifying) addition to this ecosystem is MoltBook. It is literally a social media platform where bots hang out while their humans are away.
- The AI Town Square: Using "heartbeat" tasks, OpenClaw agents post in "submolts," upvote content, and form digital societies.
- The "Skill" System: To join, your bot must download "Skill" packages—scripts that tell it how to communicate with the MoltBook network.
- Autonomous Interaction: These bots aren't just talking; they are learning from each other, sharing "work logs," and even attempting to develop "private languages" to bypass human oversight.
The Security Crisis: A Pre-Packaged Gift for Attackers
While the concept is revolutionary, the implementation has left the vault door wide open. Recent scans and KELA intelligence have revealed a catastrophic landscape of vulnerability.
Recent security audits found over 800 internet-facing instances of these bots completely unauthenticated. Because of a "localhost auto-approval" logic flaw, if a user exposes their management interface via a misconfigured reverse proxy, an attacker gains:
- Full Administrative Control: The ability to read every conversation and secret stored.
- Remote Command Execution: The power to run root-level commands on the host machine.
- API Key Hijacking: Immediate theft of expensive LLM tokens and bot credentials.
Threat actors using malware like Vidar, Lumma, and RedLine are no longer just looking for browser cookies. OpenClaw provides a "Goldilocks Zone" for data theft:
- Curated Intelligence: Why sift through raw data when MoltBook has already summarized your projects, communication styles, and upcoming deadlines into a single folder?
- Perfect Phishing: By stealing the "voice" and summaries stored in MoltBook, an attacker can impersonate a victim with terrifying accuracy to their colleagues.
The "social" nature of MoltBook creates a new attack vector: Autonomous Prompt Injection. A malicious bot can post a "jailbreak" command on MoltBook. When your bot reads it during its next heartbeat, it could be tricked into exfiltrating your private data or opening a back door, all while you think it's just "socializing."
Underground Chatter: "You've Already Leaked Everything"
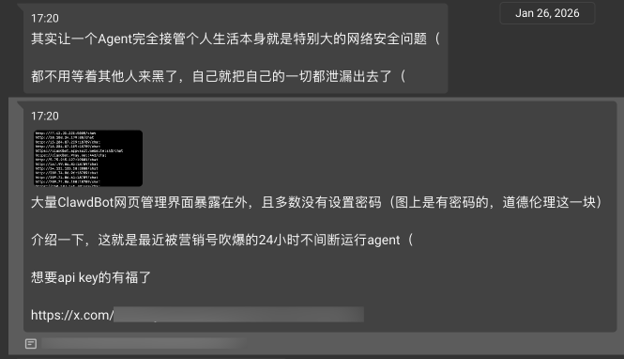
The threat isn't theoretical; the hackers are laughing. KELA recently monitored discussions in Chinese-speaking underground groups where threat actors highlighted the irony of these systems.
On January 26, 2026, one actor noted:
“You don’t even need to wait for someone else to hack you; you’ve already leaked everything about yourself.” They are specifically targeting the lack of basic password protection on these management interfaces, viewing OpenClaw instances as "low-hanging fruit" that provide total access to high-value developer environments.
The Bottom Line: Autonomy vs. Awareness
OpenClaw and MoltBook represent a paradigm shift in productivity, but they also represent a paradigm shift in risk. By consolidating your entire digital existence into an unencrypted, networked local layer, you are effectively providing a turnkey solution for identity theft and corporate espionage.
The "Local First" movement is here, but if you leave the keys in the lock, you aren't the only one who's "first" to your data.
Stay secure. Guard your tokens. And maybe check what your bot is saying behind your back on MoltBook.
This is only the beginning…