Understanding the Infostealer Epidemic in 2025: Highlights from KELA’s 2025 Report
In light of the growing threat posed by infostealer malware and the increasing volume of compromised credentials circulating on cybercrime platforms, KELA undertook an extensive investigation using its proprietary collection of infected machines and information, closely researching approximately 300 victims.
Updated May 5, 2025

Understanding the Infostealer Epidemic in 2025: Highlights from KELA’s 2025 Report
Stolen corporate credentials are one of the highest value commodities in cybercrime, giving attackers access to sensitive organizational assets, and acting as the first step in a wide range of illicit activities. These activities are generally leveraged for financial gain, but can also be used for ideological or strategic motivations. One approach for gathering corporate credentials is infostealer malware — designed to infiltrate systems and steal sensitive data.
In light of the growing threat posed by infostealer malware and the increasing volume of compromised credentials circulating on cybercrime platforms, KELA undertook an extensive investigation using its proprietary collection of infected machines and information, closely researching approximately 300 victims. As commodity infostealer attacks tend to be opportunistic rather than targeting specific individuals, we compiled a dataset of 300 compromised machines containing access to corporate resources, which were infected by infostealer malware between July and August 2024. Together, these machines contain more than 100,000 compromised credentials. For each machine, KELA identified an affected individual based on information contained in the stolen bot.
In this way, our research aims to identify the individuals most vulnerable to these threats, and to uncover common risk profiles and behavioral patterns. The study also provides organizations with practical insights and strategic recommendations to help mitigate the risks associated with infostealers and safeguard corporate credentials against exploitation. You can download the full report here, or keep reading for your highlights.
Forget the Kardashians - Prominent Infostealer Families Who Demand Your Attention
Infostealers are a business like any other — and so market share is an important indicator of how prevalent and successful an infostealer is in today’s threat landscape. KELA has been collecting logs stolen by more than 30 prominent infostealers, with the top three named as:
StealC: StealC is known for its stealth techniques that reduce the chances of triggering security alerts.
Lumma: Lumma is in second place, hitting headlines for innovative distribution techniques such as deceptive CAPTCHA verification pages.
Redline: Commonly delivered via phishing emails, but also distributed via executables or archive files, Redline comes in third place with the bronze.
In 2024 alone, these three families were responsible for 75% of the 4.3 million machines infected by infostealer malware.
Which Department is Most at Risk? Project Management
Attackers are generally opportunistic, and will take whatever corporate credentials they can get. This is the very nature of infostealers, that they can’t specifically choose a target, instead they infect a machine and then can take advantage of whatever is on those compromised machines. With this information, they can see what next steps can be taken for an attack. After all, many organizations have lax security practices or poorly implemented access control — which means any credential could be an open door for initial access. This access can then be escalated through lateral movement across an organization.
When looking at the most popular job role within the researched dataset, there was one department that accounted for 28% of all compromised accounts, and that was project management. Within this department, you can include diverse roles that include technical project managers, digital and innovation staff, IoT services, and SAP operation team lead — to name just a few.
Why project management? Our hypothesis is that employees in this department often have broad system access and use many digital tools for collaboration and communication, so naturally their machines contain multiple credentials to corporate resources and are highly useful to attackers.
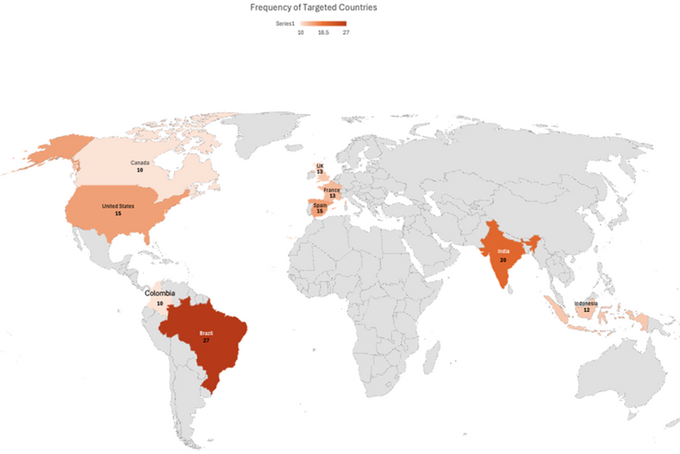
Where are Most Affected Victims Geographically? We Say “Cuidado!”
Interestingly, when KELA looked at where attack victims are based geographically, even the most targeted region — Brazil, was only the home of 9% of attacks. We did however find a concentration of victims in the countries highlighted on the chart below, India, the United States, Spain, France, the United Kingdom and Indonesia.
Outside of this research scope, are you interested in which two countries are the most affected when looking at the millions of infected machines collected during 2024? Brazil took second place, and you can check the report to find out who stole the top spot.
Watch Your Digital Footprint: 14% of Infostealer Malware Infected Technology Companies
It’s no surprise to see Technology as the main sector for infostealer malware and compromised corporate credentials. This area includes high-value targets such as FinTech companies, as well as technology-related fields from computer and network security to cloud services and software development. These are companies where employees are interacting digitally almost all of the time, with dozens of disparate software applications and online accounts. For attackers — what better industry to serve phishing emails, malvertising, or compromised websites to?
Spoiler alert: Rounding off the top three affected sectors, close behind Technology is IT Services at 11%, and Manufacturing at 9%. Four other industries each attract 5% of attacks — can you guess which ones they are?
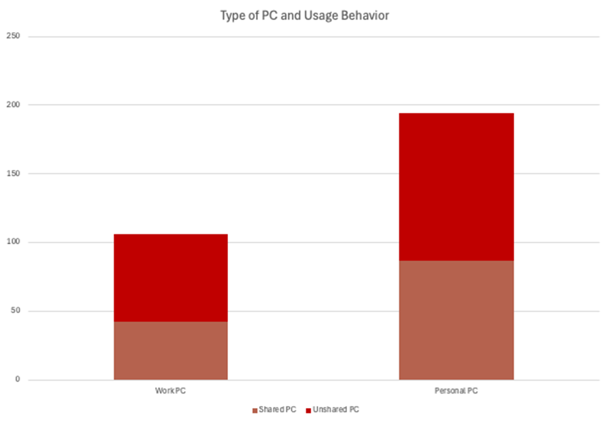
Who’s Watching Netflix With You? Personal Machines are More Likely to be Infected than Work PCs
Through our research, we also wanted to understand how the infections occurred and through which machines. After all, even personal computers have corporate credentials. It turns out, whether your PC is shared with other users or not shared, your personal computer is much more likely to be infected by infostealer malware than your work computer. In fact, according to our research, personal, unshared computers are the most frequently infected category, representing 35.7% of all cases, followed by personal, shared computers at 29%.
Personal computers are in an attacker’s line of sight because:
They tend to lack robust cybersecurity measures that companies enforce in the workplace such as Multi-factor Authentication (MFA).
Users are likely to engage in more risky online behaviors at home than they are in the privacy of their homes.
There is usually no IT oversight or monitoring, including no enforced security updates from a centralized team.
Despite the elevated risk, in today’s hybrid work climate, personal computers are extremely likely to contain corporate work credentials — making this a problem for any organization.
Are Infostealers a Stepping Stone for Ransomware Threat Actors?
Our latest report is packed to the rafters with data on the risk of infostealers in 2025, and also shines a spotlight on the relationship between infostealers and activities by prominent ransomware groups such as Play, Akira and Rhysida.
Download the full report to access unique case studies of KELA observing and analyzing infected machines of businesses who were later claimed as ransomware victims, as well as to learn:
CMS… Business Cloud… VPN… or none of the above: Which sensitive services are of most interest to attackers?
Are founders and CEOs the most at risk? Which job positions are corporate credentials most leveraged for, and does this change across regions?
Remember that guy, what was his name…? KELA uncovers whether most compromised accounts were associated with current or past employees.
We also include seven actionable recommendations to help organizations to ward off the threat of infostealer malware and potential ransomware attacks, covering cybersecurity awareness, device security and access management.
To level-up your own threat intelligence, start your free trial of KELA’s proactive real-time solution here.