XSS Forum After Takedown: DamageLib Emerges
The arrest of XSS[.]is admin “Toha” has shaken the cybercrime underground, sparking mistrust and speculation about law enforcement involvement. Many users have migrated to DamageLib, a rising forum with limited activity but growing membership.
Published September 4, 2025

It’s been just over a month since the dramatic arrest of “Toha,” the alleged administrator of the notorious Russian-language cybercrime forum XSS[.]is. On July 22, 2025, Ukrainian authorities, backed by French police and Europol, claimed a major victory, accusing Toha of profiting over €7 million from ransomware and facilitating trade in malware, stolen data, and illicit access.
Yet the takedown hasn’t silenced the underground. While XSS technically remains online, confusion over who now controls it has fueled suspicion that it could be a law enforcement honeypot. This growing mistrust has driven many cybercriminals to distance themselves from XSS, creating the perfect opening for something new: DamageLib, a rising forum quickly positioning itself as the successor to XSS.
KELA’s Cyber Intelligence Center has tracked this shifting landscape and examined the fractured state of XSS across its onion and clearweb versions, the emergence of DamageLib as a potential replacement, and what these changes mean for the broader cybercriminal ecosystem.
» Strengthen your cybersecurity with KELA's expertise
In this blog, KELA’s Cyber Intelligence Center Covers:
The Arrest of “Toha” – The alleged XSS admin accused of making €7M from ransomware operations, and the ripple effects of his takedown.
New Admin Suspicion – Skepticism over the identity of new XSS admins, low-reputation moderators taking control, and fears that the forum is now a law enforcement honeypot.
Shifting Traffic – Exploit forum traffic surged almost 24% during the XSS turmoil as actors sought alternatives, while XSS visits plummeted.
The Rise of DamageLib – As of August 27, 2025, DamageLib counted 33,487 users—nearly 66% of XSS’s 50,853 members. But engagement lagged: only 248 threads and 3,107 posts in its first month, compared to over 14,400 messages on XSS in the month before the seizure.
Deposit Disputes – Nearly $6M in user deposits remain contested, with partial repayments sparking further mistrust.
Ransomware Rumors – Stallman’s appointment as moderator, speculation about LockBit’s return, and signs XSS may loosen its ransomware ban.
» Understand why you need cyber threat intelligence for your organization
Rewind: XSS Admin Arrested in Ukraine
On July 22, 2025, Ukrainian authorities arrested a 38-year-old man suspected of being the administrator of XSS[.]is, a major Russian-language cybercrime forum. The arrest followed a multi-year investigation led by French authorities, Europol, and Ukrainian law enforcement. XSS, which has been active since 2013 and was formerly known as DaMaGeLaB, has long served as a hub for the trade of stolen data, malware, and ransomware tools, with nearly 50,000 registered users. The forum had a reputation system to facilitate secure transactions and a strict ban on attacking CIS countries.
The arrested individual is widely believed to be "Toha", a central figure in the cybercrime community since 2005, who played a pivotal role in the evolution of several major Russian-speaking forums. “Toha” was a founding member of Hack-All, which later rebranded as Exploit[.]in and they continued to dominate the underground scene when they took over DaMaGeLaB in 2017 after the arrest of its administrator "Ar3s". In 2018, Toha rebranded DaMaGeLaB to XSS[.]is, further cementing their place at the forefront of cybercrime.
Since the arrest, rumors and speculations about Toha's identity and the future of XSS have intensified. Researchers connect this threat actor with the alias “Anton Avdeev”. Nevertheless, there haven’t been any statements from law enforcement so far, probably due to the ongoing investigations and attempts to identify other individuals involved in the forum’s activity.
» Learn how to reduce damage from info-stealing malware
From Suspicion to Migration: The DamageLib Emgergence
While the clearweb XSS domain was seized and shut down, the onion version of the forum remained accessible. As is evident, forum members began to panic-clean their threads and messages, while moderators remained silent. Later, on August 3, 2025, the new admin of the forum claimed that they had successfully transferred all the infrastructure to new servers and launched new clearweb (XSS[.]pro, with the letter “X” now painted in the colors of the Russian flag) and darkweb sites, as they were afraid that the onion website had also been seized. They also stated that the backend of the forums and Jabber servers had not been intercepted.
In the same message, they also claimed that on July 27, 2025, they informed the moderators in a hidden thread about the current status, but the moderators ignored their message. Instead, these moderators launched their own onion-based forum, DamageLib, and sent XSS forum members private messages inviting them to join the new forum and claiming that XSS had been fully seized.
KELA’s review shows that as of August 27, 2025, DamageLib grew dramatically during the first month of its existence and now counts 33,487 users (which makes up almost 66% of the entire XSS user list, and now includes 50,853 registered members). However, current statistics indicate that the users of the newly created DamageLib generated only 248 threads and 3,107 public messages throughout the month. According to KELA’s internal statistics, threat actors demonstrated significantly higher levels of engagement throughout the month prior to the seizure from June 23, 2025, to July 23, 2025, generating over 14,400 public messages. Despite a fast-growing user base, the activity is significantly slower to XSS pre-takedown.
» Learn more: Common threats and vulnerabilities that lead to data breaches
XSS Today: Shifting Leadership and Motivations
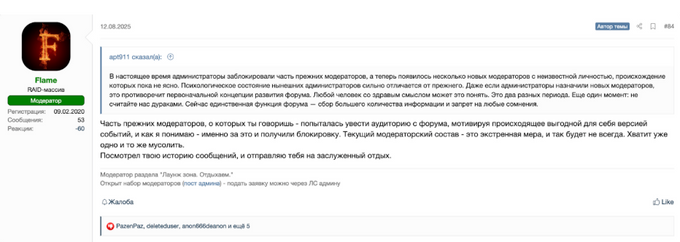
Following their statement, the new admin banned the previous moderators and appointed new ones, “Flame” (registered in 2020, but only 53 messages since), “W3W” (registered on August 4, 2025), and “locative” (registered in 2022, most reputable of the current moderators team), to manage threads and organizational matters while they continued working on the infrastructure. This action raised significant concerns and indignation among forum members, mainly because the new moderators were users with no reputation or recognition, either on the forum itself or outside of it. This triggered a new wave of speculation and discussions among forum members, as the moderators began banning long-time users for concerned posts and negative comments.
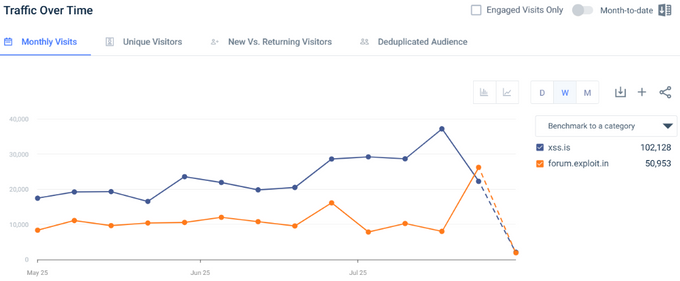
Further on, members began to worry about the lack of activity from old or reputable users (presumably, reputation is based on the presence and amount of reactions), mentioning the presence of only a few, namely “c0d3x”, “lisa99”, “stepany4”, and “proexp”. KELA can confirm that the list of old members participating in discussions is rather short, adding to the names above also “waahoo”, “antikrya”, and “p1r0man.” Additionally, threat actors are discussing where they might go if XSS ultimately falls, mostly naming Exploit (which also raises their concerns as some of the forum members speculated that Exploit can also be a honeypot), RAMP, and Verified forums. According to SimilarWeb statistics, the Exploit forum experienced a significant surge in traffic at the onset of the XSS escalation, with a 23.99% increase in total visits over the course of the month. However, following a peak on July 24, traffic to Exploit began returning to normal levels, while visits to the XSS forum dropped sharply. Notably, users also avoid visiting the clearweb domain XSS[.]pro. It's important to emphasize that these statistics reflect traffic to the clearweb versions of the forums only.
» Learn how to uncover your adversaries with KELA's threat actors hub
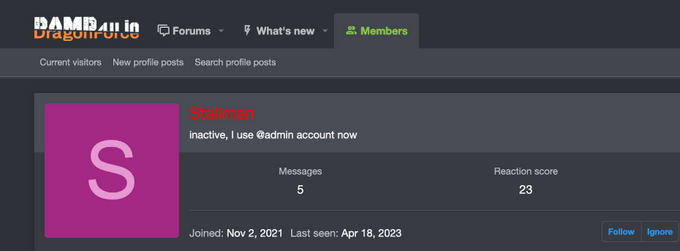
Addressing the situation, the admin decided to add a known member of the community, “Stallman,” to the list of moderators, which also raised concerns among forum users. Stallman, active on various currently existing and previously defunct reputable forums including Exploit, XSS, RAMP (Stallman is an admin on RAMP as well), Rutor, and Runion, mainly specializes in breaches and ransomware, as directly stated in the admin's post from August 18, 2025 (“Stallman de facto leads ransomware community”), and was assigned to manage the sellers and breaches sections. This development raises fresh questions about the new XSS administration and its underlying motivations. Following Stallman’s appointment, several users began calling for the reinstatement of LockBit’s XSS avatar.
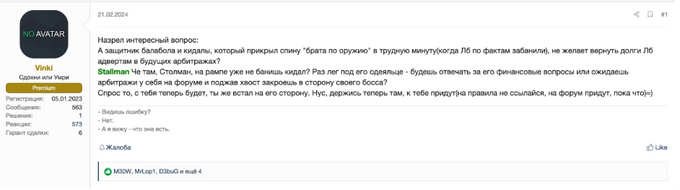
LockBit, a ransomware group, was permanently banned by “Toha” on XSS, which reportedly led to several personal threats made by LockBit against “Toha” and his family. This also overlaps with earlier concerns raised by forum members in February 2024, when they questioned Stallman for not banning LockBit on RAMP, where they serve as admins. Finally, Stallman’s appointment was followed by rumors that the new XSS admin would allow ransomware offers and discussions on XSS, which were previously forbidden. These speculations have neither been confirmed nor denied by the new administration.
» Read more: Ransomware groups are selling network access directly
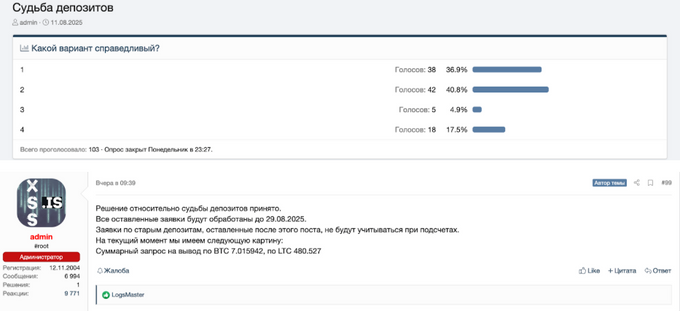
Another hot topic that occupied the community's attention was the status of the deposits (the sums threat actors voluntarily added to their accounts to raise their reputation) and their payment. In a dedicated thread created specifically for this matter, the new admin stated that they did not have enough funds to pay back all the deposits and initiated a poll offering four different options:
- To pay deposits only to those with small amounts, as they might need the money due to their small businesses;
- To calculate an equal percentage for all deposits and pay that percentage to everyone who submitted a withdrawal request;
- To implement the first option with an alternative that includes exchanging the amount for pinned threads;
- To reward those who forgo their deposits with various regalia on the forum.
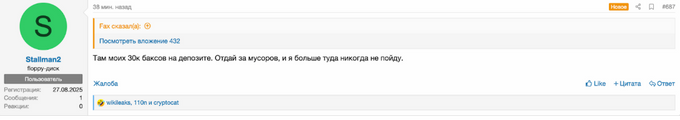
According to KELA’s review, the second option received 40.8% of the votes. The poll has since ended. The admin stated that the total withdrawal requests amount to 7.015942 BTC (788,254 USD) and 480.527 LTC (54,673 USD), which would be distributed among those who requested their deposits back. Additionally, members began discussing that the total deposit debt is estimated at around 50–55 BTC (6,170,873 USD), which they suggest could be considered the cost of the entire forum. It is important to note that Stallman openly confronted this idea, insisting that moderators’ deposits should be withdrawn first before paying the rest.
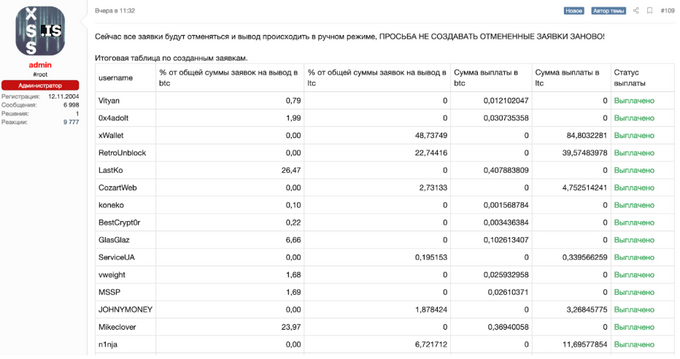
On August 28, 2025, the admin of the forum claimed that they had transferred the percentages of the deposits to those who claimed for withdrawal. Some of the threat actors from the list confirmed in the same thread the arrival of the funds to their wallets.
The marketplace section of XSS remained active through the month, generating new offerings of products and services. However, as mentioned by different forum members in discussion boards with moderators, the new offerings are coming from newly registered and unverified members. Additionally, the offerings targeting CIS countries started to become more frequent and were not being moderated, which also caused discontent among users, as XSS was always known for its strict prohibition of CIS-targeting services.
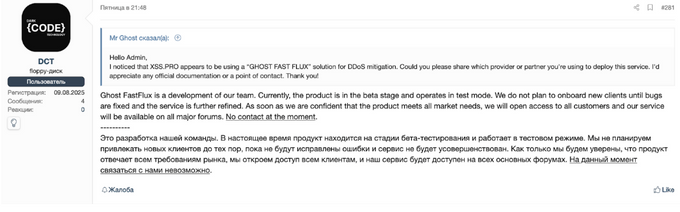
Finally, the new admin mentioned that they are working together with a team named “darkcode.technology”, identified as the developer and provider of the anti-DDoS solution “Ghost FastFlux” for both the new clearweb and onion websites. “Darkcode.technology,” acting on the forum under the moniker “DCT,” claimed that this technology is currently in test mode and may be developed into a product in the future, but is not for sale at the moment.
» Understand what is the role of a threat intelligence analyst
DamageLib Today: Current Status
As previously mentioned, the original moderators of XSS left the forum to launch their own – DamageLib. DamageLib exists only in the onion version; the moderators, including “cryptocat,” “fenix,” “sizeof,” “zen,” “stringray,” “rehub,” and others, claimed they are not planning to support a clearweb version of the forum.
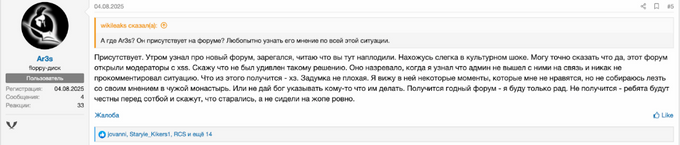
Initially, registration was fully anonymous, and the moderators and admin directly asked new members to avoid using their XSS handles to prevent possible attribution. However, in more recent posts, they stated that they were able to restore user data and created what they called “ghost accounts” to first prevent impersonation of known users, and second, allow those who want to restore their reputation to go through a verification process and regain access to their nicknames. This process, as expected, raised concerns. However, as observed by KELA, a few members, such as “Spy” and “paranoid”, have already restored their nicknames.
» Concerned about the future? See these trends shaping the future of CTI
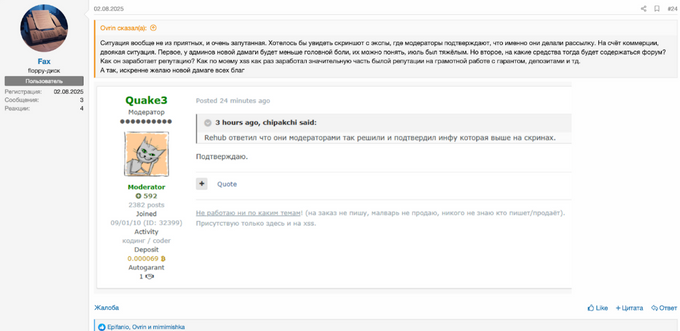
The legitimacy of the moderators and their motivations concerned the newly registered members. In a dedicated thread for discussing forum news, one of the users asked the moderators to send messages from their accounts on Exploit to confirm their identities and the claims they made. On August 2, 2025, the user with the moniker “Fax” stated that the moderator of the Exploit forum, “Quake3”, messaged them confirming that one of the DamageLib moderators, “Rehub”, had verified that the XSS moderators team was indeed behind the launch of the DamageLib forum.
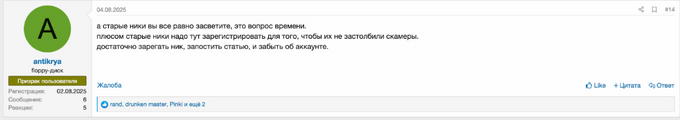
Additionally, KELA observed a few prominent XSS members active on both current XSS and DamageLib forums using their original nicknames, including “antikrya” and “Ar3s” (KELA cannot confirm they are the same threat actors due to a lack of verification on DamFageLib). The latter confirmed that the forum was launched by the former XSS moderators team, while “antikrya” mainly expressed the view that there is no point in hiding nicknames. In addition, Stallman, who operates on DamageLib under the moniker “Stallman2” and registered on August 27, 2025, claimed that they are still active on the XSS[.]pro forum because they want to retrieve their deposit. Notably, they are making aggressive claims that the XSS forum is under police control.
In other posts published by moderators and the admin of DamageLib they claimed that they are considering excluding the commercial section of the forum, as this was a direction “Toha” had considered shortly before their arrest. Finally, the discussion around allowing ransomware-related discussions and offers also took place on DamageLib and received moderately positive feedback from the community.
» Here's everything you need to know about infostealers
Conclusion
Per KELA’s observation, neither XSS PRO nor DamageLib currently hosts substantial discussions or offerings. While XSS PRO is flooded with unverified commercial posts (an issue that at one point led to the introduction of a paid subscription model, which was later abandoned), DamageLib shows limited posting activity overall.
At present, it appears that the communities of both forums, which significantly overlap in user base, are more focused on the status of the platforms themselves, the ongoing investigation, the identities and legitimacy of their respective administrations, and the fate of user deposits. As the situation continues to evolve, KELA will maintain active monitoring to assess further developments and the future trajectory of these forums.
» Get started for free with KELA and strengthen your cybersecurity


![XSS[.]is posts amount from May 23 to July 23](https://entail-assets.com/kelacyber/fit-in/680x456/XSS_posts-1756886558714.png)