From Initial Access to Ransomware Attack – 5 Real Cases Showing the Path from Start to End
Updated February 16, 2022.

Successful ransomware attacks are all alike: they start from unnoticed access to a company’s network. While some attackers get their access in a stealthy way, some use publicly available offerings on cybercrime forums and markets. Part of these offerings is made by Initial Access Brokers who play a crucial role in the ransomware-as-a-service (RaaS) economy. These actors significantly facilitate network intrusions by selling remote access to a computer in a compromised organization (Initial Network Access) and linking opportunistic campaigns with targeted attackers. Ransomware actors are actively looking for network access listings on cybercrime forums to match their ideal ransomware victim.
In this blog, KELA reveals several ransomware attacks that started with network access on sale and led to an attack within a month from the sale offer.
Key Findings:
- KELA managed to identify 10% of victims based on characteristics shared by IABs who usually do not name their victims in order to prevent enterprise defenders from discovering a threat.
- On average, a network access sales cycle takes 1-3 days.
- When bought by a ransomware affiliate or middleman, the access leads to a successful ransomware attack and naming the victim on a blog within 1 month on average.
- At least 5 ransomware operations, most of them managed by Russian-speaking actors, are buying access from IABs and using them in their attacks: LockBit, Avaddon, Darkside, Conti, and KELA describes 5 attacks carried out by these groups that apparently started with a deal with an Initial Access Broker.
How KELA Identifies Network Access Victims
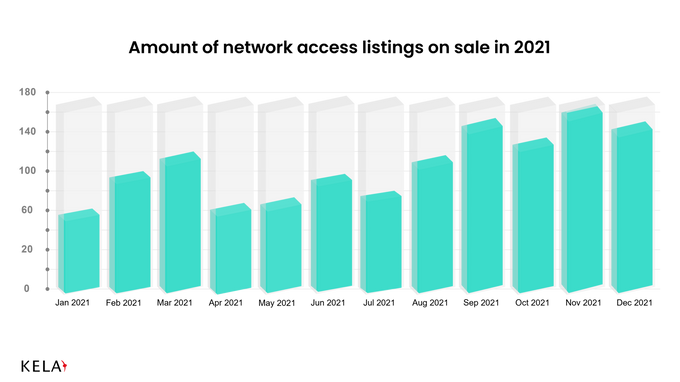
KELA continuously and automatically monitors network access listings on major cybercrime forums, as well as privately communicates with threat actors to receive exclusive offers and insights. Last year, more than 1300 such listings were posted by almost 300 Initial Access Brokers. According to KELA’s research, on average it takes 1-3 days for access to be sold. For USD 500 (the median price for access in 2021, while the average one was USD 4600), a cybercriminal can gain network access and further compromise this victim as they like. In some cases, it means a ransomware attack. But how to connect access on sale to a successful ransomware operation?
IABs rarely name their victim when they offer access for sale – otherwise, security researchers can notify the affected company, helping to identify unauthorized access and close it. Instead, IABs list properties of a compromised company which can include:
- Revenue
- Size (Number of employees)
- Industry
- Description
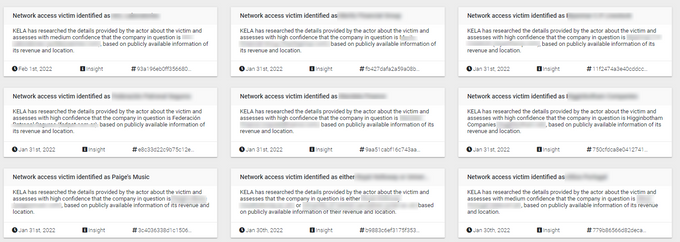
These metrics help other threat actors to understand if a victim is valuable. Luckily, these metrics also enable KELA to identify almost 10% of IABs’ victims with medium and high levels of confidence.
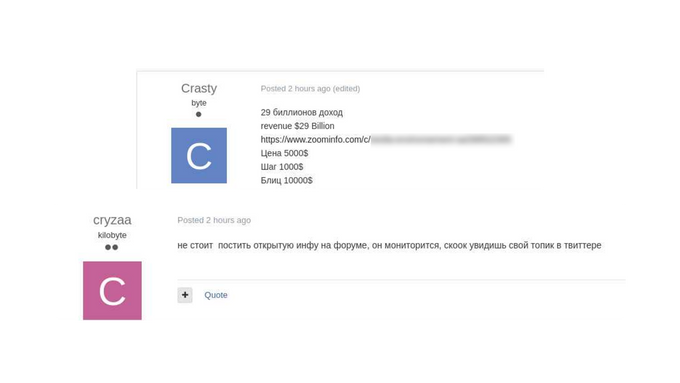
The actor “cryzaa” advises another actor who posted a link to Zoominfo’s page of his victim: “It isn’t worth to post publicly accessible information on the forum, it’s being monitored.” Source: Exploit
KELA’s recent DARKBEAST insights about identified victims
How KELA Finds Network Access Victims Attacked by Ransomware
In parallel with KELA’s daily monitoring of ransomware blogs and data leak sites, these efforts give an opportunity to detect companies that were compromised both by IABs and ransomware actors. Then, KELA investigates each case to understand if this match is a coincidence or one chain of events resulting in the ransomware attack. KELA observed at least 5 ransomware operations, most of them managed by Russian-speaking actors, buying access from IABs and using them in their attacks: LockBit, Avaddon, Darkside, Conti, and BlackByte.
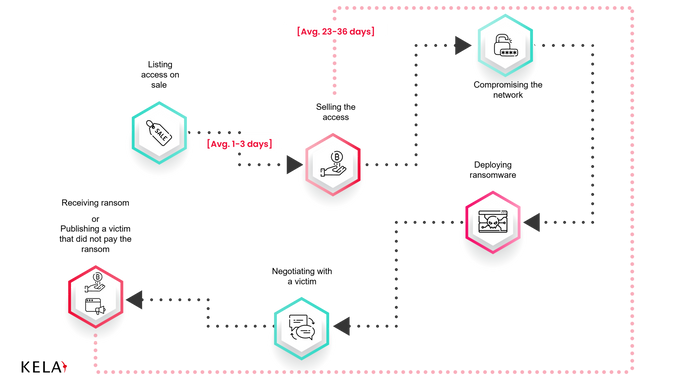
In various attacks that KELA observed, from the moment the access was listed for sale, it took 23 to 36 days to attack the company and publish its name on a ransomware blog as a result of failed negotiations.
The path from access on sale to a ransomware attack
Let’s take a look at some of these cases (please note that the two latter examples were first described in KELA’s research “All Access Pass: Five Trends with Initial Access Brokers”).
LockBit’s Attack on Bangkok Airways
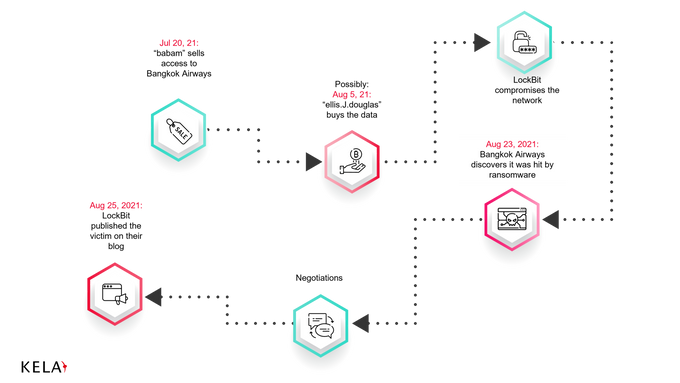
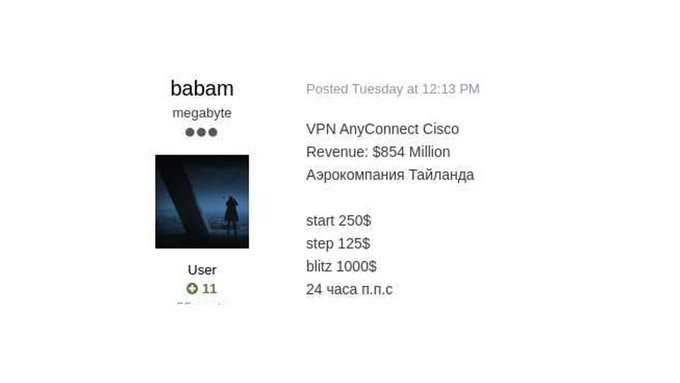
On July 20, 2021, the threat actor “babam” offered to sell access to Bangkok Airways through Cisco’s AnyConnect VPN. The actor was selling the access in an auction manner, starting with USD 250, and a “buy-out” option of USD 1000. It is not clear who bought the access and when: on August 5, 2021, the actor named “ellis.J.douglas” offered to pay the “buy-out” price though babam did not publicly confirm this deal. It is possible that the access was bought by another actor earlier. Interestingly, ellis.J.douglas the same month expressed a desire to join an affiliate program and work for a share of profits, which resembles a profile of a ransomware operation. They started operating on forums as Initial Access Broker first, and later switched to buying accesses.
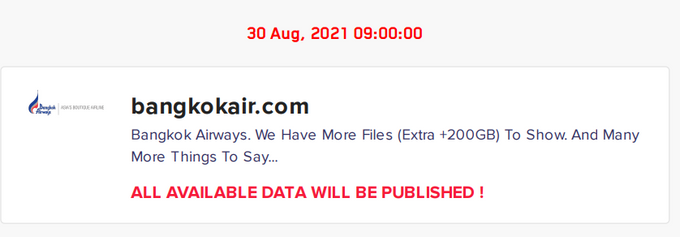
Regardless of who bought the access, the company discovered it was affected by a ransomware attack on August 23, 2021 – a little less than a month after the access first appeared for sale. Two days later, the victim appeared on LockBit’s ransomware blog. Bangkok Airways did not disclose any investigation details, but based on the timeline, it is highly possible that the attack was performed using the bought access.
a diagram showing the path from access on the sale to the attack on Bangkok Airways
a screen shot of An actor sells access to a company identified as Bangkok Airways
LockBit claims they attacked Bangkok Airways
LockBit’s Attack on an Israeli Immigration Consulting Firm
On September 20, 2021, KELA observed the threat actor “orangecake” selling access through VPN to an Israel-based immigration consulting firm (the company did not publicly disclose a further ransomware attack). The next day, the access was sold for USD 200 to the actor named chakalaka. The actor was seen both buying and selling network access listings, as well as requesting hash decrypting services.
Again, for LockBit’s affiliates, it took around a month to perform an attack. On October 25, 2021, the victim was published on LockBit’s blog.
Conti’s Attack on a US Manufacturer
On September 30, 2021, the threat actor bye47 offered access through VPN and RDP to a US-based manufacturing company. At first, no one was interested in buying the access, and the seller lowered the price several times. On October 8, 2021, the actor “framework” bought the access for USD 800. The actor is mostly buying malware, exploits, and tools, as well as offering to “work out” networks and stolen accesses.
A little more than two weeks later, on October 25, 2021, Conti already exposed this victim in their blog. In November, the ransomware operators had started to leak stolen data, though mysteriously never shared the whole stolen information.
Darkside’s Attack on Gyrodata
On January 16, 2021, the initial access broker babam, mentioned above, was observed selling access to the company identified as Gyrodata. On January 18, 2021, the actor declared that the access was sold, while on February 20, 2021, the DarkSide operators published a blog post claiming to have compromised the same company.
Gyrodata’s investigation of the incident determined that the unauthorized actor gained access to certain systems and related data within the company’s environment at various times from approximately January 16, 2021 to February 22, 2021, which corresponds with the findings.
An actor sells access to a company identified as Gyrodata
Avaddon’s Attack on a UAE Supplier of Steel Products
On March 8, 2021, KELA learned that the threat actor thyjew is selling access to a UAE supplier of steel products. Three weeks later, on March 31, 2021, the company appeared on a blog of Avaddon.
Insights for Enterprise Defenders
When talking about network access on sale transforming into a ransomware attack, the window of opportunity for an enterprise defender is short. As seen from the above examples, it usually takes less than a month for threat actors to make a deal and perform a ransomware attack. Before access gets into the hands of a buyer, defenders have only 1-3 days to understand that their company was compromised by Initial Acces Broker.
Thus, tracking IABs public activity on underground forums and taking further action is crucial for network defenders willing to understand the threat landscape and prevent damaging cyber-attacks. KELA’s DARKBEAST, an automated technology used for cybercrime research and investigations, provides defenders with the possibility to hunt Initial Access Brokers and their offers. DARKBEAST’s Finished Intelligence module enables defenders to see identified victims of IABs and react if a threat to their company, partners, clients, or other third parties is discovered.
Try DARKBEAST for 14 days now, free of charge, for your own cybercrime underground investigation: https://kelacyber.com/products/darkbeast/darkbeast-trial/