Hunting Down Initial Access Brokers with DARKBEAST
Published April 26, 2021.
Initial access brokers have taken the spotlight over the last year following their strong efforts – and success – of significantly facilitating network intrusions for ransomware affiliates and operators. These initial access brokers (“IAB”) continue to gain popularity as they become more active and popular in the cybercrime underground ecosystem. This blogpost will explore the different ways that users can leverage DARKBEAST to track and defeat initial access brokers before they cause harm.
The blogpost will explain how DARKBEAST can be used to:
- Identify noteworthy initial access brokers’ listings with the click of a button.
- Pivot to investigate initial access brokers or network access listings by utilizing complex queries, metadata searches and Boolean logic.
- Subscribe to relevant queries in order to track new results over time and receive real-time notifications.
- Identify Initial Access Brokers hindering threats behind images rather than in plaintext.
- Leverage finished intelligence compiled by KELA’s experts to gain more contextualized insights about various brokers or listings.
- Retrieve and analyze data about initial access brokers in your existing tools using the DARKBEAST API.
Who Are These Actors and What Are They Offering?
Before we begin, let’s recall both the definition of initial network access as well as the ransomware supply chain that we’ve demonstrated in our first research analyzing Initial Access Brokers.
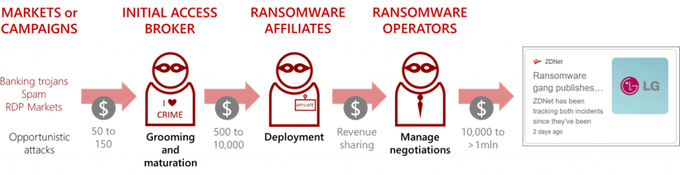
Initial Network Access refers to remote access to a computer in a compromised organization. Threat actors selling these accesses are referred to as initial access brokers. The image below demonstrates the role that initial access brokers play in the ransomware supply chain:
As presented in the figure above, the initial access brokers are playing a critical role in gaining the initial foothold into a victim’s network. As part of our ongoing monitoring of numerous initial access brokers, we observe new listings added daily in the cybercrime underground ecosystem.
Exploring the Home to Initial Access Brokers
DARKBEAST automatically penetrates the hardest-to-reach corners of the cybercrime underground to enable security practitioners, intelligence analysts, and threat hunters to safely and simply research through the cybercrime underground. Among the vast amounts of curated sources that users can pivot through are numerous cybercrime forums where initial access brokers are publishing new listings for sale, daily. To understand the abundance, in Q4 2020 alone, KELA traced almost 250 initial network accesses listed for sale at a cumulative price of $1.2 million. On average, we observed around 80 accesses offered for sale in each month of Q4 2020.
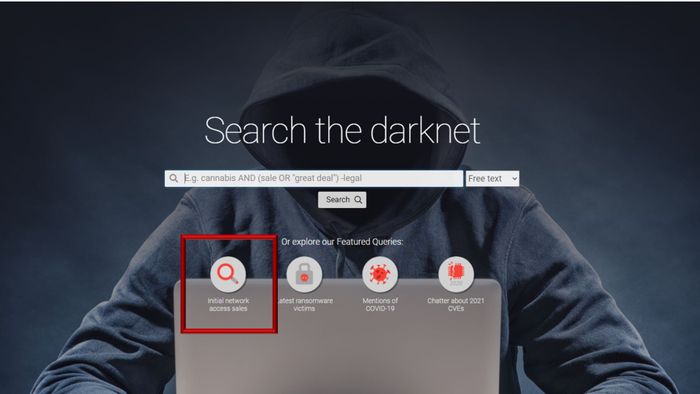
Using DARKBEAST’s Featured Queries
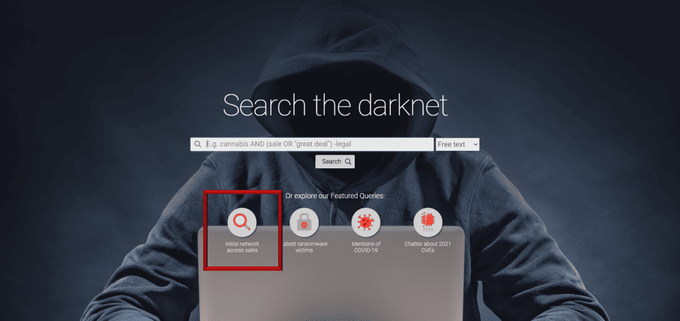
In order to make listings most accessible and simple-to-navigate, a user that just enters the DARKBEAST interface can immediately begin investigating these actors by leveraging the featured queries. The featured query for ‘Initial Network Access Sales’ automatically creates and runs a query of the most active initial access brokers that KELA continually tracks. This essentially allows KELA to provide users with a foundation to begin pivoting through other data points that could help finetune their investigations.
DARKBEAST’s featured queries enable KELA’s team to push relevant and interesting queries to users’ attention regarding emerging threats, attacker trends, and other interesting events detected in our sources. Queries constantly change and update in alignment with trends observed in the cybercrime underground ecosystem.
Leveraging Complex Queries and Boolean Logic
Let’s drill down into more specific searches, where users can investigate an initial access broker or listing of interest based on a number of parameters – i.e. listing by a specific Initial Access Broker or listings within a specific forum. DARKBEAST provides users with the opportunity to search through the darkest corners of the internet in a safe and simple manner and supports numerous ways to do so – either by directly searching a term, or by utilizing a variety of complex queries or Boolean logic. For example, by utilizing the function to search by actor name or source, or by including specific terms that they would like to identify in a listing, DARKBEAST users can easily and quickly filter through the vast amounts of raw data and finished intelligence available to retrieve the most relevant intelligence with minimal effort and time.
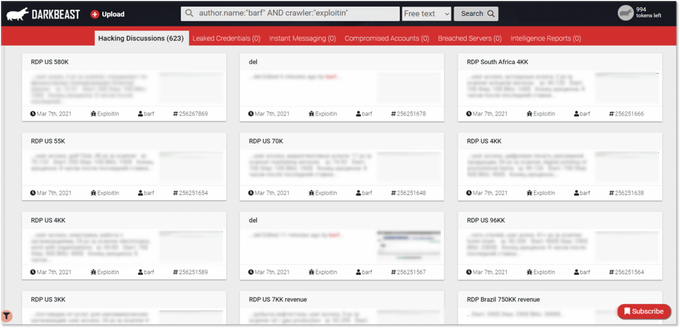
A DARKBEAST user can search for all posts by actor “barf” across Exploit over time, by using various basic and advanced Boolean search operators. This search yields all results where the IAB named barf posted in the underground forum Exploit.
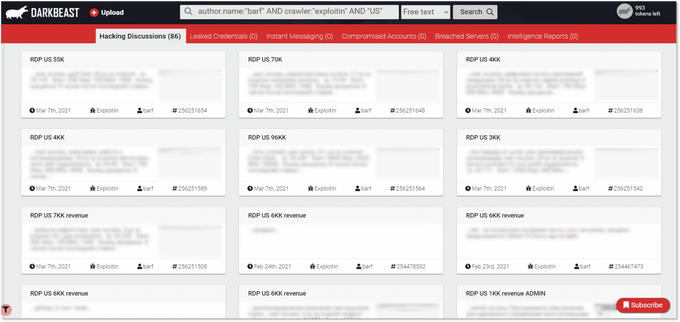
To finetune the search even further, users can perform the same search as above and add in “US” to retrieve results only about this broker’s listings related to the US.
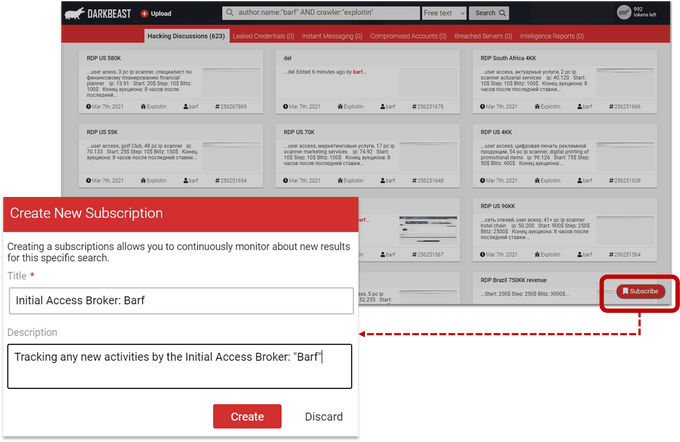
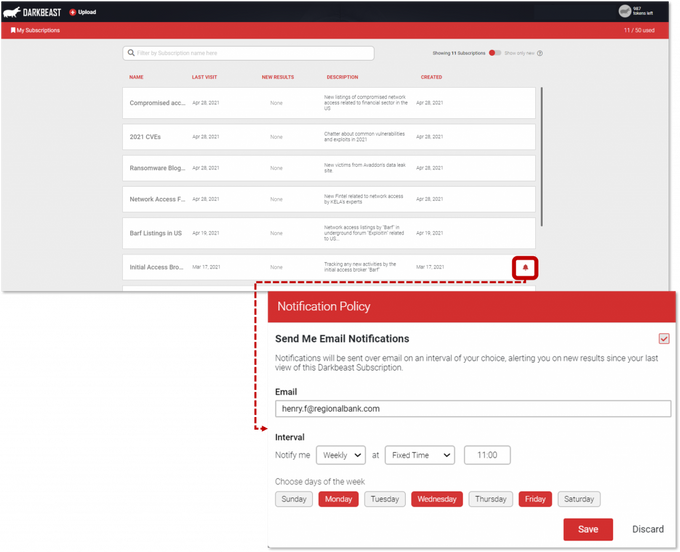
Configuring Query Subscriptions on IABs of Interest
Security practitioners can actively and continually track initial access brokers through query subscriptions. Here, users simply create a subscription, save it with the relevant details, and configure it to receive alerts at any time during the day that best suits their workflows.
In the subscriptions tab, users can view and edit each subscription they created and can set alerts to any time and frequency that suits the user’s workflow.
Bypassing IAB’s Efforts to Avoid Detection with Text Extraction from Images
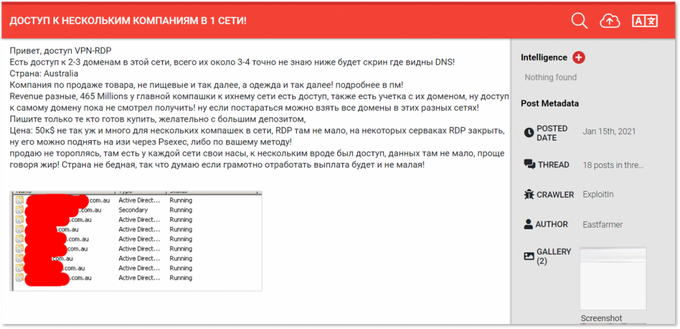
While penetrating the hardest-to-reach sources of the cybercrime underground, KELA not only collects text but also images that criminal actors are posting. DARKBEAST allows users to search through images posted by threat actors and automatically identifies keywords within images. For instance, if an initial access broker decides to post an image showing his proof of access to a victim’s network – and a victim’s assets are appearing in that screenshot – they can go perform searches on relevant queries to yield images containing the data.
By searching for images containing the suffix of an Australian domain (.com.au) and ‘RDP’ – a user can identify posts by threat actors who shared a screenshot for proof of working RDP access.
Finished Intelligence Related to IABs and Network Access Listings
Users can obtain finished intelligence about various IABs or network access listings composed by KELA’s Cyber Intelligence Center through DARKBEAST. Finished intelligence ensures that users gain contextualized and actionable intelligence and can be accessed in two different ways through DARKBEAST:
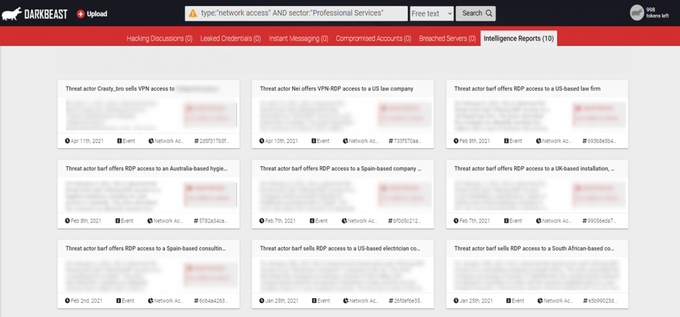
1. Users can perform a search on a number of queries that could immediately yield results of finished intelligence within DARKBEAST. For example, users can search by the threat type “network access” and immediately gain visibility into the numerous pieces of finished intelligence events and reports that KELA’s team has analyzed and explained.
Users can search by any query (such as threat type, an IAB’s name, a sector, a region, etc.) to view all pieces of finished intelligence that KELA’s experts have compiled. This example provides users with access to KELA’s finished intelligence repositories consisting of events related to network accesses targeting the professional services sector that KELA’s experts identified in the cybercrime underground.
2. Users can search for raw data and in parallel gain access to added insights on top of the raw data in DARKBEAST. The augmented data allows users to attribute finished intelligence to raw data, essentially providing users with contextualized and actionable insights. For example, many times access brokers will list a very general description of the access they have for sale, or alternatively will use attacker-specific slang or technical terms, making the raw data difficult for some users to digest. The added insights by KELA provide a clear description of the incident as well as any mention of related TTPs or background based on KELA’s knowledge of the relevant actor, source or current trends.
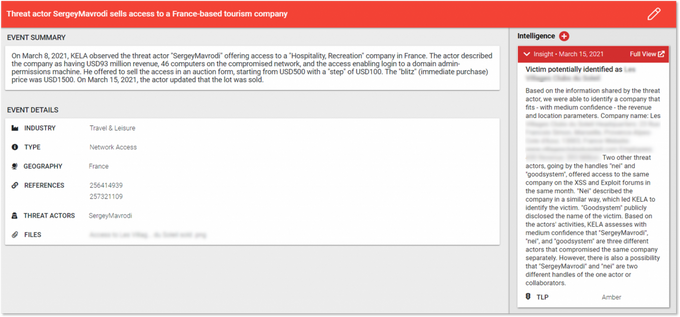
A result from DARKBEAST showing the raw data that was identified in the cybercrime underground ecosystem – a threat actor auctioning off access to a French organization. The details may be difficult to understand, making this raw data unactionable for some users. In this case, users can view the augmented data added by KELA’s experts on the top right-hand side.
The image above shows how a user can gain contextualized and actionable insights for the raw data that was presented in the previous image. Already analyzed by KELA’s experts, the raw data which was presented above is augmented with insights, providing users with contextualized and actionable intelligence. The insight above includes a summary of the raw data, details on the affected industry/geography, the type of threat, the actor involved, and the files exposed.
Accessing DARKBEAST-Driven Intelligence Through the API:
Last, with DARKBEAST’s integration to RESTful API, users can now track and analyze IABs and network access listings without the need to enter the DARKBEAST interface. The easy-to-implement API allows users to manage and operate their IAB investigation processes from their existing tools and technologies.
—
KELA’s DARKBEAST automatically penetrates the hardest-to-reach corners of the cybercrime underground to enable security practitioners, intelligence analysts, and threat hunters to safely and simply research through it. KELA’s industry-leading technology helps expose underground digital dangers to its clients by collecting, analyzing, and storing data from numerous sources such as: underground forums, specialized shops (i.e. botnet markets, remote access markets, compromised database feeds), information sharing sites, instant messaging groups (i.e. Telegram, Discord), and more. All sources qualified by KELA are stored in a secured data lake and accessible through DARKBEAST, saving users the time, risk, and complexity of needing to locate and access the cybercrime underground themselves.
To learn more or to get started, contact us today: https://kelacyber.com/contact-us/