Could The Belsen Group Be Associated With ZeroSevenGroup?
Published March 10, 2025.

KELA explores a possible link between the Belsen Group and ZeroSevenGroup, two cybercriminal entities with ties to Yemen. The Belsen Group surfaced in January 2025, leaking Fortinet data and selling network access, while ZeroSevenGroup had been active earlier, breaching companies and monetizing stolen data. Notably, both groups share similarities in writing style and post formatting. While these overlaps are not conclusive, they suggest a possible connection.
Who is the Belsen Group?
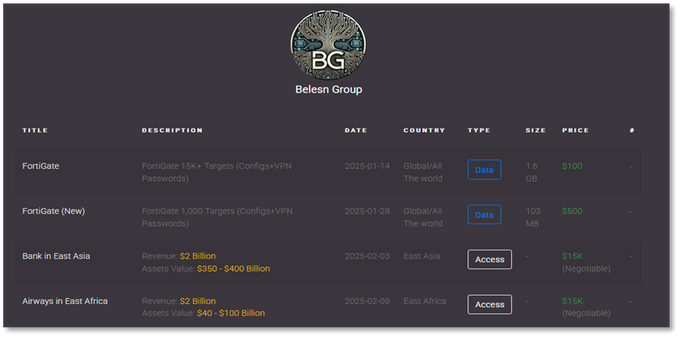
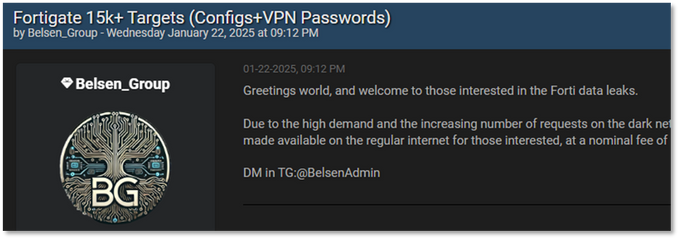
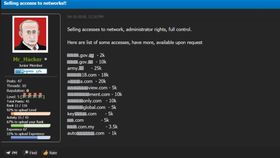
The Belsen Group emerged on cybercrime forums and social media in early January 2025, making their first major announcement on January 14 on BreachForums under the handle Belsen_Group. Their initial activity involved leaking 1.6 GB of sensitive data from over 15,000 vulnerable Fortinet FortiGate devices, including IP addresses, configurations, and VPN credentials, first on BreachForums and then on their dedicated TOR-based blog. This data was initially shared for free to build credibility. The group is believed to have exploited CVE-2022-406841, a critical authentication bypass vulnerability in FortiGate firewalls, indicating they may have had access to the data for over two years before the leak. Later, they expanded to selling network access to victims in Africa, USA, and Asia. No evidence was found that the access was sold.
Belsen Group’s Onion Website
OSINT Traces
The group has shared multiple contact methods since the beginning of its operations, including Tox, XMPP, Telegram, and X. Additionally, they maintain an onion site where they publish details of their victims alongside all their contact methods. Their Twitter account, created on January 10, 2025, mirrors the victim listings found on their BreachForums posts and onion site. The account is registered under the partially redacted email address ad********@gmail.com.
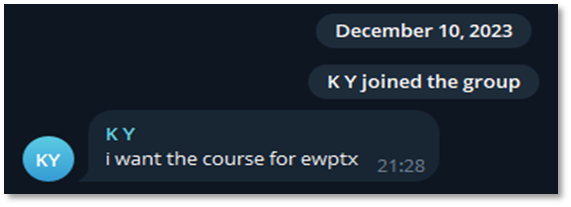
Only on their Twitter and in a one BreachForums post, they listed a Telegram user for contact. This user, @BelsenAdmin (ID 6161097506), registered in 2023 under the name “K Y.” Previous usernames associated with this account include @m_kyan0 and @mmmkkk000000. The user is subscribed to a diverse range of channels, including cybersecurity certification groups (eWPTXv2, eWPTX), adult-themed communities, regional Arabic-speaking groups in Yemen, and an anime chat group.
@BelsenAdmin posted a message on Telegram looking for the eWPTX course
Who is the ZeroSevenGroup?
While investigating Belsen Group, KELA identified a possible connection to ZeroSevenGroup, a threat actor active since July 2024 and January 2025. ZeroSevenGroup emerged in July 2024 on NulledTo before expanding to BreachForums, CrackedTo, and Leakbase. They specialized in leaking and selling stolen data and network accesses, targeting companies in Poland, Israel, the USA, UAE, Russia, and Brazil. Initially offering free leaks, they later began selling databases, often hosted on Terabox or Mega. In August 2024, they claimed responsibility for breaching Toyota’s US branch, leaking 240GB of sensitive data. Toyota initially downplayed the incident but later clarified that a third party, not its own systems, was compromised2.
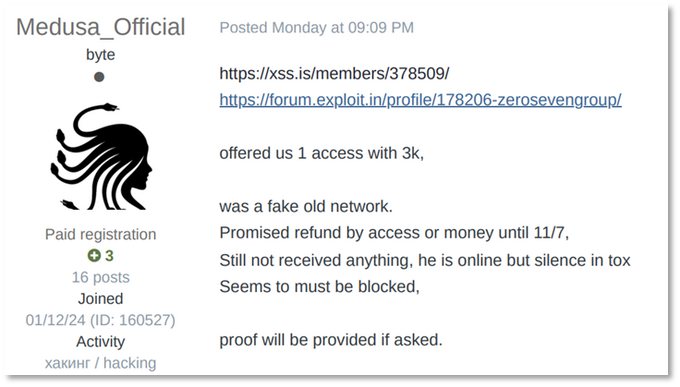
In November 2024, ZeroSevenGroup was accused of scamming the Medusa Ransomware group by selling outdated and fake network access. Since January 2025, they have been active exclusively on the Exploit Forum, where they re-emerged with a post offering C2 and VPN access to an Italian government entity, as well as companies in the US and Japan.
KELA identified individuals likely managing ZeroSevenGroup by analyzing their early activity. In their initial days in July 2024, the group shared a few free databases, providing a unique password to unlock the files. A search for this password in KELA’s data lake returned two significant findings: an email address from a leaked database and a machine infected with infostealing malware that had utilized the same password. Both were linked to Yemen and connected through social media to one another. The user behind the stealer bot was also linked to the Yemen Shield hacking group. Additionally, KELA traced the group’s presence back to RaidForums, where they operated as “ZeroXGroup” under the username zerox296. The full details regarding these findings is available to KELA’s customers with the full threat actor report of ZeroSevenGroup. Request a Free Trial now.
ZeroSevenGroup former user on RaidForums, zerox296
Possible Connection
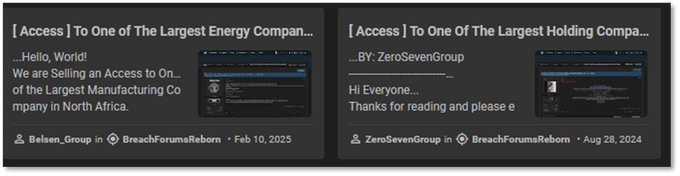
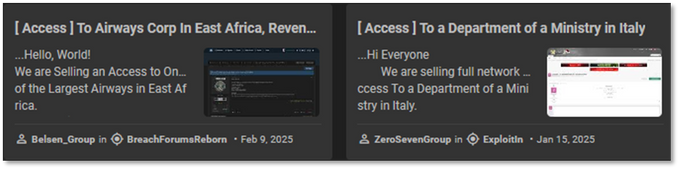
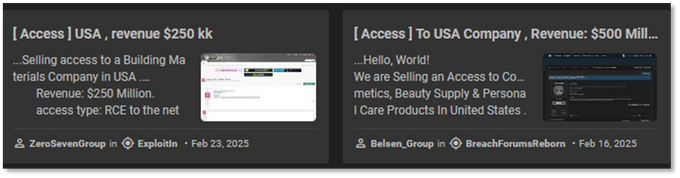
The two groups were the only users in KELA’s data lake to employ the same title format—”[ Access ]”—including square brackets and spaces, both in their titles and multiple posts. Additionally, their posts frequently exhibited nearly identical phrasing and stylistic patterns, indicating the use of a shared posting template. A targeted search for a distinct combination of keywords on KELA’s platform returned results exclusively linked to these two actors. Further analysis of their Twitter profiles revealed a consistent pattern in hashtag usage, frequently using the #hack hashtag.
These findings align with the fact that both groups appear to originate from Yemen, share an interest in network access sales, exhibit a similar writing style with recurring templates, and identify as part of a “group”, as reflected in their usernames.
While KELA cannot definitively confirm a direct connection based solely on these findings, the overlap in multiple key areas strongly suggests some level of affiliation or coordinated activity between the two groups.
2. https://www.foxnews.com/tech/toyota-has-data-dilemma-after-hackers-leak-240gb-customer-information