I-Soon Leak: Kela’s Insights
Published March 7, 2024.

On February 16, 2024, a repository titled “I-S00N” was uploaded to Github, allegedly intended to expose insider information about I-Soon (Anxun Information Technology Co., 安洵信息技术有限公司,i-soon[.]net), a Chinese technology company in the cybersecurity field. The dump may indeed be a breach of I-Soon and contains documentation related to the company’s products, including spyware and offensive tools and services. AP News reported that two anonymous employees of I-Soon confirmed that the leak originated from the company. However, the cause and the leaker are still unclear.
KELA acquired and analyzed the leaked data. This blog outlines the most interesting insights, such as the structure of the leak, clients and potential targets of I-Soon, the company’s connection to advanced persistent threats (APTs), and discussions about zero-day vulnerabilities.
What's in the leak?
According to KELA’s review, the repository contains 577 files, including duplicates of contents in different formats. The files contain “readme,” which explains the supposed nature of the leak as insider information about I-Soon and includes the following reason for releasing the information: “I-Soon is unreliable and scamming the (Chinese) state government agencies.”
Per KELA’s review, the files include:
- Thirty-seven records of text conversations between employees and managers from 2020 to 2022
- Files allegedly containing I-Soon employee information, such as names, roles, and salary rates
- Several files that appear to be detailed call logs stolen from telecommunication companies in Kazakhstan
- Lists of organizations and networks allegedly breached by I-Soon
- Many image files, including screenshots of folders, text conversations and internal notes on potential targets
- Page-by-page images of documentation on I-Soon products and services, among which are tools to monitor domestic social platforms and Twitter, offensive tools, and test tools.
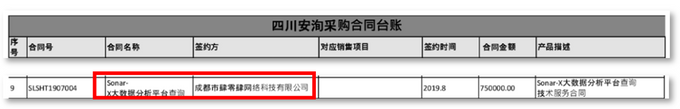
- A contract ledger listing 120 contracts and end users, many of which are Chinese local governmental bodies, and procurement ledgers
One of the leaked chat records is between I-Soon’s top two managers, Wu Haibo (吴海波, “Shutd0wn”) and Chen Cheng (陈诚, “lengmo”), dated from August 1, 2020, to August 30, 2022. Wu Haibo, seen using the name “Shutd0wn” as his chat username in the leaked record, founded I-Soon in 2010 and is known to have been part of the “Green Army” (绿色兵团) in the early days of the skilled nationalist hacktivists movement in China in the 1990s.
Client list and target list
Based on KELA’s review, the leaked conversation records reveal that I-Soon maintained close relationships with Chinese governmental bodies as a provider of cybersecurity software, services, and training, and that it infiltrated organizational networks in countries including the US, India, Kazakhstan, Vietnam, Malaysia, Mongolia, Taiwan, Thailand, South Korea, the Philippines, Myanmar, and Nepal. KELA identified lists of target countries and organizations for which I-Soon allegedly held access to internal data or networks, including organizations in the government, public, education, banking, and telecommunication sectors.
According to the leaked conversation records and contract ledger, dated September 2020–2022, the majority of I-Soon’s clients were Chinese provincial- and city-level governmental bodies, most of which were local public security bureaus. Based on I-Soon’s public website archive, the company was a certified provider for the Ministry of Public Security (MPS), which oversees all the public security bureaus throughout the country, and the Ministry of State Security.
I-Soon’s cyber-offense products and services
The following is a general overview of the tools and cyber weapons that I-Soon offered, based on KELA’s and other analyses [1, 2, 3] of the leaked documentation:
- Twitter/xStealer: This tool can retrieve a Twitter user’s email address and phone number and monitor activities in real time, read direct messages, and publish tweets on the user’s behalf.
- Custom RATs for Windows and Linux: Remote access tools that have keylogging and file logging and that can obtain information on a remote system. They include a remote shell tool that can disconnect and uninstall itself remotely in compromised systems.
- iOS/Android device exploitation: Tools for both iOS and Android platforms that can obtain information from compromised systems, including dumping messages from top messaging apps, and take real-time audio recordings.
- Network penetration devices: Devices disguised as electronics and used to attack networks from within.
- Email Analysis Intelligence Decision-Making Platform: This tool supports intel production on troves of stolen emails, AKA mass email analysis. The tool also mines IP addresses from headers and personal information from email content.
- Automated Pentesting Platform: The penetration testing tool is made up of several modules using custom and publicly accessible tools. The tool has offensive capabilities such as application exploitation, RATs, and running phishing campaigns.
Links to known APTs/nation-state activities
After analysis of the leaked I-Soon documents, especially by corroborating known indicators of compromise and tactics, techniques, and procedures, researchers were able to link two previously reported Chinese APT campaigns to the company: Jackpot Panda and Poison Carp.
Additionally, the data leak includes manuals and whitepapers of Treadstone, ShadowPad, and Sonar-X, attributed to nation-state actors, including APT 41 and Winnti Group.
Per KELA’s review, leaked conversations and procurement lists indicate a close relationship between I-Soon and Chengdu 404 (Chengdu Silingsi Network Technology Co., 成都市肆零肆网络科技有限公司), a company exposed as having been behind the operation of APT 41 in 2020.
Weaponized Comm100 attributed to Jackpot Panda
In September 2022, Trend Micro reported a supply-chain attack on the Canadian company Comm100. The attackers trojanized Comm100’s chat-based customer engagement platform hosted on the official website.
In the leaked documents, it was revealed that two employees using the company chat referred to a server on 8.218.67[.]52, which belongs to I-Soon. In September 2022, researchers found that the IP 8.218.67[.]52 served a Linux ELF file that, when executed, contacted the domain unix[.]s3amazonbucket[.]com. They found that another subdomain of s3amazonbucket[.]com was the C2 server for the installers (the trojanized Comm100 platform). The IP address is associated with the APT group known as Jackpot Panda.
Poison Carp
It was noted that in September 2019, Citizen Lab reported attackers targeting Tibetan groups via iOS and Android exploits. Citizen Lab attributed the attacks to the Chinese APT group called Poison Carp.
The Citizen Lab report refers to domains and IP addresses that were found in the leaked I-Soon documents. For instance, the IP 74.120.172[.]10, which was associated with the domain mailnotes[.]online, appeared in one of the conversations between I-Soon employees. The domain mailnotes[.]online was used in the Poison Carp campaign.
Treadstone, ShadowPad, and Winnti
Among the whitepapers and product manuals in the leaked data trove is a Windows RAT known as ShadowPad. The whitepaper on ShadowPad included screenshots containing IPs associated with potential ShadowPad C2s, noted by a researcher.
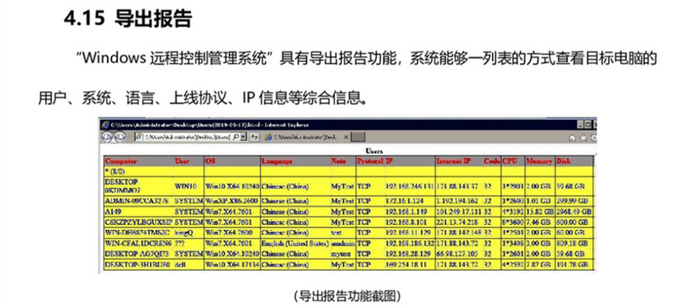
Screenshot from a Windows remote control product (ShadowPad) whitepaper with potential C2s
Researchers noted that in the same whitepaper, one of the screenshots describing the configuration screen shows an example IP address and port 118[.]31[.]3[.]116[:]44444, which was reported as a ShadowPad C2 server in August 2021, attributed to Winnti Group.
Screenshot from a Windows remote control product (ShadowPad) whitepaper with an IP reported as C2
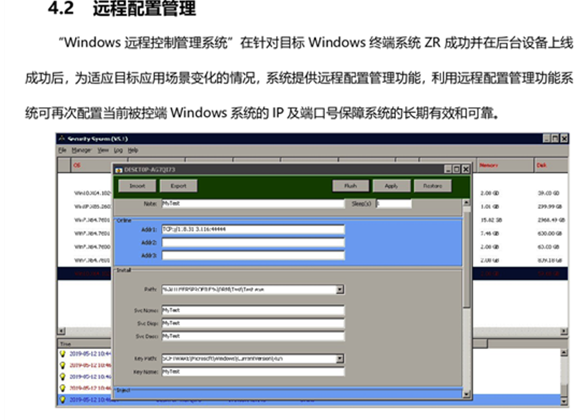
Additionally, researchers detected an image of a control panel of one of the products introduced in the leaked documents as Treadstone. Per KELA’s review, it’s in the Linux Remote Control Management System section, categorized as part of I-Soon’s product lineup in the “special-control-secret-access” category. The product description was in some of the leaked image files that constitute a 50-page document titled “Product Manual V1 2020,” credited to I-Soon’s company name. Per KELA’s review, it’s unknown whether I-Soon offered this product as a reseller or as a proprietor.
The panel name “TreadStone” can be seen in the left top corner of the image, described as “Linux remote control system control panel image.” (KELA added a red line to the part where “TreadStone” is displayed at the top left. Other red lines were included in the original image.)
Treadstone, ShadowPad, and Winnti Group have been linked to APT 41 in some campaigns by researchers, although both Shadowpad and tools from Winnti’s arsenal have also been observed being used by various Chinese threat actor groups. One such group includes RedHotel, to which some researchers note overlap with I-Soon.
Close relationship with Chengdu 404 tied to APT 41
KELA identified many Chinese companies mentioned in the conversations as potential cooperators and competitors, operating in the similar range of service providers to the domestic public sector, among which is Chengdu Silingsi Network Technology Co. (成都市肆零肆网络科技有限公司), known as Chengdu 404. While Chengdu 404 describes itself as a network research and development company registered in Chengdu, Sichuan, the FBI exposed its ties to APT 41 in 2020.
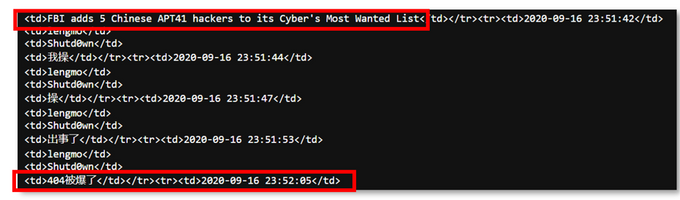
Based on KELA’s review, in one of the leaked conversation records between I-Soon managers Wu Haibo and Chen Cheng, dated 2020, there is a reference to this incident, confirming the assumption that Chengdu 404 members are indeed in groups referred to as APT 41. Furthermore, while the two managers acknowledged their joint participation in bidding and frequent interactions, they appear to confirm that there’s no key partnership with Chengdu 404, presumably to protect themselves from the repercussions of the FBI’s exposure of that company.
One of the leaked conversation records between I-Soon managers Wu Haibo and Chen Cheng, dated September 16, 2020. They bring up the news of Chengdu 404’s exposure by the FBI and mention their close relationship with the members, while confirming that there’s no business partnership between I-Soon and Chengdu 404.
Per KELA’s review of another leaked conversation, dated 2022, and a document titled as a list of I-Soon’s procurement contracts, it was indicated that I-Soon was procuring items from Chengdu 404, including “Sonar-X Big data analysis tool.” According to the US Department of Justice’s indictment of Chengdu 404, Sonar-X is a social media repository and search tool that enables users to explore social media records pertaining to individuals of interest, potentially for use by Chinese intelligence.
Excerpt of a document titled “Sichuan I-Soon’s Procurement list” (redacted). The document shows that I-Soon (Sichuan branch) was procuring items from Chengdu 404, including Sonar-X.
Nevertheless, there’s no indication that I-Soon was collaborating with Chengdu 404’s activities as a part of APT 41 campaigns.
Zero-day vulnerabilities discussed in chat records
KELA’s review detected multiple mentions of vulnerabilities referred to as zero-day. KELA analyzed conversation logs, collated known vulnerabilities, and noted which vulnerabilities the conversations were about.
Tianfu Cup 2021’s zero-day vulnerabilities seized by MPS
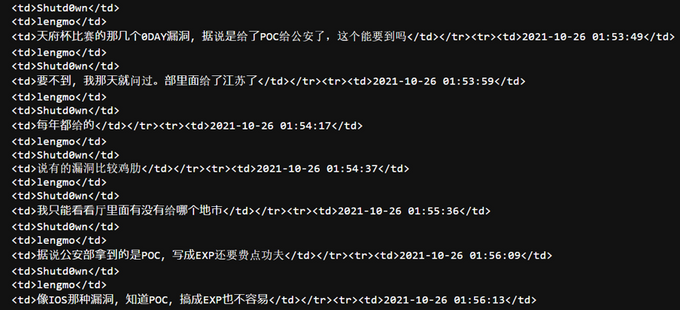
Among the chat records between Wu Haibo (“Shutd0wn”) and Chen Cheng (“lengmo”) is a discussion dated October 26, 2021, about zero-day vulnerabilities from Tianfu Cup, which is one of China’s prestigious cybersecurity competitions. Considering that the Tianfu Cup 2021 was held in Chengdu on October 17, 2021, this conversation took place nine days after the event.
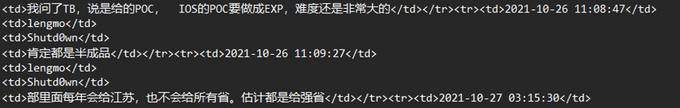
In the conversation, Shutd0wn asks lengmo if they can obtain “Tianfu Cup’s 0day vulnerabilities that were said to have been given to the [Ministry of] Public Safety.” Lengmo replies “We cannot, I have already asked [about it].” It’s unclear which zero-day vulnerabilities they’re talking about. However, per KELA’s review, lengmo later mentions that it would be difficult to create an exploit of “those IOS vulnerabilities,” a possible reference to the iOS zero-days hacked by two teams in the Tianfu Cup 2021.
Additionally, they mention in the conversation that the MPS had internally given the vulnerabilities to Jiangsu (likely the province-level public safety bureau), then to Wuxi (likely the city-level public safety bureau). Interestingly, Shutd0wn mentions that “[MPS] gives [the zero-days to them] every year,” referring to Jiangsu.
Shutd0wn and lengmo discuss “Tianfu Cup (2021)’s 0day vulnerabilities” as seized by the MPS
Log4j2, Mikrotik, and Juniper SRX flaws
Three additional zero-day vulnerabilities are seen being discussed in two different leaked chat records between I-Soon employees:
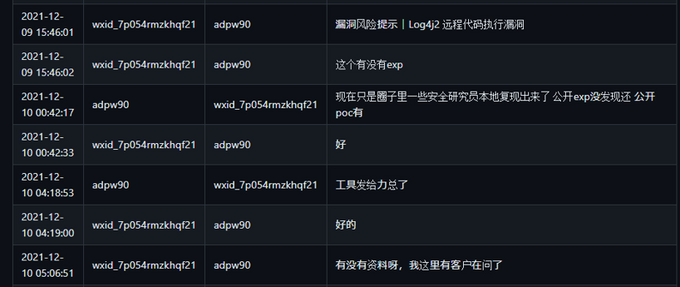
- Log4j2’s zero-day vulnerability’s exploit on December 9, 2021
- “Mikrotik 0day” on December 2, 2021
- “Juniper SRX Firewall RCE 0day” on November 30, 2021
While according to the chat, only Juniper RCE seems to have been “most likely” available for the I-Soon staff to exploit as of the date of the conversation, these chat records indicate that I-Soon was constantly looking to find and exploit zero-day vulnerabilities.
Per KELA’s review, the “Log4J2 0day” likely refers to CVE-2021-44228, found on December 9, 2021, and published on December 10. The leaked chat on the vulnerability starts with an employee sharing a news article about Log4j2 and asking another employee if they have an exploit or not, to which the other employee answers that there are no public exploits but only a proof of concept.
I-Soon employees discuss exploitability of Log4j2 0-day vulnerability, likely referring to CVE-2021-44228
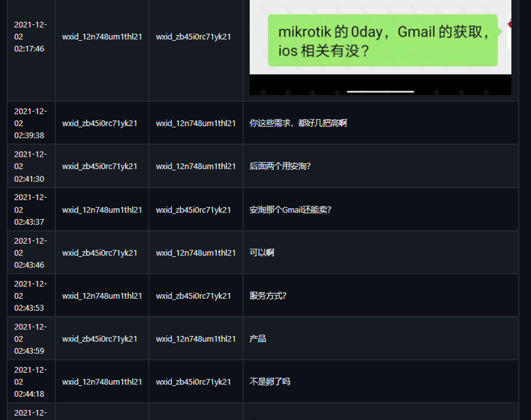
As for the “Mikrotik 0day,” KELA could not detect which vulnerability was referred to, as there’s no additional context discussed in the chat.
I-Soon employees discuss if “Mikrotik’s 0day” is relevant (to I-Soon)
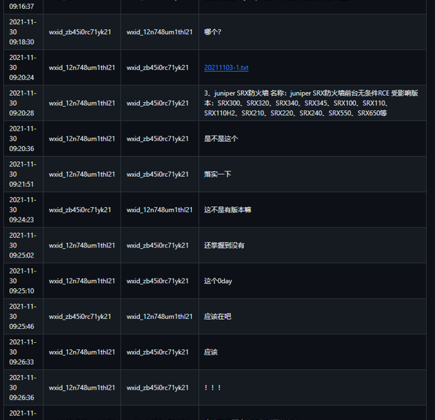
Employees of I-Soon also discussed “Juniper SRX Firewall RCE 0day.” In the chat record on this “0day,” one employee asks another employee, “Have you got hold of this 0day vulnerability yet?” after detailing it as “Juniper SRX Firewall Front-End Unconditional RCE, Affected Versions: SRX300, SRX320, SRX340, SRX345, SRX100, SRX110, SRX110H2, SRX210, SRX220, SRX240, SRX550, SRX650, etc.” The other employees responded, “Should have.” At this time, KELA could not pinpoint a specific CVE that could be related to the mentioned vulnerability.
I-Soon employees discuss if the team can exploit “Juniper SRX Firewall Unconditional RCE 0day”
Why does the leak matter?
The recent data leak sheds light on a broader ecosystem of cyber offense vendors serving Chinese governmental bodies, with companies like I-Soon competing in capability and price to infiltrate high-value foreign organizations’ assets. The leak suggests a competitive landscape where multiple entities offer such services, and it provides a unique view into their inner workings.