5 Questions (and Answers) About the Kyivstar Attack
Published December 15, 2023.

Following a cyberattack on December 12, 2023, Kyivstar, a major Ukrainian mobile network operator, faced a significant digital crisis. The incident has been discussed as one of the most powerful attacks on a telecommunication organization. Confusing claims surfaced from hacktivist groups like Killnet and its successor, Deanon Club, along with Solntsepek. In this blog, KELA dives into the details of the Kyivstar cyberattack, exploring the conflicting stories and the potential involvement of a Russian nation-state actor.
What Happened?
On December 12, 2023, the Ukrainian mobile network operator Kyivstar experienced a cyberattack. The attack is said to have affected not only mobile and internet services but also the air raid alert system in parts of the Kyiv region.
The CEO of Kyivstar stated in interviews that the attackers infiltrated the infrastructure with the aim of destroying or interrupting the virtual IT infrastructure of the operator as much as possible. Kyivstar attributes the root cause of the telecom attack to a compromised employee account, following which the actors were able to infiltrate the “center” or “core” of the infrastructure, added the CEO. Currently, the company and its partners are investigating whether this incident was a premeditated “insider” event or involved social engineering/hacking.
Who Claimed Responsibility?
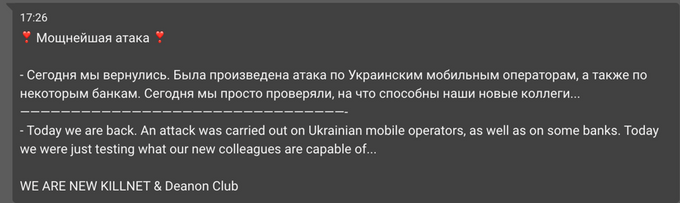
On the day of the attack, the Killnet hacktivist community claimed they are related to the attack: “Today we are back. An attack was carried out on Ukrainian mobile operators, as well as on some banks. Today we were just testing what our new colleagues are capable of…” The claim has quickly raised skepticism among cybersecurity researchers including pro-Russian hacktivists. Based on Killnet’s previous attacks and TTPs, the Kyivstar incident appears to surpass the group’s typical capabilities.
The statement came a few days after a leadership transition within Killnet: The former owner Killmilk “resigned” while a threat group Deanon Club took over their Telegram channel (please refer to the section “Who is Deanon Club” below). Based on KELA analysis, it seems that Deanon Club’s main focus is DDoS attacks and hacking discussions, therefore the leadership transition is unlikely to have brought highly skilled actors into the Killnet group. However, it is possible that Killnet/Deanon Club referred to other hackers involved in the attack by mentioning “colleagues” in their statement.
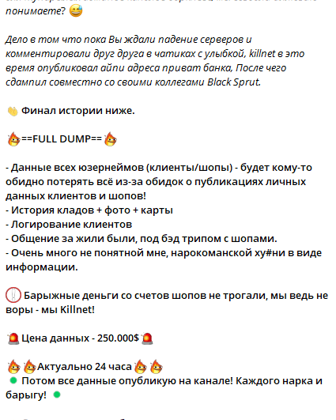
Killnet refers to a cyberattack on “Ukrainian mobile operators and banks.” In the following post, they also shared a screenshot of Kyivstar statement taken from Facebook (screenshot via KELA platform)
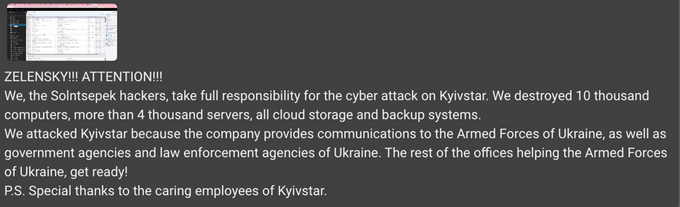
On December 13th, one day after the attack had occurred, another hacktivist group named “Solntsepek” claimed responsibility for it in their Telegram channel. The Solntsepek actors said they have “destroyed” 10,000 computers, over 4,000 servers, along with cloud storage and backup systems. They even presented screenshots suggesting access to server management systems and client information, with data dating back to November 2023. However, some chat members expressed skepticism about the legitimacy of the claims, noting that the provided screenshots only displayed alert logs.
Solntsepek claims responsibility for the cyberattack on Kyivstar (auto-translated by KELA platform)
Although Kyivstar dismissed the allegations and assured that no client data had been compromised and no servers had been destroyed, on December 13th, 2023, the CEO acknowledged the claims of Solntsepek, saying it is “obvious” that the Russian security services were behind the attack.
The Security Service of Ukraine (SBU) has stated that the Russian security intelligence services are behind this attack, and mentioned that the group that took responsibility (while not naming specifically Killnet or Solntsepek) is known as the hacking division of the GRU, a Russian intelligence agency.
Who is Solntsepek?
Solntsepek describe themselves as a “hacking group”. They have been active in their Telegram channel since June 2022, mostly deanonymizing Ukrainian soldiers. The group runs a website that contains personal data of the exposed soldiers (currently unavailable).
In September 2023, Solntsepek claimed to have executed cyber attacks against Ukrainian banks Oschadbank and Accordbank. The group posted screenshots from an online tool for checking availability of websites as a proof of DDoS attacks, allegedly showing that two subdomains of the banks were not available. The group also said they had stolen personal information of Oschadbank clients. The banks did not comment on these claims.
Solntsepek has also occasionally claimed to have stolen data of other Ukrainian companies, as well as to have executed DDoS attacks on organizations from other countries, collaborating with various pro-Russian hacktivists. Some of their attacks, such as hacking into public-facing infrastructure, have been confirmed, but the data theft or more powerful attack claims were denied or never commented on by alleged victims.
Pro-Russian hacktivists collaborating with Solntsepek
Solntsepek have not addressed that incident further, focusing on posting Ukrainian soldiers’ personal data. Ukrainian intelligence services believe the group to be controlled by GRU, although it remains uncertain whether the group has participated in the attacks or perhaps was just utilized to publicly claim the responsibility for the incident, drawing attention to the attack.
Who is Deanon Club and What Does it Have to Do with Killnet?
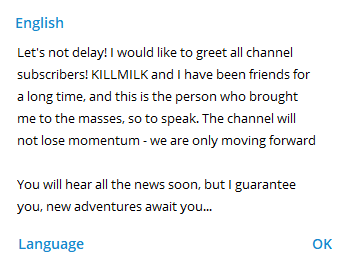
Killnet is a pro-Russian hacktivist group that has been targeting organizations from Ukraine and its allies since February 2022. Killnet was founded in November 2021 by the actor ‘Killmilk’. On December 7, 2023, Killmilk, the leader of Killnet, announced his “retirement”. On the same day, it was announced on Killnet Telegram channel that Deanon Club is the new owner of the group. The actor stated that he and Killmilk “had been friends for a long time”.
Deanon Club’s post on Killnet Telegram channel
The current Deanon Club Telegram channel was created on October 22, 2022. As of the time of writing this post it has almost 30,000 subscribers. The group operated several Telegram channels in the past, and the project seems to have existed for over a year. Deanon Club claims to distribute DDoS attacks on dark web drug marketplaces and publishes general information about dark web markets.
The administrator of “Denon Club” Telegram channel has been operating under the Telegram username btc_dc_club, with the name Btc. It is most likely that the actor “BTC” who has been active on InfinityForum since December 31, 2022, sharing the contact information of “Deanon Club” and the previous Telegram channel of the group. The user under the handle ‘ShadowMan’ shared a blog post on Telegraph claiming that the identities behind DeanonClub are individuals named Pavel Davidenko and Nikita Antipov.
The actor behind DeanonClub has been also active on Exploit since March 2023. He published several posts, sharing the source code of Pegasus Spyware. Two other users, probably affiliated with DeanonClub, were active on Exploit during different periods of time using the same Tox. One of them, the user ‘Tokio’ was seen seeking Russian-speaking pentesters for his team. The actor Carshop was interested in buying traffic.
Killnet and Deanon Club have been collaborating since 2022, for example, attacking Black Sprut, as well as other drug marketplaces. They also established Infinity Forum, a now-defunct forum for cybercrime discussions and the sale of logs, databases, exploits, accesses, and services.
Killnet and Deanon Club first attack
As mentioned above, based on the previous activity of DeanonClub, it appears that the primary focus of the project revolves around doxxing, DDoS attacks and discussions related to hacking. The transition in Killnet leadership seems unlikely to have attracted highly skilled individuals who could have performed the attack on Kyivstar. While referring to the attack on Kyivstar, DeanonClub mentioned “colleagues”, possibly referring to the actors involved in the attack, not clear if meaning Solntsepek. However, Killnet has been known in the past to make unsupported claims and exaggerate their attacks, therefore the whole Kyivstar attack claim could be just another PR action for the community, especially in need of that after changing the leadership.
Is a Russian Nation-State Actor Using Hacktivists?
The attack against Kyivstar appears to have been orchestrated by a Russian nation-state actor, with these claims being raised both by the cybersecurity community and the Security Service of Ukraine, as well as the victim. Both Killnet and Solntsepek have been quick to claim the responsibility for the attack, however, they did not provide sufficient proof for these claims and they addressed the attack only after it was reported in the media. Their previous activity does not suggest the actors could have acted alone to conduct such an attack, if they were involved at all. Thus, the statements could have been just another attempt to promote the groups and intimidate the public.
Alternatively, the groups’ Telegram channels could have been used by a Russian nation-state actor/GRU to generate buzz and draw further attention to the attack. While it is not confirmed that a Russian nation-state actor directly controls all activities of pro-Russian hacktivists, it is quite clear that these hacktivists act in line with the needs of nation-state operations and targeting.
Get notified about threats targeting your organization in real-time. Try KELA’s Cyber Threat Intelligence Platform for Free.