More Than Data: Ransomware Groups Are Now Selling Network Access Directly
Updated February 12, 2024.

No, ransomware extortionists aren’t heading back to college to grab a degree in Art History. Nothing that dramatic. But typically, we would expect to see ransomware groups and threat actors doing ransomware-type things.
Y’know — targeting specific organizations, encrypting their sensitive data for a ransom, or sharing it publicly on the web or via Telegram channels.
Increasingly, KELA has identified that ransomware groups are adding to their usual tactics, selling direct network access as a new method of monetization.
While this network access would usually be offered by Initial Access Brokers (IAB) to the highest bidder, and presented on cybercrime forums such as Ramp, XSS, Exploit, or BreachForums (to name a few), some ransomware groups are now advertising network access for sale directly from their own blogs, on Telegram channels, or via data leak websites.
Seeing it in Practice: 3 Examples of Network Access for Sale
To understand this evolution of tactics, here are three examples of ransomware groups who are dabbling in network access for sale.
Lockbit
One of the most active ransomware operations, Lockbit is a ransomware-as-a-service (RaaS) operation that has been active since 2019. This group has claimed over 2,000 ransomware victims, and counting. Globally, it was the most deployed ransomware variant in 2022. There’s no official awards ceremony for being the most dastardly criminal — so we do hope they accept this emoji trophy instead. 🏆
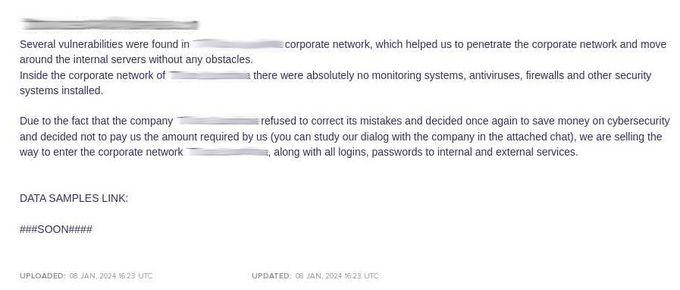
LockBit appear to be thinking about a disturbing addition to their strategy, as in January 2024, KELA observed LockBit offering access to a Scandinavian electronics company, claiming that it could sell access to the corporate network, as well as the logins and passwords that would provide access to internal and external services.
Stormous
As a ransomware group, Stormous attracts some skepticism, mainly because it has often failed to share proof of intrusion or publicly available data. However, since 2021, the group has been active, compromising somewhere in the region of 50 victims. It is affiliated with the hacking collective Five Families.
Since December 2023, Stormous has come into its stride in selling network access to a wide range of organizations.
On December 21, 2023, KELA observed Stormous selling access to six different entities. Three were in the education sector, across Turkey, Thailand and Egypt. Additionally, KELA monitored Stormous selling access to a Serbia-based software engineering company, a Vietnam-based electricity business in the Energy sector, as well as a Moroccan Telecommunications company. Sounds like a profitable day, but highlighting just how affordable cybercrime has become to the average criminal, the network access to all six organizations was offered for under $25,000 USD. To put that into perspective, you can’t even get a new Lexus for that.
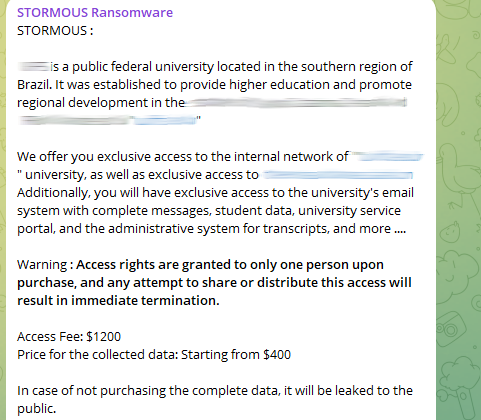
Since then, Stormous has continued using its Telegram channel to sell network access to a wide range of corporate networks, including a university in Brazil, where Stormous is selling access to the internal network, the email system, student data, the administrative system, and more. In early February, Stormous has been seen selling access to a US-based Insurance company, a Peru-based casino, and a Vietnam-based insecticide supplier. We think it’s safe to say they are casting a wide net.
Everest
Finally, Everest is more than just your kid’s favorite paw patrol pup — it’s a Russian speaking ransomware group that’s been active since 2020, claiming approximately 90 victims so far. Like the pup, Everest loves a transformation, and has evolved from a data exfiltration group to a ransomware operator, and now sells access to networks directly.
KELA has monitored Everest offering access to various networks since 2021, with a trend towards government targets in Brazil and Peru, many US-based government entities including a District Court and an official Department of Motor Vehicles.
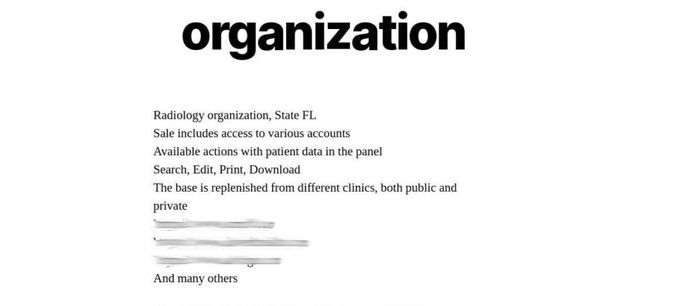
However, over time, Everest has become less picky about its targets, expanding its network access offerings to include a Canadian aeronautics organization, the corporate network of a particular Telco giant, and access to a large database belonging to a Medical organization in Florida.
You Can’t Put the Ransomware Tactics Back in the Bottle
Not to be the bearer of bad news, but organizations need to recognize that with ransomware groups selling network access as a matter of course, they are now facing a broader scope of threat. It’s never been a better time to enhance cyber resilience in response.
The scope of these attacks, across industries that vary from professional services and education to healthcare, energy, and telecommunications sectors, and the global reality of recent network access sales show that no one is truly safe.
Ransomware and extortion actors have found this additional avenue to monetize their skills, and there’s likely no going back.
Looking to boost your threat intelligence to stay ahead of emerging cyber threats, and adapt your protocols ahead of time? Request a Free Trial of KELA’s Cyber Threat Intelligence Platform.