New Phone, Who Dis? The Importance of Verifying Threats in the Age of Fake RaaS
Published March 19, 2024.

They say imitation is the sincerest form of flattery. If that’s the case, some ransomware-as-a-service (RaaS) threat actors must be feeling seriously good about themselves lately.
With ransomware operations hitting the headlines, and the global cost of ransomware damage predicted to hit $231B by 2031, threat actors are increasingly creating fake operations, often leveraging the fame of other actors to get more attention to their own activities in order to get a slice of the action.
What’s in a Name?
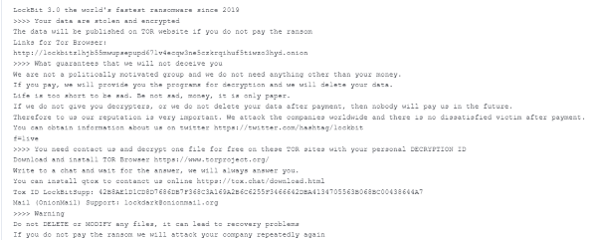
Like anyone who has ever been the victim of a good old catfishing operation knows, you can say you’re anyone on the web — and who is to know the difference? That’s what at least one attacker thought anyway, when they launched an alleged ransomware site in a similar design to LockBit’s own ransomware blog in December 2022. Six victims were named, and ransom notes that directed users to the site leveraged the “good name” of Lockbit to demand payment.
However, looking closer at the details of this supposed threat, KELA uncovered that the contact details do not match those shared by LockBit, and the aforementioned blog has been never linked to LockBit. While this was a simple case that hardly needed Sherlock Holmes to expose, other threat actors are investing a lot more time and effort to mimic other RaaS actors and add legitimacy to their own false operations.
Fake Ransomware on the Rise
One famous instance of fake ransomware actors is the case of Groove, a gang that was announced by the founding administrator of RAMP forum, and originally claimed to be responsible for the Babuk ransomware operation, citing its involvement in industrial espionage as well as ransomware. In October 2021, after many posts on its website, including a request for $30M to cease its activities, the site was outed as a “trolling project”, aimed at manipulating the western media and exploiting public fear of ransomware itself.
More recently, KELA has uncovered similar examples of fake ransomware groups. In February 2024, we identified a new data extortion site which went by the name Mogilevich. It showcased data supposedly stolen from one victim, with an option available to buy this data via a Telegram channel or an email address.
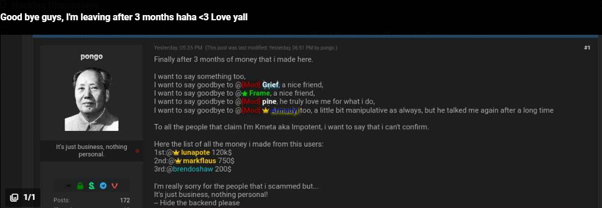
However, less than two weeks later, the gang confessed to being “professional fraudsters”, claiming that they had fabricated high-profile targets to gain attention and get themselves a lucrative pay day. Under the handle “Pongo”, Mogilevich claimed that panel access had been sold to 8 threat actors, and listed the money he had scammed out of other users.
Pongo admits to scamming other users on BreachForums
Interestingly, the username Pongo is associated with a user who has the same handle on BreachForums, and was previously banned for scamming other users.
Another recent example is Dispossessor, a data leak website that has many design similarities with the LockBit website. After thorough analysis, KELA suggests that it may have leveraged the data of LockBit, 8BASE, Clop, Snatch and other ransomware operations in order to give itself legitimacy as a serious threat. The gang even seems to have created a fake news website to threaten victims with reports about attacks on them. As most of its information appears to be manipulated or stolen from other sources, including public media and other threat actors, and as most of its claims are unable to verify and remain unsupported — it is likely that at this time Dispossessor carries a low level of threat. Unless you’re threatened by overuse of the letter S.
Anyone Can Put on a White Hat
Even when a supposed cybersecurity researcher is blowing the whistle, it’s important to get all your facts straight. A great example is the report of La Piovra, published by a person named Nelu Porumbelu, who has a website that only contains information related to this supposed ransomware group.
The content of the report appears to be mostly lifted from a public blog on the Cybereason website, from an article sharing legitimate content concerning the REvil / Sodinokibi ransomware.
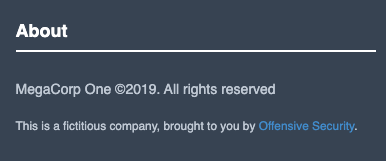
The victim company named on the La Piovra blog is “a fictitious company, brought to you by Offensive Security.”
In short, we wouldn’t start quaking in your boots about the risk level just yet.
Attackers Can Smell Fear: Approach Ransomware with Logic and Knowledge
If attackers are happy to steal from you, the chances are they won’t draw the line at lying to you either.
In the world of cybercrime, it’s critical to second guess absolutely everything you see. Ransomware actors play on your fear and your sense of urgency, and want victims to act without thinking, because that makes it more likely the dollar signs will appear on their bank statement.
You can’t always know when a threat actor is reputable, but here are three top tips:
- Check how unique the content is: Can you reverse search the image being shared and find it anywhere else? Is the copy being used taken from another website or threat group? These are signs that all is not as it seems.
- Perform due diligence: Don’t raise the alarm until you’ve checked that you are sure a source is real. Even researchers can get it wrong, or be threat actors in disguise. Investigate ties between different threat actors to see if a new name is legitimate.
- Stay informed: A platform like KELA ensures you receive precise alerts instantly, as a cyber threat emerges. Our aim is to establish a benchmark in proactive Cyber Threat Intelligence, taking pride in guiding you through this landscape.
Looking to boost your threat intelligence to stay ahead of emerging cyber threats, and adapt your protocols ahead of time? Request a Free Trial of KELA’s Cyber Threat Intelligence Platform.