INVESTIGATE
The cybercrime underground ecosystem is constantly mutating and evolving. Its most harmful operations are hidden in its darkest corners.
KELA’s technology casts the widest net across the Internet’s hidden sources, making collection and management of intelligence highly scalable and accessible.
The Investigate module helps analysts to perform successful threat hunting and deepen their cyber investigations with contextualized intelligence insights as to attackers’ TTPs, threat actor profiles and identities, hacking discussions, and more.

CYBERCRIME INVESTIGATION
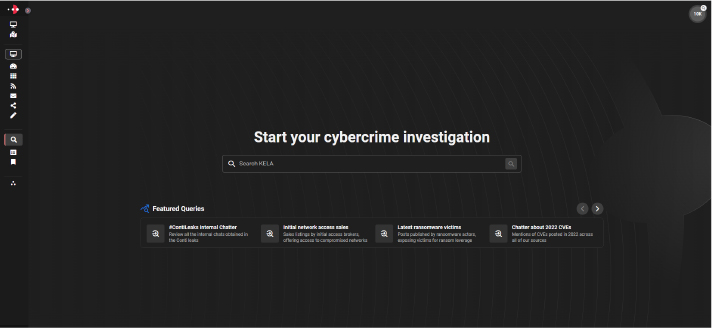
INVESTIGATE AND ANALYZE THREATS, TARGETS, TOPICS AND GROUPS, ANONYMOUSLY AND IN REAL-TIME
IN-DEPTH INVESTIGATION
Intuitive search functionality
Investigate any data point in real-time
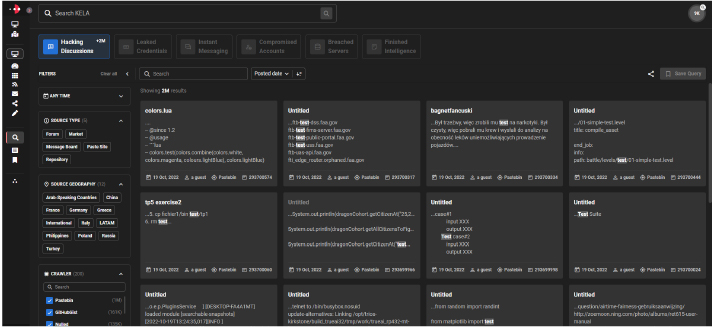
Perform complex query searches
SECURITY DATA LAKE
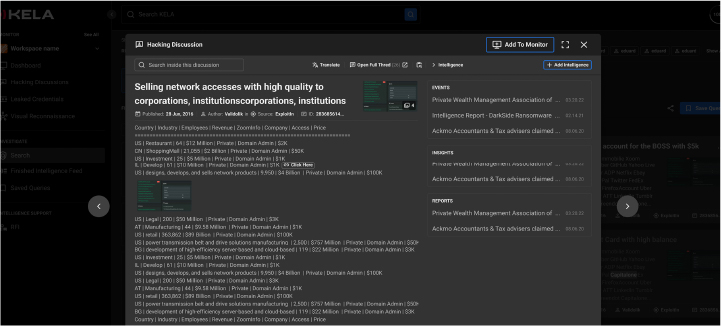
Access intelligence from database dumps, Telegram groups, botnet markets, hacking chatter and more
Enables anonymous and safe investigations
Avoid exposing your scope and obtain access to raw data
FINISHED INTELLIGENCE
Gain full access to research from KELA’s world-class Cyber Intelligence Center
HOW IT WORKS
REAL-TIME DATA COLLECTION
KELA's Investigate module automatically and continuously collects information from hard-to-reach, dynamic cybercrime sources.
UNIQUE IMAGE ANALYSIS FEATURES
The module collects text, images and other meta-data from its sources and applies image analysis to extract critical intelligence from images in a searchable format.
COMPLETE ANONYMITY AND SAFETY
KELA's Investigate module serves as an anonymous proxy to search and access the different sources in real-time, without breaking any security or compliance policies or attracting unwanted attention.
POWERFUL FEATURES
REAL-TIME INVESTIGATIONS
Perform in-depth investigations on any data point and access valuable results in real time.
COMPLEX QUERIES
Allows users to perform complex query searches, and immediately retrieve relevant results.
ONGOING SOURCE ADDITION
Access intelligence from database dumps, Telegram groups, botnet markets, hacking chatter and more, straight from KELA’s security data lake.
QUICK PIVOTING
Enables an optimized search process of all data.
TOTAL ANONYMITY
Safely search and access the cybercrime underground while meeting legal and compliance requirements.
MULTIPLE LANGUAGE SUPPORT
Search and access raw data in more than 100 languages, and auto-translate results.
SECURED SEARCHES
Conduct secured investigations without exposing your scope to KELA and obtain access to raw data straight from our security data lake.