Raidforums Leaked Database – Insights and Intelligence by Kela
Published May 31, 2023.

On May 29, 2023, a database containing the information of nearly 479,000 members of the RaidForums hacking forum was leaked online on a new forum named Exposed. RaidForums was known for hosting, leaking, and selling stolen data from breached organizations. Following the seizure by law enforcement and its subsequent closure, users migrated to a new forum called Breached (BreachForums). Breached was just recently seized by law enforcement, too, after its founder was arrested.
Exposed has emerged as a possible replacement for Breached in May 2023; its founders are not seemingly affiliated with the owners of RaidForums or Breached. The leaked RaidForums database was published by a user called ‘Impotent’, the owner of Exposed, who stated that its origin is unknown. Users on other cybercrime communities have wondered, too, how this leak came to be if access to the forum was supposedly only at the hands of law enforcement. The forum has used the leak as a marketing tool and placed a banner inviting all new users to come and download the leak (which is possible by buying a 50 euro upgrade to reveal the download link). Following the leak, the number of users on Exposed tripled: from around 900 members on May 28, 2023 (one day before the leak) to more than 3200 users just two days later.
KELA has indexed the database (available on KELA’s platform through a free trial via the following query) and is sharing some insights gained from exploring it.
What’s in the dump
The leaked table appears to cover members who registered between March 2015 and September 2020 and includes users’ email addresses, usernames, instant messaging usernames, languages, IP addresses, DOBs, forum usage information, login keys, and hashed passwords with salt.
As stated by Impotent, some users were removed from the leak.
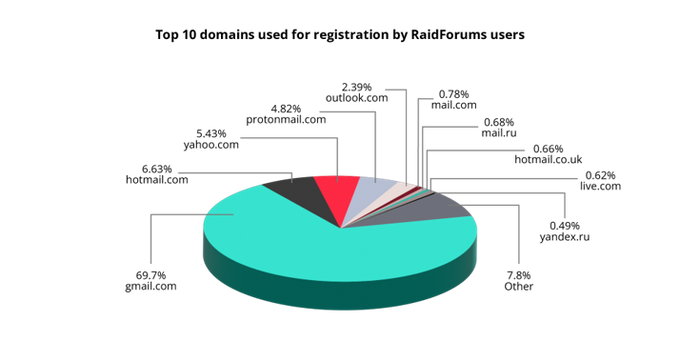
Top email services preferred by RaidForums’ users
What would be your bet on the top email service used to register to the website? Well, it appears that the statistics here are no different than for any other international service on the planet! Gmail is the leader, with almost 70% of the users who opted for it. Only 4.82% of users registered with Protonmail, an email service that drew a lot of attention from cybercriminals due to its initial (and maybe still kept) promises of top privacy.
Top email services used on RaidForums for registration
How many users were really active on the forum
A whopping 63% of users were inactive in terms of posting. The database reflects the number of posts each user published — and while KELA observed that this was not 100% accurate based on the data we ingested — the differences are minimal, so the observation remains true.
To provide a clear comparison, according to KELA’s data, within the given timeframe that the database is believed to cover, approximately 4 million posts were made by only 260,000 users. In September 2020, the forum had about 480,000 registered users, which accounts for 54% of the user base, a figure that closely aligns with the findings from analyzing the leaked database.
Actors do not hesitate to reuse their emails across hacking communities
Comparing exposed email addresses to KELA’s database of leaked credentials shows that threat actors are also actively reusing their emails across different websites, even after the websites are compromised and their user database is exposed.
KELA has chosen to look at the top 10 actors active on RaidForums based on the number of messages they posted on the forum (excluding the forum’s administrators). All of them posted around 3000-5000 messages and appeared in the leak, being registered on the forum between April 2015 and October 2019.
Out of these actors, four had their registration emails exposed in some form, either as a part of big credentials compilations or — more interesting — included in more focused breaches, usually related to the hacking communities. Such as:
- Nulled. In 2016, Nulled, a well-known cracking community, was dumped and posted in rival communities. The database dump posted contained almost 600,000 usernames alongside MD-hashed passwords, emails, IP addresses, and thousands of private messages between forum members.
- DemonForums. In 2016, the database of demonforums.net, an underground community dedicated to hacking activities, was breached. The database included emails, passwords, and usernames of the forum’s users.
- CrackingItaly. In April 2017, a threat actor shared a database of the hacking community CrackingItaly which was allegedly breached in January of the same year. The leak exposed over 18,100 unique records, and includes users’ email addresses, IP addresses, usernames, and BCRYPT-hashed passwords with salt.
- OGUsers. The forum was breached three times. In May 2019, the account hijacking and SIM-swapping forum OGUsers was breached and over 100,000 of its users were affected. The data included emails, usernames, and hashed passwords. In April 2020, the exposed data included email and IP addresses, usernames, private messages, and passwords stored as salted MD5 hashes. A total of 200,000 email addresses across user accounts and other tables were leaked. In April 2021, the data included 350,000 entries, with emails, user names, MD5 or argon2id hashed passwords with salt, birth dates, and more.
- Void.to. In June 2019 the leaks dedicated forum void.to was breached and 86,312 records were leaked. The database includes website activity, usernames, emails, passwords, website data, and user private messages.
- CardingMafia. In March 2020, a threat actor shared the database of carding forum Carding Mafia. The data leak exposed over 290,000 records, and includes members’ email addresses, usernames, instant messaging IDs, DOBs, IP addresses, and MD5-hashed passwords.
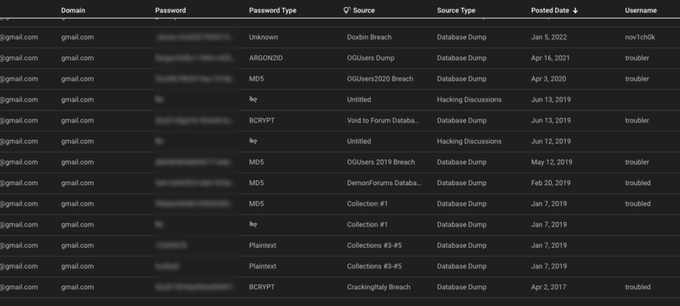
For example, a user ‘troubled’, registered on RaidForums in September 2016 with an email address hosted on Gmail, had the same email address leaked in April 2017, in the CrackingItaly breach. The email in this leak was associated with the same username. Once something is leaked, it can never be erased — and through the next year, this email was exposed as part of Collections #1-5, aggregated credentials compilations containing billions of records.
However, the actor was not bothered by that and continued to use the same email address with the same or slightly different username (troubled or troubler) on DemonForums, OGUsers, and Void.to. Logically, the same details were also circulating in Telegram channels sharing databases.
Part of the leaks containing the email address for troubled, as seen on KELA’s platform
Another user, called ‘Sunsingerlock’, registered on RaidForums in June 2018 with a Gmail email address, two years after the same address was leaked in the Nulled breach. Interestingly, the actor himself was commenting on the breach, saying “poor old nulled. Pity for the site.” While in this case, it is possible that the user could get access to a compromised email and use it to try to hide their footprints, though it is hard to be proved. Nevertheless, the actor used the same email to register on OGUsers and DemonForums, linking him to additional usernames (‘RighteousTwizz’ and ‘TroubledGary’). KELA has also already found that the user migrated to Breached under a different username, ‘Dredgen Sun’, once RaidForums was taken down.
Based on cybercriminal chatter, the two aforementioned users did not actively sell or leak noteworthy information (though they were interested in buying or downloading some of the illegally obtained data). One can assume that only unsophisticated users like these two could have continued to use exposed emails, tying up their multiple identities into one. However, the most skilled cybercriminals were known to make the same mistake, and that’s why the RaidForums database can be valuable in further investigations.
With almost 479,000 records leaked, the RaidForums leak is one of the biggest leaks affecting the cybercrime community. Having attracted cybercriminals over several years with its data breach-oriented approach, the RaidForums database will prove itself useful for researchers and law enforcement for years to come.
The database is available on KELA’s platform through a free trial via the following query.