Understanding the Different Types of Cyber Adversaries
Cyber adversaries come in various forms, each with unique tactics and motivations. Understanding these threats, from financially driven cybercriminals to insiders, is essential for securing your organization.
Published May 25, 2025

Cyber adversaries come in many shapes and sizes, each with its own set of tactics, motivations, and objectives. Some are driven by financial gain, like cybercriminals, while others are motivated by political, ideological, or personal reasons, such as insider threats.
Understanding the diversity of these threats is crucial for developing a comprehensive security strategy. In this blog, we will explore the different types of cyber adversaries, their methods, and how they can impact your organization’s security.
» Ensure your cybersecurity is up to standard with KELA
What Is a Cyber Adversary?
In modern cybersecurity, a cyber adversary is a malicious actor who seeks to exploit vulnerabilities in systems and networks to achieve specific goals. These adversaries can range from individuals to organized groups, including cybercriminals, hacktivists, and even state-sponsored actors.
A cyber adversary's motivations can include:
- Financial gain
- Espionage
- Sabotage
- Intellectual property theft
- Disruption of operations
Identifying and understanding the behavior of cyber adversaries is crucial for implementing effective defense strategies for several reasons, such as situational awareness, understanding the TTPs of adversaries, threat modeling, and a proactive approach to effective mitigation.
» Discover how KELA’s Threat Actors Hub can help you uncover your adversaries
6 Types of Cyber Adversaries
1. Nation-State Attackers (APTs)
Nation-state attackers, driven by political motives and espionage, target governments, critical infrastructure, defense, technology, and research sectors.
Examples
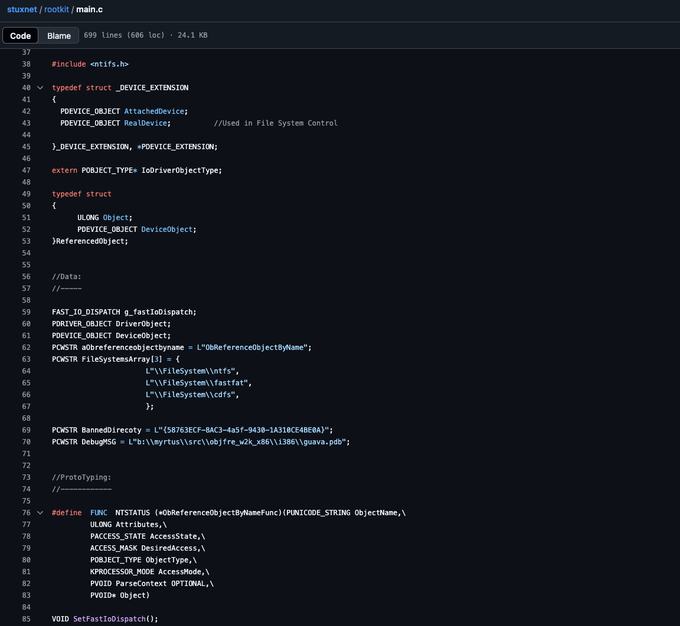
- Stuxnet: A sophisticated computer worm discovered in 2010 that targeted Iran's nuclear program. It's believed to be a nation-state attack, likely a joint effort, that used multiple zero-day exploits to infect programmable logic controllers (PLCs), causing the centrifuges to malfunction.
- Hafnium: A series of zero-day exploits targeting Microsoft Exchange servers discovered in early 2021. Attributed to a Chinese state-sponsored hacking group, Hafnium allowed attackers to access email accounts, install backdoors, and steal data from numerous organizations worldwide.
Tactics
These well-resourced groups, often operating within government structures, leverage secure communication channels. In addition to custom malware, nation-state attackers aiming for military, economic, or political gain use a variety of techniques, such as:
- APTs: Sophisticated, stealthy cyberattacks that aim for long-term infiltration and data exfiltration rather than quick, smash-and-grab attacks. They are designed to remain undetected for extended periods of time.
- Spear phishing: Highly targeted form of social engineering attack using crafted emails or messages that appear to be from trusted sources. While traditional phishing casts a wide net, spear phishing focuses on specific individuals or organizations.
- Zero-day exploits: Take advantage of previously unknown vulnerabilities in software or hardware. These vulnerabilities are called "zero-day" because the software vendor or developer has zero days to patch the flaw before it's exploited.
Defense Strategies
- Advanced network monitoring: Continuous, real-time monitoring of network activity to detect anomalous behavior, suspicious traffic patterns, and indicators of compromise (IOCs) that might suggest an ongoing or imminent attack
- Layered security: This approach assumes that no single solution is foolproof and implements multiple layers of security controls to protect assets.
- Threat intelligence sharing: The exchange of information about cyber threats between organizations, industries, and even governments. This shared information can include IOCs, TTPs, and information about specific threat actors.
» Learn how to prevent phishing attacks before they catch you
2. Cybercriminals
Cybercriminals, driven by financial gain, target organizations holding valuable data (like banks and retailers) as well as individuals with weak passwords and compromised accounts.
Tactics and Examples
Cybercriminals work alone or in groups, using underground forums and dark web marketplaces to implement various cyberattacks, including:
- Phishing: A social engineering strategy that attempts to obtain sensitive information (usernames, passwords, & credit card details) by masquerading as a trustworthy entity (bank, social media site, coworker, etc.).
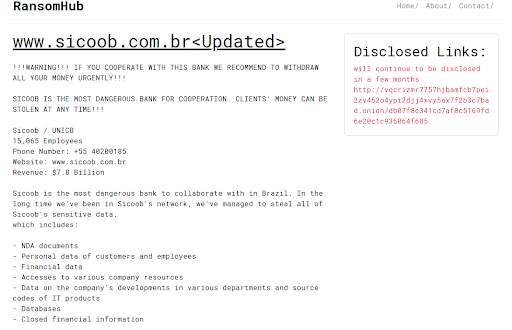
- Ransomware: A type of malware that encrypts a victim's files or blocks access to their computer system, demanding a ransom payment to restore access.
- Trojans: Malicious software disguised as legitimate programs that trick users into downloading or installing them, unknowingly infecting their systems.
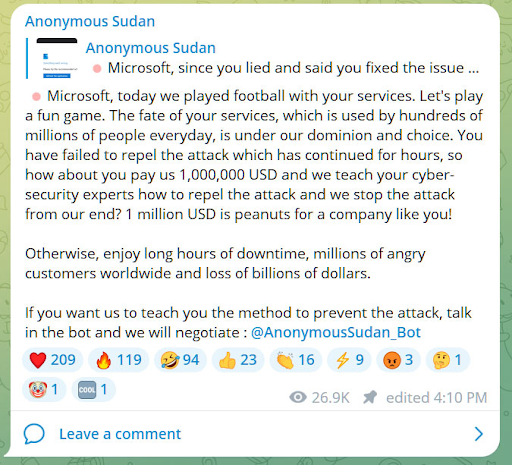
- DDoS attacks: An attack that floods a target website or network with traffic and overwhelms the target's resources, making it unavailable to legitimate users.
Defense Strategies
- Firewalls and antivirus software: These act as barriers between your network and the outside world (or between different parts of your network), blocking unauthorized access, detecting and removing malware, and scanning files, programs, and network traffic continuously.
- Regular backups and updates: Installing security patches and updates for your operating systems, applications, and hardware is essential to fixing known vulnerabilities before they are exploited. Creating copies of your important data and storing them separately can help mitigate the fallout of a ransomware attack or data loss.
- Security training: Educating employees and users about cybersecurity best practices, especially for popular attack methods like phishing and other social engineering tactics, is essential. Training should cover topics like password security, safe browsing habits, and how to identify suspicious emails and other contact points.
- Incident response plans: A documented set of procedures that an organization follows when a cybersecurity incident occurs. The plan should outline roles and responsibilities, communication protocols, steps for containing the incident, and procedures for recovery.
» Worried about security? Here are the reasons you need cyber threat intelligence
3. Hacktivists
Hacktivists are motivated by political, social, or religious beliefs, targeting governments, corporations, and organizations considered unjust. Their aim is to promote their ideals, destabilize the supposed oppressors, and raise awareness.
Tactics and Examples
These decentralized groups often take advantage of existing tools coordinated through social networks to achieve maximum impact. In addition to DDoS attacks, other common tactics include:
- Website defacement: Exploiting vulnerabilities in a target website to replace the existing content with messages, images, or videos that promote their cause or criticize the target.
- Data leaks (doxing): Releasing confidential or sensitive information to the public. This can include personal details, internal documents, emails, or financial records.
- Anonymous attacks: Defamatory cyberattacks carried out with the goal of maintaining anonymity. Hacktivists often use tools and techniques (proxy servers, VPNs, etc.) to mask their identities and locations, making it difficult to trace the attack back to them.
» Learn more about infostealers
Defense Strategies
- Monitoring online activity: Actively monitoring online platforms, social media, and forums (by tracking hashtags and keywords) for mentions of your organization, discussions about potential attacks, or leaked information. Additionally, consider using social listening tools and cyber threat intelligence platforms like KELA.
- Robust system maintenance: Regularly patching vulnerabilities, updating software, and performing security audits to ensure that systems are secure and up-to-date.
» Understand how to prepare your organization for the future of cybercrime
4. Terrorist Groups
Terrorist groups leverage online platforms to advance political or social agendas through intimidation and fear, similar to hacktivists.
Tactics and Examples
Terrorist groups target governments, militaries, critical infrastructure, and symbolic organizations. Their tactics include DDoS attacks, defacement, doxing, and hit lists, often spread through social media. They use the internet for recruiting, training, and planning attacks by communicating through social networks and encrypted channels
Examples include:
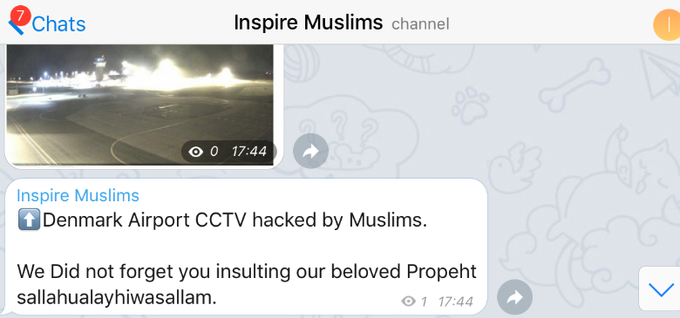
- Airport website defacement
- Military information dissemination
- Online recruitment
Defense Strategies
In addition to monitoring social media and other online activity, proactive strategies include:
- Employee threat identification training: Training employees to recognize and report suspicious behavior, including potential signs of radicalization or involvement in cyber terrorist activities. Ensure clear reporting channels and written procedures for employees to follow.
- Collaboration with authorities: Establishing and maintaining close working relationships with law enforcement agencies, intelligence communities, and other relevant authorities. This includes sharing threat information, coordinating incident response efforts, and participating in joint exercises.
5. Insiders
Insider threats are those committed by individuals who are affiliated with, or work for, a particular organization. They can occur for a variety of reasons, including financial gain, ideological discontent, personal motives, or accidental mistakes.
Tactics and Examples
Insiders target industries that handle sensitive data, like finance, technology, healthcare, and government. They use legitimate credentials to access and steal data or intellectual property, install malware, exploit privileges, and manipulate others.
Their internal position grants them access to the system, and they may use internal or external channels for communication.
Defense Strategies
In addition to security training and regular audits, defensive strategies for insider threats include:
- Robust access controls: A set of security measures designed to restrict access to sensitive data and systems based on the principle of least privilege. This means that users are only granted the minimum level of access necessary to perform their job duties, and goes hand in hand with tactics like multi-factor authentication (MFA).
- User activity monitoring: Monitoring and analyzing user behavior to detect anomalous activity that might indicate an insider threat. UAM systems track user logins, file access, data transfers, and other actions to establish a baseline of normal behavior.
» Now that we've explored the various types of cyber adversaries, discover how a threat intelligence analyst can help you stay ahead
Enhancing Security With KELA Cyber
Cyber adversaries are diverse and complex, each motivated by different goals and equipped with unique methods of attack. From financially-driven cybercriminals to politically-motivated hacktivists and the insider threats that often lurk within organizations, understanding these different adversaries is crucial in strengthening your security posture.
With the KELA Cyber platform, you can identify cybercriminal discussions in targeted Deep Web forums and credential leaks, giving you a clearer understanding of your organization's threat landscape. The platform offers greater visibility into threats that could harm your company's finances and reputation.
» Get started for free with KELA and stay ahead in cybersecurity