Hackers’ Wishlist: The 5 Most Targeted Entry Points
Published June 17, 2024.

In the ever-evolving landscape of cybercrime, one truth remains constant: valid credentials are the golden ticket. In 2023, corporate credentials became the go-to method for compromising networks, fueled by a booming cybercrime ecosystem overflowing with stolen logins. This easy access is further bolstered by a surge in infostealer-related activity (up 266% in 2023) (1).
This begs the question: what are hackers looking for when they buy these credentials? At KELA, we analyzed activity on cybercrime forums to identify the most targeted corporate access points. This blog dives into this data, revealing the top targets and, more importantly, how threat actors obtain stolen credentials to compromise them.
Glossary
Before we begin, let’s clarify some key terms that will be used throughout this blog:
- Information-stealing malware (also known as infostealer) is designed to steal sensitive information, such as browser-saved credentials and personal details, from an infected device.
- Bots are devices infected by information-stealing malware.
- Logs are data and browser-saved information stolen from these devices.
InfoStealer Logs: A Goldmine for Attackers
Infostealer malware logs have proven to be a valuable source of information for threat actors aiming to attack organizations. As many employees store their passwords directly in their web browsers, both on corporate and personal devices, this habit poses a significant risk when an infostealer manages to infect their systems. The malware steals corporate valid accounts, such as access to customer relationship management systems, RDP and VPN sessions, cloud services, and various other enterprise resources, and enables attackers to access sensitive resources. (2)
To obtain such accounts, threat actors do not necessarily need to launch and manage an information-stealing campaign. They can simply buy corporate credentials either on dedicated auto shops, such as Russian Market, through Telegram “clouds of logs,” (3) or on different cybercrime forums via communicating with specific sellers, such as initial access brokers. Cybercrime chatter gives defenders visibility into what corporate resources are in demand by threat actors aiming to attack organizations.
Threat Actors Shopping List
KELA has observed multiple actors that specify their interest on hacking forums via posts intended for cybercriminals engaged in information-stealing campaigns. Such posts are usually titled “Buying my links in your logs,” ”Buying corp access from logs,” or ”Buying logs per request” and include:
- A statement that an actor is ready to buy credentials to corporate resources from information-stealing malware logs
- A list of specific strings in compromised URLs they are interested in (usually authentication page URLs, such as <…>/+CSCOE+/logon.html)
- A list of countries in which a potential victim organization should be located
- An indication that an actor is interested only in “unique logs” (meaning not logs that were put up for sale on auto shops or as part of cloud-based services)
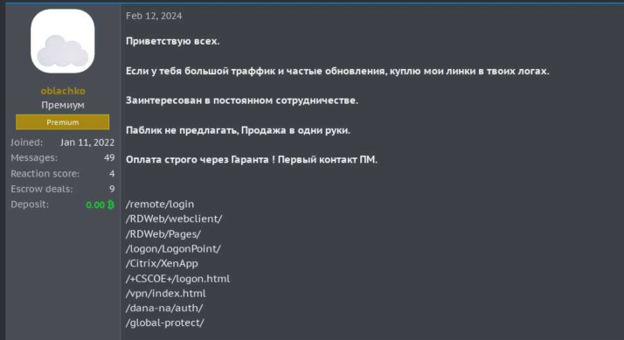
“Hi all. If you have a lot of traffic and frequent updates, I will buy my links in your logs. I am interested in permanent collaboration. Do not offer public. Sell one hand. Payment strictly through a middleman! First contact via DM.”
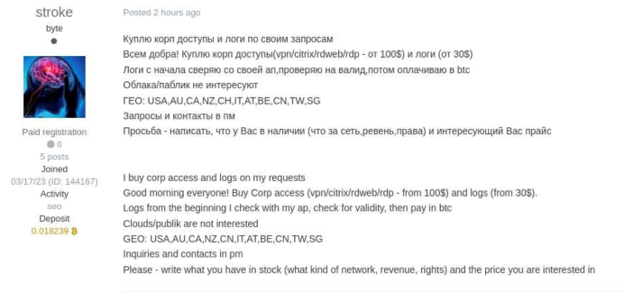
Threat actors on different cybercrime forums looking to buy corporate credentials from logs
The screenshots above provide examples of how threat actors operate on cybercrime forums to buy illicit access to corporate systems. The main purpose of such posts is:
- to gain unique credentials (as opposed to clouds of logs where logs are available to all the subscribers)
- To gain these credentials at scale (as opposed to auto shops where they should be bought one by one)
The actors’ interest in specific strings has allowed KELA to identify the most targeted corporate resources.
High-Value Targets: Most Frequently Targeted Access Points
KELA analyzed thousands of posts of threat actors who regularly expressed interest in specific resources in 2023-2024. For each threat actor, KELA took only one post indicating their interest (as many of them periodically repost the same information to find new partners) and extracted the strings that were mentioned.
Based on the analysis, the top five resources threat actors mentioned were associated with:
- Various Citrix remote access products, such as Workspace, Virtual Apps and Desktops, Gateway: based on strings /citrix/, citrixcloud, citrixportal, /vpn/tmindex.html, /LogonPoint/tmindex.html and similar
- Cisco’s VPN, such as WebVPN and AnyConnect: CSCOE, /+cscoe+/ and similar
- Pulse Secure VPN: /dana-na/
- Microsoft Remote Desktop Web Access: /rdweb/ and similar
- GlobalProtect by Palo Alto Networks: /global-protect/
In general, there is a significant focus on VPN and remote desktop-related strings, with mentions of generic strings. This indicates that VPN and remote desktop solutions are prime targets for threat actors due to their widespread use in providing remote access to corporate networks.
Some strings were generic or widely used across multiple platforms (such as /portal/, /secure/), indicating a broad interest in different entry points and services that might offer access to valuable data. On average, each threat actor had a list of 16 strings per post. However, some of them said they were ready to buy all kinds of remote access. The maximum number of strings listed by one actor was 42. Therefore, KELA assumes that threat actors intend to acquire access to more targets instead of focusing on one initial access vector associated with one specific solution.
Using Corporate Credentials for Attacks
Once acquired by threat actors, compromised corporate credentials enable attackers to perform lateral movement within networks, deploy malware, access sensitive data, and ultimately steal information, disrupt systems, conduct fraud, and more.
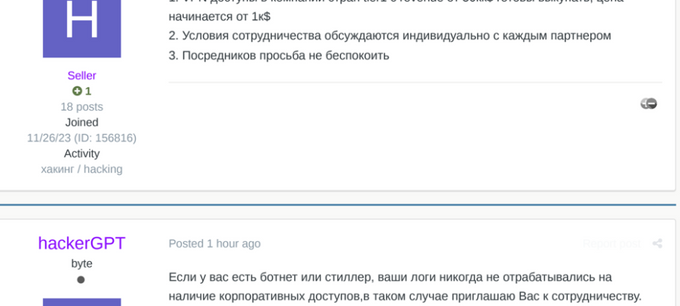
For example, one of the actors looking for corporate access from logs, ‘hackerGPT’, manages a team that aims to steal sensitive information from compromised networks. They claim: “We position ourselves as data hunters. Our goal is NDA documentation and other [information – KELA]. Due to the lack of material, we decided to go public in order to find several partners who could provide our team with the necessary amount of access to corporate networks.”
In his other posts, this actor is recruiting skilled penetration testers and mentions unique software they have, most likely referring to custom malware. Buying corporate access from logs appears to be just one way for this team to gain initial access, as they have been also looking to cooperate with botnets.
A few of many posts, in which hackerGPT looks for corporate access, specifying they are ready to buy “VPN access to companies in countries tier1 with revenue from 50kk$, ready to buy starting from 1k$ price” and saying they are ready to cooperate “if you have a botnet or a stealer and your logs have never been processed for corporate access before”
Change HealthCare Hack
The recent hack of Change Healthcare (owned by UnitedHealth) shows exactly what’s at stake. UnitedHealth Group’s CEO confirmed that in a ransomware attack the company experienced in February 2024, the cybercriminals used stolen credentials to remotely access Change Healthcare’s Citrix portal, a remote access service that did not have multi-factor authentication (MFA). The attackers moved laterally through the compromised network and used the access to steal data over nine days before deploying the ransomware (4).
KELA has seen several instances where compromised credentials to Change Healthcare-owned resources, gained through information-stealing malware, were offered for sale or leaked on cybercrime platforms, with some of them appearing only a few days before the attack. While it is not clear if the actor used these credentials to attack the company, it is a possible vector that could be used.
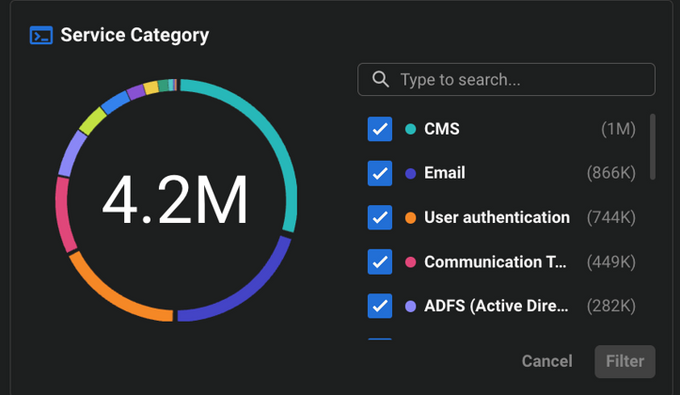
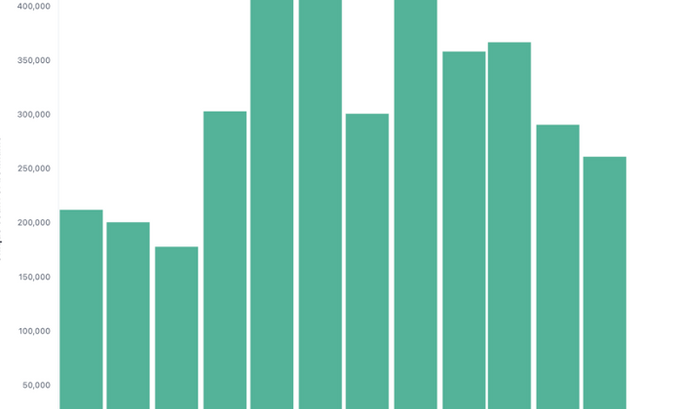
Threat actors seeking to attack high-value targets understand the value of stolen corporate credentials and are likely to use the vast amount of them provided by different actors active on cybercrime platforms. Only in the last year, KELA has ingested over 3,7 million bots, illustrating the supply for information from machines infected with info-stealing malware. The most popular corporate entry points, compromised by these infections, include CMS, email, user authentication, communication tools and ADFS-linked services.
Most popular corporate resources among stolen, credentials to which has been gathered through infostealers and ingested by KELA
Amount of bots KELA ingested in June 2023-June 2024
Conclusion and Recommendations
With increasing activity of infostealers and adaptation of the cybercrime ecosystem allowing the distribution of the stolen information, a supply chain of cybercriminals is likely to rely on compromised credentials to corporate resources, especially the ones associated with remote access and, more specifically, VPN solutions.
Therefore, it’s crucial to implement measures to protect sensitive services:
- Multi-factor authentication (MFA): Implement MFA across all company accounts to ensure that even if passwords are compromised, unauthorized access is significantly more challenging.
- Regular password updates: Enforce a policy that requires employees to update their passwords periodically. This practice reduces the risk of exposure of credentials in case of a breach.
- Employee awareness training: Educate employees about the risks and threats of phishing attacks and social engineering campaigns that can deliver information-stealing malware.
- Disable ex-employees’ credentials: Implement a protocol and process to delete ex-employees’ credentials immediately upon their departure.
- Monitor cybercrime platforms: Monitor cybercrime activities to identify compromised accounts pertaining to company assets.
References:
2. Defender-in-the-middle: How to reduce damage from info-stealing malware
3. Telegram Clouds of Logs – the fastest gateway to your network
4. Testimony of Andrew Witty, Chief Executive Officer, UnitedHealth Group