What Is TPRM? 2025 Guide With Best Practices
Third-party risk management is essential for identifying, evaluating, and mitigating cybersecurity risks that can be acquired through external entities such as vendors, suppliers, and service providers.
Published May 15, 2025

The interconnected digital landscape of the modern world requires businesses to rely heavily on third-party vendors and service providers. While these partnerships offer numerous benefits, they also introduce significant cybersecurity risks. Every vendor with access to your systems or data represents a potential entry point for cyberattacks. Around 61% of companies have been breached through a third party in events similar to the SolarWinds cyberattack that allowed a threat actor to remotely exploit the networks and systems of SolarWinds’ customers who had downloaded compromised software updates.
This is why TPRM (third-party risk management) is more critical than ever. This article covers everything you need to know from core components to best practices.
» Skip to the solution: Try KELA for free
What Is TPRM?
TPRM (third-party risk management) is a fundamental process for identifying, evaluating, and mitigating cybersecurity risks that can be acquired through external entities such as vendors, suppliers, and service providers.
Some of the third-party threats include:
- Data breaches
- Regulatory violations
- Financial instability
- Operational failures
- Reputational damage
TPRM should be considered in an organization's defense strategies due to the increasingly common adoption of outsourcing that comes with a primarily digital world. It's a crucial aspect of business operations, involving various aspects such as cybersecurity, regulatory compliance, data privacy, and vendor relationships.
» Learn more about the cybercrime threats coming in 2026
Types of TPRM
- Cybersecurity risk management: Mitigating risks such as data breaches, malware incidents, and cyber attacks originating from third parties.
- Operational risk management: Minimizing service interruptions and supply chain delays caused by the actions of third parties. Assessment of a supplier's operational resilience is necessary before contracting.
- TPRM with a focus on compliance: Ensuring adherence to industry standards, avoiding legal penalties for third-party non-compliance, regularly assessing suppliers, and keeping up to date with regulatory requirements.
- Financial risk management: Addressing the possibility of a supplier failing to fulfill financial obligations (leading to losses for the company) and monitoring changes over time to verify the supplier's financial stability while protecting financial results.
- Reputational risk management: Mitigating the risk that a supplier's actions could damage your company's image and customer confidence while regularly monitoring suppliers and aligning them with your company's values and prevention strategies.
Core Components of a Robust TPRM Framework
- Third-party identification: This involves creating a comprehensive inventory of all vendors, suppliers, and partners that have access to your systems or data.
- Risk assessment and mitigation: This step assesses the potential cybersecurity risks posed by each third party and develops strategies to minimize or eliminate those risks.
- Continuous monitoring: This involves ongoing surveillance of third-party security practices to detect and respond to any changes or emerging threats.
- Supplier risk management: This is the process of managing the risks associated with your suppliers. It involves working with your suppliers to make sure that they are maintaining adequate security protocols.
- Integration: This is the process of incorporating TPRM into your overall cybersecurity framework and integrating processes with your existing security tools and systems.
These components work together to strengthen an organization's security posture, identifying weak links in the supplier network and providing continuous oversight.
» Confused? Here's our guide to navigating third-party cyber threats
Real-World Examples of Third-Party Cybersecurity Incidents
- Snowflake breach: Threat actors exploited stolen credentials—many harvested via infostealer malware—to access over 165 Snowflake customer accounts lacking multi-factor authentication, leading to significant data breaches at organizations like Santander Bank and
- Ticketmaster. CDK Global ransomware attack: A ransomware attack disrupted CDK Global's systems, causing widespread operational disruptions to around 15,000 car dealerships that they supply.
- Exploitation of a zero-day vulnerability in MOVEit: Hackers exploited a previously unknown vulnerability in the MOVEit file transfer software, leading to data breaches at numerous organizations that used the software.
- Change Healthcare Ransomware Attack: A ransomware attack severely impacted Change Healthcare, a major healthcare technology company, disrupting prescription processing and other critical healthcare services.
» Understand these threats better with our guide to ransomware
Best Practices for Maintaining TPRM
1. Implement TPRM-Focused Security and Monitoring Tools
Integrating technology into the risk assessment and threat intelligence process optimizes data analysis, enabling faster and more accurate risk identification.
Some of these tools and technologies include:
- Risk assessment and scoring tools: Automate the evaluation of vendor risks based on predefined criteria and scoring models.
- Supplier onboarding and offboarding automation: Streamline the process of adding and removing vendors while ensuring security protocols are followed.
- Contract management and compliance tools: Manage vendor contracts and track compliance with security and regulatory requirements.
- Reporting and incident response tools: Generate reports on vendor risk and facilitate swift response to security incidents.
- Data analysis and visualization: Provide insights into vendor risk through data analysis and visual dashboards.
- Unified supplier data platform: Centralize vendor information for a comprehensive view of supplier relationships and risks.
- Supplier portals: Provide a secure platform for communication and data exchange between organizations and their vendors.
- Blockchain technology: Enhance data security and transparency in supplier relationships through decentralized ledgers.
» Not convinced? Here are some more reasons you need cyber threat intelligence
2. Use AI and Machine Learning for Automation
The TPRM tools listed above simplify the complex process of supplier risk management, including assessment, monitoring, and mitigation. They can be further improved through the use of AI and machine learning to automate risk assessments and supplier monitoring at a much faster rate than human management.
» Did you know? Cybercriminals now exploit generative AI
3. Understand Key Regulations and Compliance Standards
It's essential to stay informed about relevant regulations and industry standards so that you can regularly update third-party contracts to ensure compliance with regulatory requirements and avoid penalties. These frameworks and standards provide a baseline for assessing and managing the risks associated with third-party vendors.
The main structures, regulations, and compliance standards include:
- NIST Cybersecurity Framework (CSF): Provides guidelines for organizations to assess and manage cybersecurity risks, including those from third parties.
- ISO 27001: An international standard with a formal certification through an independent audit for information security management, requiring organizations to implement controls to protect data. This extends to ensuring third parties meet security standards.
- GDPR: Mandates that organizations protect the personal data of EU residents, holding them accountable for data handled by third-party processors.
- SOC 2: Reports on a service organization's controls related to security, availability, processing integrity, confidentiality, and privacy, providing assurance of third-party security practices. It involves an audit and the issuance of a report by an independent auditor.
- DORA: A European Union regulation that focuses on the information and communication technology (ICT) risk of financial entities. A large portion of DORA focuses on how financial entities manage their ICT third-party risk.
- PCI DSS: Requires organizations that handle credit card data to meet security standards, including ensuring that third-party service providers comply with PCI DSS requirements. It involves an audit and the issuance of a report by an independent auditor.
4. Make Use of the Best Risk-Scoring Methodologies
Some organizations combine different methodologies to classify and prioritize supplier risks.
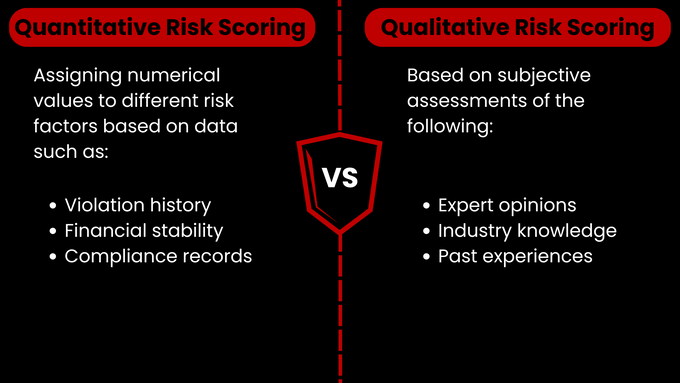
For example, quantitative methods involve assigning numerical values to different risk factors based on data such as violation history, financial stability, and compliance records. On the other hand, qualitative methods are based on subjective assessments of expert opinions, industry knowledge, and past experiences.
To prioritize suppliers effectively, organizations map them out in a matrix to determine which third parties would significantly affect your business if they were compromised.
The following strategies can be established for correct implementation
- Risk heat map: A visual representation of risks, typically using a grid or matrix. The axes represent the probability (likelihood) of a risk occurring and the impact (severity) of that risk. By plotting risks on this map, you can quickly identify high-priority risks which appear in the "red" or "hot" zones of the map.
- Central risk register: A repository for all identified risks, their assessments, and mitigation plans. It serves as a single source of truth, ensuring that risk information is consistent and accessible to relevant stakeholders. By centralizing the results of risk scoring, you can filter out irrelevant data and focus on key areas of concern. This helps to streamline risk management processes and improve decision-making.
- Scoring methodologies: Using standardized scoring methodologies like NIST and FAIR (Factor Analysis of Information Risk) ensures that risk assessments are objective and consistent. This might involve assigning numerical scores to various risk factors based on predefined criteria.
Key note: Supplier collaboration is essential because obtaining accurate information from them is key to scoring their risk. Working with the supplier to get that information and help them understand the importance of the process, improve the quality of the data received, and boost the effectiveness of your TPRM strategy.
5. Maintain Documentation and Communication
A crucial aspect of TPRM is ensuring that your vendors, suppliers, and employees understand the necessary rules and regulations and follow them to the same degree that you do. The simplest way to do so is to communicate this to them and have everything in writing. Consider the following:
- Establish clear communication protocols and incident response plans to ensure swift action when issues arise, limiting damage and preserving business continuity.
- Ensure you have a contract for each third party you interact with that clearly defines security obligations, data protection protocols, and performance metrics to establish a legal framework for risk management.
- Clearly communicate risk policies to suppliers to avoid confusion and ensure effective risk management.
Guarantee Effective TPRM With KELA
The 6th best practice for guaranteeing TPRM is to work with a professional cyber threat intelligence platform like KELA. Third-party risk management is a necessity in today's complex digital environment, but it can be extremely complicated to get right without the right level of expertise and understanding.
Tools like KELA leverage threat intelligence feeds and automated vulnerability scanning to offer a powerful advantage. By providing real-time alerts on critical issues like credential leaks and unauthorized access sales through proactive continuous monitoring, KELA empowers businesses to maintain a vigilant watch over their suppliers' security posture. Ultimately, a strong TPRM program, supported by cutting-edge technology, is the best defense against the ever-evolving landscape of cyber threats.
» Ready to begin? Contact us to learn more about our third-party intelligence