Akira Ransomware Gang Evades Decryptor, Exploiting Victims Uninterruptedly
Published August 1, 2023.

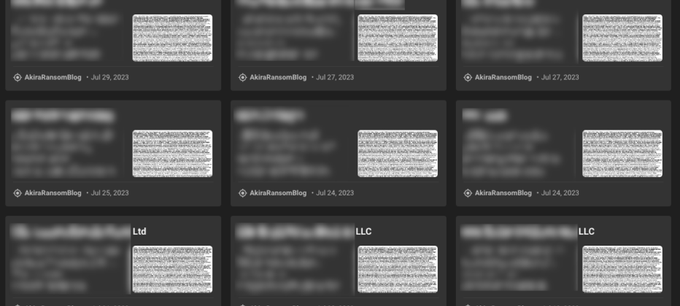
Despite the decryptor for the Akira ransomware that was released at the end of June 2023, the group still seems to successfully extort victims. In July, we observed 15 new victims of the group, either publicly disclosed or detected by KELA in the course of their negotiations.
It seems that some of the July victims were infected with the Linux version of the Akira ransomware, based on the list of stolen files. However, at least for some victims, the infected machines were running on Windows.
Akira’s latest victims as seen on KELA’s Cyber Threat Intelligence platform
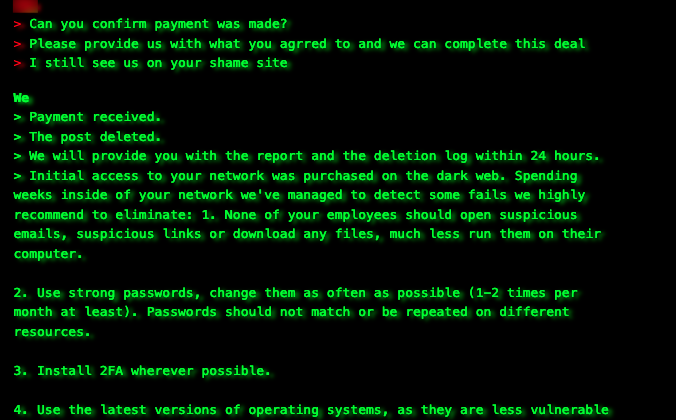
For example, a law firm in the US that was discovered as a victim in June 2023, has paid the ransom on July 13. Interestingly, during the course of negotiations, Akira disclosed the victim’s name on the blog; after that, the victim still continued to participate in negotiations.
US law firm pays ransom and receives recommendations
The company claimed that due to the damage caused by the publication and the fact they no longer have the need for the decryptor (probably due to the decryptor release), they are ready to pay only USD 75,000 instead of the initially requested amount of USD 165,000.
In exchange for the ransom, Akira disclosed that initial access to the company’s network “was purchased on the dark web.” Based on their recommendations, it’s possible that the initial access was through VPN. Akira also deleted a post about the victim from their website.
The case of the US law firm, which paid the ransom and seems to have only their Windows machines encrypted, illustrates that Akira actors can still continue to receive ransom for stolen data, even if the decryptor is no longer needed.
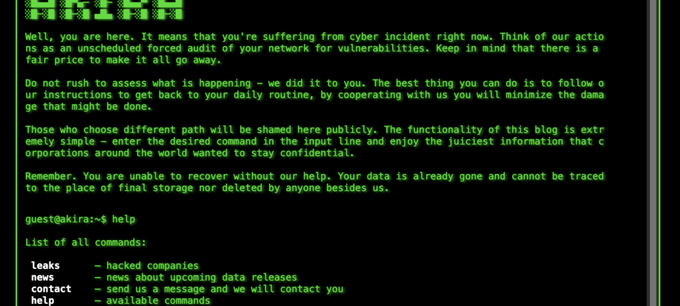
Akira ransomware blog
As mentioned Christopher Vincent, CRO of Halcyon: When decryptors are made public, a significant challenge arises as threat actors receive advance notice to modify their code. This means that decryptors released to the public usually have limited effectiveness against active threat actors, as they quickly adapt and evolve their techniques. As a result, the window of opportunity to neutralize ransomware attacks through public decryptors remains relatively short-lived.
Get notified about threats targeting your organization in real-time. Try KELA’s Cyber Threat Intelligence Platform for Free.