2025 Midyear Cyber Threat Recap: Evolving Tactics and Emerging Dangers
Cybercrime is surging in 2025, with record ransomware attacks, millions of infostealer infections, and faster vulnerability exploitation. KELA’s Midyear Threat Report outlines the key threats and urgent defenses needed.
Updated August 11, 2025

Over 3,600 ransomware victims. More than 2.67 million infostealer infections. The numbers speak for themselves. 2025 is on track to break new records in cybercrime. And it’s no coincidence, as infostealers are fueling the ransomware epidemic. As we hit the halfway point of 2025, KELA’s Cyber Intelligence Center reviewed the first half of the year and saw, unsurprisingly, that threats are intensifying and evolving at an unprecedented rate.
KELA’s 2025 Midyear Threat Report offers a deep dive into the key findings and analysis, as well as recommendations for preparing and responding to the persistent and evolving risks. Read on for a summary of the report.
» Strengthen your cybersecurity with KELA's expertise
Hacktivist Activity: Shifting Tactics and Geopolitical Tensions
Hacktivism in 2025 has been characterized by shifting communications platforms and more decentralized group behaviors. As geopolitical tensions escalate, hacktivist groups have adapted, expanding their communications to X (formerly Twitter) to avoid disruptions caused by platform takedowns. While many of these groups appear less active in the public eye, they remain a significant threat.
Key Highlights:
Increase in symbolic attacks: DDoS attacks, website defacements, and data theft have been popular tactics, often used to make political statements rather than cause direct harm.
Psychological warfare: The spread of disinformation and exaggerated claims has become a primary tactic to influence public opinion and shape narratives.
While these attacks are often unsophisticated, they can cause major operational headaches and reputation damage. The rise of "low-tech, high-volume" tactics, including DDoS campaigns, underscores the importance of investing in advanced DDoS protection and building robust incident response playbooks.
» Learn more about how hackers gain entry to your systems
Ransomware and Extortion: An Unstoppable Threat
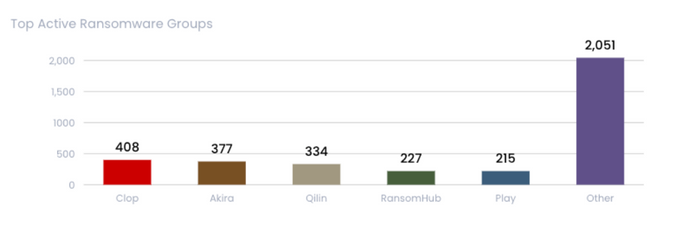
Ransomware remains one of the most dangerous and lucrative cyber threats of 2025. KELA tracked over 3,662 ransomware victims in the first half of the year, with the U.S. being the primary target, accounting for more than half of all victims. The trend toward multi-extortion tactics, combining data theft, credential resale, and DDoS threats, is on the rise.
Key Highlights:
- Growth of Clop: The Clop ransomware group saw a massive (2,300%) spike in activity, attributed to the exploitation of a vulnerability in Cleo software.
- Top sectors impacted: Manufacturing & Industrial Products was the most affected sector this year (18% of all victims), and Professional Services (16%) came in second. This is consistent with H1 2024.
- Supply chain attacks: Attacks targeting third-party vendors remain an effective tactic for ransomware groups, allowing them to infiltrate multiple organizations via a single access point.
» Learn more about how ransomware operators gain access
Infostealers: The Quiet Precursor to Larger Attacks
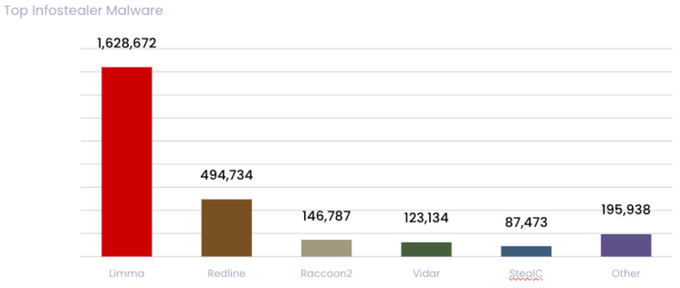
Infostealers are playing a critical role in the cyber threat landscape of 2025, acting as a gateway for more significant attacks such as ransomware and espionage. KELA observed more than 2.67 million machines infected by infostealer malware in the first half of 2025, compromising over 204 million credentials.
Key Highlights:
- Top infostealer strains: Lumma, Redline, and Racoon2 were responsible for 85% of all infections.
- MacOS under pressure: The Atomic macOS Stealer (AMOS) added a persistent backdoor, undermining the myth that Macs are safe from malware.
» Read more: Data breach or infostealer—what's the real culprit?
Emerging Vulnerabilities: Rapid Exploitation in a Noisy Landscape
2025 has seen a surge in the exploitation of newly disclosed vulnerabilities, with cybercriminals quickly weaponizing zero-day flaws and publicly disclosed CVEs. Vulnerabilities in widely used systems such as Ivanti Connect Secure and Palo Alto Networks’ PAN-OS were quickly exploited by attackers, underscoring the importance of timely patching.
Key Highlights:
- Rapid exploitation: Cybercriminals’ discussions around new CVEs appeared on average within one to two days following CVE disclosure, some of them even on the same day, and continued for months after disclosure.
- Increasing risks: Four out of the five most discussed CVEs on cybercrime forums in H1 have been confirmed as exploited in the wild.
» Make sure you know how threat actors breach and exploit your data
How Can Security Practitioners Prepare for the Rest of 2025 and Beyond?
As with years prior, the first half of 2025 continues to show that cybercriminals are agile, resourceful, and highly motivated. But how can organizations prepare? What steps do they need to take to strengthen their cybersecurity posture?
For KELA’s full list of recommendations and countermeasures, as well as more detailed insights into the current threats and their impact, check out KELA’s full 2025 Midyear Threat Report. You can also view the H1 related webinar on demand.
» Get started for free with KELA and strengthen your cybersecurity