Anubis: A New Ransomware Threat
Published February 25, 2025.

Recently, a new ransomware group, dubbed Anubis, emerged. Their official X (formerly known as Twitter) profile suggests they have been active since the beginning of December 2024. At the time of writing, KELA has observed representatives of Anubis on both RAMP (using the moniker ‘superSonic’) and XSS (using the moniker ‘Anubis__media’). Both users’ posts are written in Russian. According to the statement from one of their victims regarding a ‘cyber security incident’ on November 13, 2024, it may suggest that the group has been active since at least then.
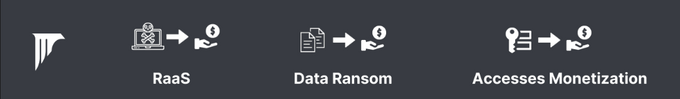
Interestingly, the group’s appears to not only use double extortion and work as ransomware-as-a-service (RaaS), but also employ other monetization models via additional , all within affiliate programs, such as, a data ransomware affiliate program, and an access monetization affiliate Program.
KELA assesses that Anubis’ operators may have been former affiliates of other ransomware groups or have experience with data extortion and ransomware-related activities, based on the actor’s statements regarding their ransomware capabilities and the informative, well-written investigative articles on their victims. Anubis appears to be an emerging threat, highlighting different business models employed by modern extortion actors.
Anubis’ business model
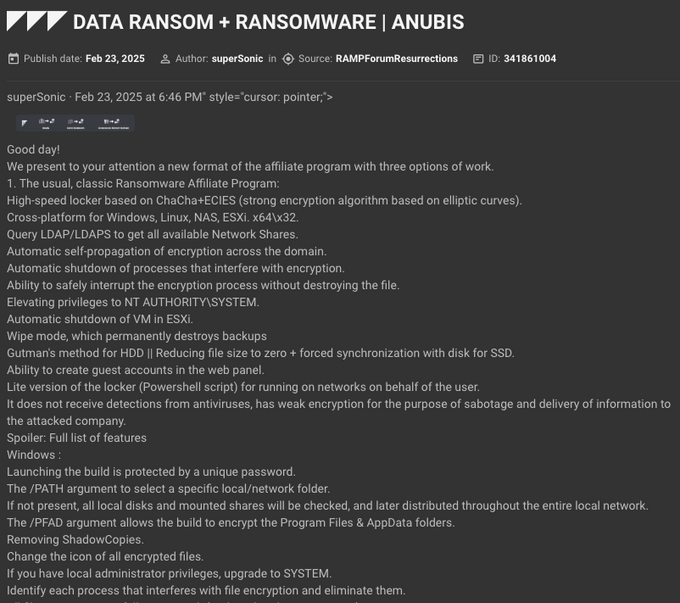
On February 23, 2025, the threat actor “superSonic” advertised a “new format” of affiliate programs on the RAMP cybercrime forum. All of their suggested revenue-share structures are open to negotiation for long-term cooperation.
Anubis’s affiliate programs are detailed below, highlighting the comprehensive monetization vectors they cover.
A screenshot of Anubis’s affiliate programs advertising post, presenting their monetization models
Anubis Ransomware – 80/20
This affiliate program offers a ‘classic’ ransomware-as-a-service (RaaS) model, providing affiliates with 80% of ransom share. Anubis details the following features of their ransomware:
- written in ChaCha+ECIES
- targets Windows, Linux, NAS, and ESXi x64/x32 environments
- elevates privileges to NT AUTHORITY\SYSTEM
- has the capability for self-propagation of encryption across the domain
- easily managed via a web panel
While not mentioned specifically, the RaaS program most likely provides affiliates with access to the publication of information on the Anubis blog to intimidate victims.
Anubis Data Ransom – 60/40
This affiliate program offers cybercriminals to monetizate sensitive data they have already stolen from companies using Anubis’ assistance. Anubise vouches to receive ransom payment through public exposure threats, providing affiliates with 60% revenue. The data must meet the following requirements: it must be exclusive (meaning it hasn’t been published anywhere on the Clearnet or Darknet before), the breach must be recent (no older than six months), and its content must be deemed ‘interesting for publication’.
Interestingly, in addition to the data leak marketplace, Anubis suggests a unique service including:
- After studying the data and agreeing on the terms, an ‘investigative article’ is written based on the stolen files’ and published in hidden mode on the blog (not visible on the main page of the blog and password protected).
- Putting pressure and threatening the victim company using ‘non-standard methods.’
- Informing entities affected by the leak, as well as ‘special authorities’ (such as GDPR, EDPB, HHS, OPC, ICO, OAIC, etc.) and clients, in addition to initially publishing the article on X and later releasing all the data.
Accesses Monetization – 50/50
This affiliate program offers Initial Access Brokers to provide corporate access credentials to Anubis in exchange for 50% revenue.
This service applied by Anubis on the given initial access includes:
- A deep dive into the victim’s data and understanding of the victim, in order to identify vulnerability points within its team, thereby increasing the pressure during the extortion stage.
- Detailed reports filled by Anubis in CryptPad tables (similar to Google Sheets, with live updates), provided to the affiliate and documenting the attack progress.
The access is required to meet the following criteria: the victim’s jurisdiction must be the US, Europe, Canada, or Australia, and the company must not have been attacked by ransomware groups in the past year Anubis states that they will not accept access from entities from the educational, governmental, or non-profit sectors.
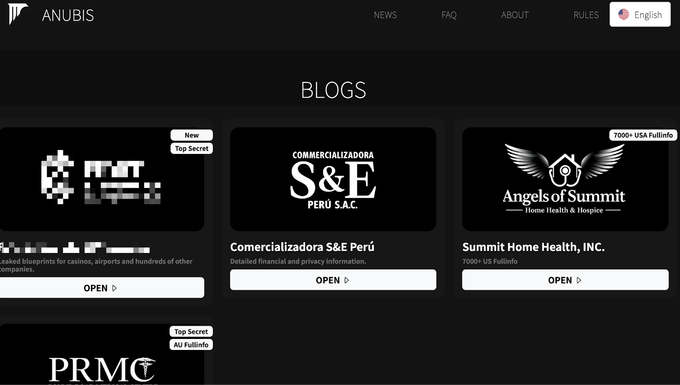
Onion Blog
Below is the homepage of the Anubis’ darkweb blog, with four victims claimed at the time of writing:
Screenshot of homepage of Anubis’ blog
Representatives
DarkWeb
Anubis’ users’ posts/comments on the forums are written in Russian, which may suggest the operators’ origin. At the time of writing, due to the lack of activity from both users on the forums, KELA couldn’t clarify the exact connection between the two users or the structure of Anubis.
superSonic – RAMP
KELA observed a user on the RAMP forum advertising Anubis’s affiliate programs on February 23, 2025. The user, superSonic, joined RAMP on September 13, 2024, with their first and only post being the one from February 23, 2025. In their forum signature, they include ‘ANUBIS RANSOMWARE BLOG’ along with its onion blog link. At the time of writing, the post does not have any comments.
Anubis__media – XSS
The user ‘Anubis__media’ on the XSS forum is specified in the contact details section of Anubis’s blog. They joined XSS on November 16, 2025, and at the time of writing, they have received 12 reactions on one thread in total.
KELA observed one of their posts, published on December 26, 2024, where they claimed to be publishing part of “about 7,300 full info of US medical clinic clients”, highlighting that the data wasn’t on sale or in public before, with samples.
The stolen data is offered via download link for free. First, part of the archive will be offered to the first 500 people. The rest of the full files will be given for free upon request via private message to 100 people.
X
KELA observed Anubis’s profile on X, which has been active since December 2024. At the time of writing, the profile has a very low number of followers and low traffic exposure rates for their posts.
Anibus’s profile page on X
At the time of writing, their posts section on X includes three victim claims: two first victims claimed on December 28, 2024, and the most recent on December 29, 2024.
Victims
Pound Road Medical Centre (PRMC)
Anubis’s first claim victim is Pound Road Medical Centre (poundroadmc.com.au), an Australia-based company from the healthcare sector.
The victim company published a statement about a ‘cyber security incident,’ observed by them on November 13, 2024. In the statement, they mentioned the potential exposure of contact information, health information, Medicare or pensioner cards, and other additional records.
Screenshot from PRMC’s statement informing about Cyber Security Incident
Summit Home Health
Summit Home Health (angelsofsummit.com), a Canada-based company from the healthcare sector, was claimed as a victim of Anubis on their X page on December 29, 2024. At first they posted ‘New Investigation: Massive Data Breach at Summit Home Health, Inc.’ followed by another post the same date including the hidden onion link with all the stolen data download option for free.
KELA observed that the user ‘Anubis__media’ posted stolen data from Summit Home Health on XSS on December 26, 2024, with identical data samples for free. Based on these dates, more than a month passed from the victim’s awareness of the attack to the free data leak, which was likely the time period for negotiations.
This instance sheds light on the group’s activity flow:
- First, Anubis gains access to the victim’s system or unique data (most likely, primarily through affiliates), and studies it in order to write a comprehensive article about the company. This article is first published via hidden page and later on their blog and also on their X account for public exposure.
- In parallel, negotiations with the victim occur. The victim receives a link for a hidden blog post with a download option for the stolen data, which Anubis threatens to publish on the blog. According to their post, ‘link to the negotiations is sent to the company by calling’.
- If negotiations succeed and an agreement is reached, the stolen data remains unpublished.
- If negotiations fail, the entire file tree and data of the victim is published, free to download.
Comercializadora S&E Perú
Comercializadora S&E Perú (sye.com.pe), a Peru-based company from the engineering & construction sector was claimed as victim by Anubis on their X page on December 29, 2024. Also with this victim, they first published their ‘investigation article’ and later the hidden blog link including a download for free of all the stolen data.
Fourth victim, claimed on February 25, 2025
KELA observed on February 25, 2025, a new victim claimed on Anubis’s blog. The victim is US-based from the Engineering & Construction sector. It is worth mentioning that at the time of writing, the claim of this victim is published only in Anubis’s blog and not appearing in their X page or posted by their representatives on cybercrime forums.
Anubis’ ransomware capabilities
The post, advertising Anubis’s affiliate program on RAMP, also includes the alleged technical capabilities of their ransomware.
A post showing part of Anubis’s ransomware capabilities (source: KELA platform)
At the time of writing, it is not possible to verify whether the claimed capabilities are actually present in Anubis’s ransomware. If true, this could suggest that Anubis operators have used malware code from other ransomware groups or developed it, having some knowledge in the matter. In addition, according to KELA’s analysis of Anubis’s blog, statements about their ransomware operations, and their published posts on victims, Anubis’s operators may be experienced individuals, possibly former affiliates of other ransomware groups. Finally, their detailed and informative content across all platforms, including their onion blog, may indicate operators with extensive hands-on experience in ransomware and data extortion.
All in all, this emerging threat may be a well-organized and knowledgeable group, potentially posing a significant risk to organizations due to their apparent expertise in ransomware operations and data extortion tactics. Notably, two of the four victims claimed by Anubis so far belong to the healthcare sector, highlighting the group’s potential focus on targeting critical industries.