No, OpenAI Wasn’t Breached—The Real Threat Comes from Infostealers
Updated February 10, 2025.

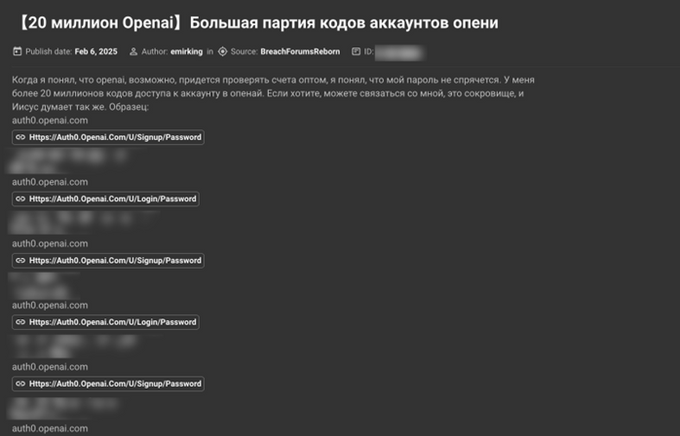
On February 6, 2025, the threat actor “emirking” posted on BreachForums they allegedly have access to “over 20 million account access codes in OpenAI.” The actor offered to BreachForums’ users to reach out to him if they are “interested”, possibly intending to sell these accounts. It is worth noting that the post is written in Russian; however, its wording suggests it is an automatic translation into Russian rather than being written by a native speaker.
Emirking joined BreachedForums on January 9, 2025 and wrote only one post besides the aforementioned one, claiming to have access to 50 thousand logs, listing a sample of 15 logs in the post (compromised accounts including URL, login and password details, 40GB of data in total). Both posts of the actor got very few comments from other users of the forum. The lack of activity of emirking making the assessment of their credibility, skill level and relations to other cybercrime actors challenging at the time of writing this blog. Interestingly, the OpenAI post has been deleted since, while the actor is still a member of BreachForums.
To assess the OpenAI credentials claim, KELA analyzed a sample shared by the actor, which included 30 compromised credentials related to OpenAI services—all containing authentication details to auth0.openai.com. These credentials were cross-referenced with KELA’s data lake of compromised accounts obtained from infostealer malware, which contains more than a billion records, including over 4 million bots collected in 2024. All credentials from the sample shared by the actor emirking were found to originate in these compromised accounts, likely hinting at the source of the full 20 million OpenAI accounts that the actor intends to sell. The actor’s first post on BreachForums, related to infostealer logs, strengthens the assessment.
Upon identifying matches, KELA conducted a deeper analysis of the infected machines, examining the infection date, malware family, and the source of the logs. Additionally, KELA assessed whether the email addresses used for OpenAI logins were registered for other services, which could indicate their validity and potential verification status.
Setting up the terms: infostealers
Before going into investigation results, it is worth clarifying the terms: infostealer operations are a rapidly evolving segment of the cybercrime landscape, with attackers continuously refining their methods to capture and monetize sensitive information. Infostealering malware is designed to infiltrate systems and steal sensitive data, such as login credentials, financial details, personal details, system and network information. Once installed on a victim’s system, they extract information from web browsers, password managers, and even clipboard data, with the type and scale of the data varying from one infostealer component to others.
Below is a map presenting the prominent infostealer malware families identified by KELA, such as Vidar, Lumma, StealC, MetaStealer, Redline and Raccoon2 (disrupted) among others. Most of them operate as Malware-as-a-Service (MaaS) — meaning that different cybercriminals gain access to the malware for a fee.
Once acquiring the infostealer builds as MaaS, a threat actor willing to specialize in credentials selling needs to successfully set up an infrastructure and collect compromised accounts on a wide scale, often using a team of traffers (related to the word “traffic,” referring to actors who have the means to infect multiple targets) to spread the infection.
The following stage is monetization, highly utilizing the dedicated cybercrime platforms that have evolved over the last few years. Stolen credentials are often sold on cybercrime forums and markets, either in bulk or as individual accounts, as well as through subscription services (so called “clouds of logs”). Sometimes they are freely shared across these sources, allowing other cybercriminals to take advantage of the data without direct transaction costs. This commodification of stolen information amplifies the scale of the threat, enabling continuous exploitation across various platforms.
Prominent infostealer malware types identified by KELA
Breaking Down the OpenAI Breach Claim – KELA’s Findings
KELA’s investigation into compromised credentials from the emirking’s sample identified that they are identical to credentials stemming from multiple sources that share and sell data stolen through infostealing malware. The compromised credentials came from 14 distinct sources, classified by KELA as Private Data Leaks (originate from paid subscription bot seling TG channels), Public Data Leaks (widely shared stolen credentials, often appearing in public forums, dark web marketplaces majorly onTG channels). Notably, the most prevalent source in the dataset was linked to over 118 million compromised credentials in KELA’s data lake.
Multiple malware families were linked to these infections. The analysis revealed that Redline (8 occurrences), RisePro (5 occurrences), StealC (4 occurrences), Lumma (5 occurrences), and Vidar (4 occurrences) were the primary infostealer malware families observed, with infections date spanning from October 12, 2023, to July 28, 2024, and the majority of infections occurring between January and April 2024.
Further investigation into the compromised email addresses showed that 23 out of 28 were used for registration on other services, confirming that victims’ email addresses were repurposed across multiple platforms, which indicates their validity. This finding is based on the collection of wide range of characteristics from each bot, allowing to pivot on each compromised credential and analyze the whole infected machine’s stolen information including other credentials, dates, IP addresses, system information and more.
Screenshot of emirking’s post on BreachForums, February 9, 2025 (Source: KELA Platform)
Thus, based on the sample analysis, KELA asserts that the majority of compromised credentials of OpenAI services offered for sale on BreachForums by emirking are not related to a breach of OpenaAI systems. The credentials appear to be a part of a larger dataset scraped from a mix of private and public sources that sell and share infostealer logs. The affected individuals fell victim to different infostealer campaigns, which is highlighting the severity of infostealers’ threat and the necessity of proactive defence against them. For reference, in 2024 alone KELA collected more than 3 million compromised accounts belonging to OpenAI users, as well as 174,000 accounts belonging to Gemini users.
Recommendations
- Active Defence Monitoring: Monitor credential exposure to detect sensitive personal and work-related credentials early in the compromise process. Early detection allows organizations to quickly block threats by changing passwords, revoking access, and taking protective actions. To achieve this, leveraging a cyber exposure management platform like KELA’s can help organizations manage exposed credentials and prevent security breaches.
- Deploy Robust Antivirus Solutions: Organizations should implement comprehensive antivirus software to protect against cyber threats like phishing, malicious downloads, and drive-by attacks. Regular updates and features such as real-time scanning and behavioral analysis enhance defense, reducing the risk of exposure to infostealers and evolving malware.
- Invest in employee training and awareness to mitigate cyber risks: Organizations should prioritize training programs that enhance employees’ understanding of cyber threats and their associated risks. This is particularly critical for organizations where employees access sensitive work-related environments from personal computers that are not managed or secured by the workplace. Training sessions should be as practical as possible, focusing on the organization’s unique identifiers, specific asset types and tailored scenarios. This approach empowers employees to independently recognize and respond to potential threats while fostering a cybersecurity-aware culture.
- Enforce Strong Password Policies and Use MFA: Organizations should mandate the use of strong, unique passwords and implement Multi-Factor Authentication (MFA) to enhance account security. Passwords should avoid common patterns, such as including the service name or default terms, as they are more susceptible to brute force attacks. For example, KELA observed that the password “Chatgpt999” (one of the credentials from the emirking’s sample) appeared in 11 different compromised credentials used to access OpenAI services, involving 10 unique email addresses. Another instance observed was the usage of password pattern including “chatgpt” in it which revealed more than 2800 compromised accounts. By ensuring password complexity and using MFA, organizations can significantly reduce the risk of unauthorized access.