Infostealer Unmasker: Turning Digital Traces into Real World Identities
Infostealers collect far more than passwords and cookies, they can expose entire criminal networks. By aggregating and analyzing stolen logs, hidden identities of hackers, fraudsters, and crypto owners are revealed. With its vast data lake, KELA connects these traces to unmask real criminals and support law enforcement.
Published August 26, 2025

An infostealer is malicious software that collects stored information from a compromised device, including passwords, browser cookies, autofill data, and cryptocurrency wallets. Once installed, an infostealer can capture far more than a single victim’s data. When those stolen logs are aggregated and analyzed, they may expose hackers who believed they were operating anonymously, fraudsters using fake identities, or cryptocurrency owners who assumed their wallets could not be traced back to them. With access to a massive data lake of infostealer logs, KELA can cross-reference stolen credentials, browsing activity, and other digital traces to connect seemingly unrelated pieces of information. This allows KELA to uncover and verify the real identities of criminals, even those who go to great lengths to hide their tracks online, and contact law enforcement. In this report, KELA will present three real-world examples of how such exposures take place.
Scenario 1 – Ransomware Group Member
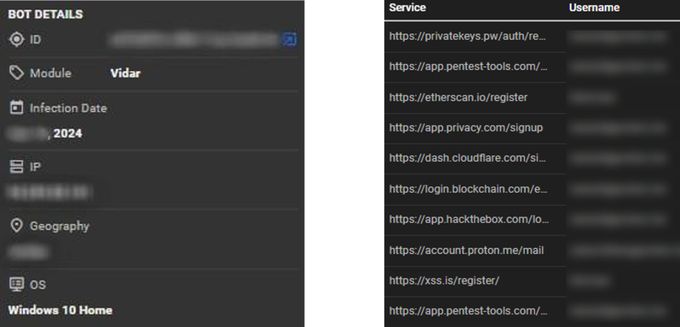
KELA continuously monitors infostealer leaks across cybercrime forums to identify valuable intelligence on threat actors. In one notable case, KELA detected that a high-profile ransomware operator was active on BreachForums, specifically using the forum’s escrow domain to conduct transactions. This finding triggered a deeper investigation aimed at mapping the actor’s digital footprint. Through careful analysis, KELA was able to uncover key elements of the threat actor’s infrastructure, including the tools and services they depended on, detailed browsing history, and other operational artifacts. These insights provided a clearer picture of the actor’s methods, resources, and online behavior, enabling a better understanding of their activities.
These leads also provided valuable insights into the rest of the ransomware group. Eventually, the identity of the threat actor behind the group was uncovered through the infostealer, which exposed personal details such as phone numbers, addresses, personal emails, and background information. Following this discovery, KELA notified law enforcement, who launched their investigation based on KELA’s findings.
Analysis of the infostealer data reveals the threat actor's digital footprint and operational habits. The stolen credentials include logins for cybercrime platforms like BreachForums and Doxbin, with the user of different browsers, with similar passwords across accounts for Cloudflare and Hack The Box, which indicates poor password hygiene and the potential for account takeover. A primary email address is a central login, appearing on numerous services like Pentest-Tools, Skrill, and AWS, further centralizing the actor's digital identity. The presence of credentials for Hack The Box and Pentest-Tools also points to the actor's use of legitimate cybersecurity platforms. The data also includes a login for a cryptocurrency-related site, blockchain.com, suggesting involvement in financial transactions.
Scenario 2 – North Korean IT Workers
Since last year, North Korean IT workers have drawn increasing attention for their attempts to infiltrate companies abroad. Operating primarily from countries friendly to North Korea, they often pose as remote workers in Western organizations, aiming to gain access to corporate systems and resources. Some also leverage freelance platforms like Fiverr and Upwork to generate income for the regime. Despite these efforts, their operational security is often weak with easily identifiable, repeated modus operandi, reliance on Astrill VPN, and the use of deepfake software to mask their identities. These shortcomings have allowed researchers to uncover numerous email addresses linked to the workers.
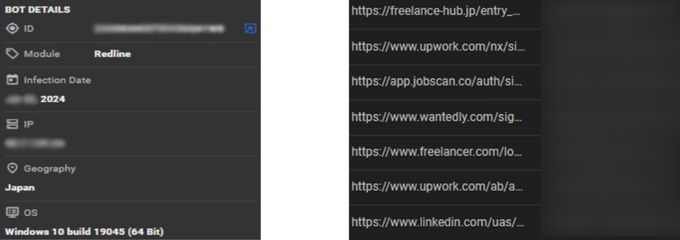
Using dozens of these reported emails, KELA searched its extensive infostealer data lake to gather deeper intelligence on their activities. The findings revealed that these workers frequently used tools and services such as Google Translate (from Korean to English), GitHub, Upwork, Fiverr, proxy platforms, and various VPNs. Additionally, infected machines often contained multiple personas, with many usernames ending in “dev” or random numbers, further indicating attempts to maintain multiple false identities for their operations.
Analysis of the data reveals the North Korean workers' digital footprint and operational habits. The machines include logins for freelance platforms like Upwork and Freelancer, as well as job search sites such as Indeed and LinkedIn, attempting to pose as legitimate remote professionals. The presence of credentials for a variety of job-related and career development services, such as Novoresume, Smartr, Jobscan, and Kickresume, further supports this. The data also reveals a heavy focus on IT-specific platforms, including GitHub, Codecademy, and a MongoDB cloud service. The use of multiple Outlook email addresses and the repeated use of the same password across numerous sites, including LinkedIn, Upwork, and Accenture, indicates poor security practices and the use of multiple people to conduct their operations.
Scenario 3 – Terrorism-linked cryptocurrency wallets
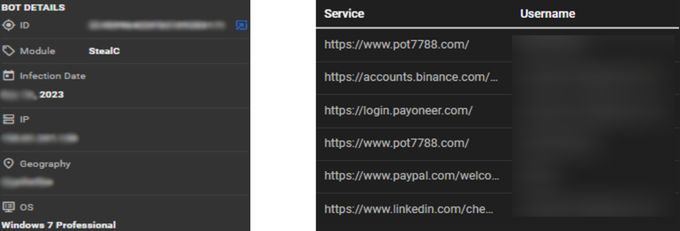
Working closely with law enforcement is a key component in uncovering the real identities behind malicious actors. In one case, KELA was investigating intelligence provided by a partner, where a cryptocurrency address was obtained. This address was linked to an individual involved in terrorist activities, primarily connected to financing operations. By cross-referencing KELA’s vast database of infostealer logs, it was discovered that the same individual had been infected by an infostealer. This infection exposed a wealth of personal and operational details, including infrastructure related to his terrorism activity.
This case highlights that infostealer data goes far beyond phone numbers and emails. It can also provide critical pivot points such as cryptocurrency wallets, credentials, and access to accounts or services used in illicit operations. While cryptocurrency is often viewed as an anonymous tool, an infostealer infection can impact that anonymity by tying wallet activity back to a real individual and their broader network. By leveraging this type of intelligence, KELA enables law enforcement not only to identify bad actors but also to map out their ecosystems, making it possible to disrupt criminal and terrorist activity at its core.
Analysis of the infostealer data reveals an individual's financial and professional digital footprint. The credentials include logins for numerous cryptocurrency and financial platforms such as Binance, WazirX, Skrill, PayPal, and Western Union. The presence of logins to multiple social media and messaging platforms, including Facebook, Instagram, Twitter, and Discord, indicates a broad online presence. The data also contains logins to educational and government websites, as well as a range of online services, suggesting a broad and interconnected digital life. Although the PC appeared to be infected by an African country, KELA’s investigation traced the actual location to Pakistan based on additional credentials.
Bottom Line
Understanding the modus operandi of each type of target can help retrieve even more infostealer bots from KELA’s data and identify additional actors for each use case. Each infostealer can expose the target’s infrastructure, provide valuable pivot points for further investigation, and assist law enforcement in obtaining critical answers. KELA has indexed and continues to index new infostealer data daily.
This continuous indexing ensures that investigations are not limited to static snapshots in time but benefit from a constantly expanding intelligence base. As new logs are ingested, older cases can be revisited with fresh correlations, sometimes revealing actors who had previously evaded attribution. Over time, this creates a dynamic, living dataset that strengthens KELA’s ability to track emerging threats, uncover hidden connections, and provide timely support to both clients and law enforcement partners.