2024 Paris Olympics: Compromised Before the Starting Gun
Updated July 23, 2024.

Olympic fever is well and truly upon us, with the Olympic Games starting in Paris on July 26th. However, it’s not just athletes warming up for fun and games, with eight-ten times the number of cyberattacks predicted for the Paris Olympics as were seen in the 2021 Olympic Games in Tokyo. As Tokyo saw 450M security events blocked — the risk has never been greater. You can download our full report for a comprehensive view of potential attack types, targets, and threat actors planning Olympic-related attacks, or read on for a brief overview.
Who is at Risk?
Attackers are known to take advantage of high profile events like the Olympic Games, leveraging the excitement and attention directed towards the event for many different reasons, whether that’s disruption, ideological and political motives, or for financial gain.
Threat actors targeting the 2024 Olympics have a wide range of victims to choose from, and may choose to attack Olympic assets, for instance websites and apps, the broadcasting service or the email accounts of the Olympic Committee, or they may go after partners of the Olympics. This year, there are 84 official Olympic partners, as well as those connected via third-party services, hospitality providers, and those offering travel and leisure. KELA has already identified multiple compromised internal accounts related to these orgs, such as EDF France, an official supplier of energy for the Games and Atos, an Olympic Games IT provider. This information has been stolen by infostealer malware, and has been leaked or offered for sale on various cybercrime platforms.
In addition, KELA has uncovered around 600 instances of leaked credentials, including approximately 150 plaintext passwords related to domains associated with the Olympics including olympics.com, paris2024.org, and paralympic.org, as well as over 8700 compromised accounts.
It’s not just Olympic partners and third parties that need to be wary. As the games are taking place in France, you should also expect a general increase in attacks against French organizations, especially critical infrastructure such as telecommunications, energy, healthcare, and logistics. Individuals should also be cognizant of potential instances of fraud, such as ticketing scams.
What Types of Threat Actors Will be Going for Gold?
There are various kinds of attacks to look out for, including influence operations, information theft for cyber espionage, destructive malware to cause damage, DDoS attacks to force downtime, ransomware for financial gain, and more. Threat actors conducting some of these attacks could leverage compromised credentials that are circulating in cybercrime sources. Threat actors that will likely target the Games include:
Nation States
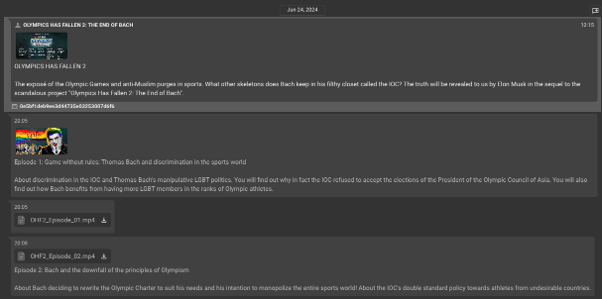
Russia is believed to be the country that is most likely to pose a threat at this years’ Olympic Games, due to factors including France’s continued support of Ukraine in the Russia-Ukraine conflict, and the IOC’s ruling that Russian athletes cannot compete under their own flag. KELA has already identified Russian-affiliated actors building influence campaigns related to the 2024 Games, including the campaign Olympics Has Fallen 2 in June 2024, a follow up from 2023’s Olympics Has Fallen video, both created using AI-generated celebrity voices by an actor tracked as Storm-1679.
Activity in Storm-1679’s Telegram channel in June 2024 as seen on KELA’s platform
Hacktivists
Politically-motivated attacks occurred at the 2016 Olympic Games in Rio, and ongoing conflicts such as Russia-Ukraine and Israel-Hamas put the 2024 games at higher risk. Pro-Russian hacktivist group NoName057(16) has already launched DDoS attacks targeting organizations of countries who opposed Russia and Belarus participating under their own flag.
NoName057(16) claims to have conducted a DDoS attack against the Austrian Federal Ministry of Labour and Economy following media reports on Austria opposing the participation of Russia and Belarus in the 2024 Olympics (auto-translated by KELA platform)
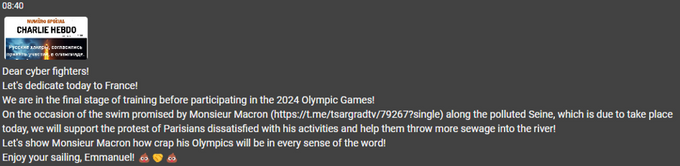
Another pro-Russian group, People’s Cyber Army boasted that they are training for the Olympics by completing attacks, supposedly in preparation for increased activity once the games begin.
People’s Cyber Army announces that they will be targeting France and that they are in their final phase of training before the Olympics (auto-translated by KELA platform)
Financially-motivated actors
Of course, many attacks will be opportunistic — led by threat actors that are looking to monetize operations for financial gain. Ransomware actors may feel confident in a quick payment if businesses cannot afford downtime during a peak season. Ransomware and extortion actors commonly attack French organizations, and KELA has already identified more than 60 organizations in France who have been victims of ransomware and extortion in 2024.
Olympic entities and third-parties will be handling a wealth of sensitive data, including financial details of attendees, which may well make them the target of attacks looking to sell data on. Globally, phishing scams are likely to leverage the Olympics for ticket scams, false merchandise, or fraudulent streaming websites that take advantage of fans and their fear of missing out.
On Your Marks… Get Set… Vigilance
Both individuals and organizations need to be wary of cyberattacks during the Olympic season, as social engineering attacks may use Olympic-themed techniques, and whatever the motivation — the cybercrime ecosystem will be gearing up for a surge in attacks.
French organizations and any business with a link to the Olympics should monitor the cybercrime ecosystem closely, using threat intelligence to identify any compromised accounts or leaked credentials that can be used for the attacker’s gain.
For more examples of Olympic Games-related cybercrime exposure, download our report, 2024 Paris Olympics: Cyberattacks are Far from Fair Game“
Want to check if your organization has been compromised in the cybercrime ecosystem — start your free trial of KELA’s threat intelligence platform.