Sharing is Caring: Ransomware and Extortion Actors Increase Threat Levels through Cooperation
Updated April 18, 2024.

Intimidating victims is all part of the game when ransomware and extortion actors steal data and aim to grab a pay day from the potential leak by demanding a ransom in return for not publicizing their haul. At KELA, we’ve noticed that threat actors have started leveraging one another’s data to maximize the level of threat, and sometimes even collaborating to distribute stolen information more widely. Really warms the heart, eh?
Ransomed Data Back Up for Grabs
One example of data moving around the cybercrime ecosystem can be seen in the recent headline-hitting Change Healthcare attack, where data was originally stolen by an affiliate of ALPHV (also known as BlackCat). Just weeks later, and despite Change Healthcare likely paying a $22M ransom, RansomHub have claimed that they have 4TB of Change Healthcare and United Health’s data, and are demanding a new ransom.
According to RansomHub, ALPHV “stole the ransom payment”, reiterating the claim that the affiliate responsible for the original ALPHV attack was not paid their fee, usually 70-80% of the total amount. This would have been a huge pay day for this affiliate, who goes by the name “notchy”. It’s possible that this affiliate kept a large portion of the stolen data, and angry at losing their payment, has now moved their loyalties over to RansomHub. It looks like the TBs of data stolen from United Health is the data leak that keeps on taking.
Can We Use Your House? It’s Bigger
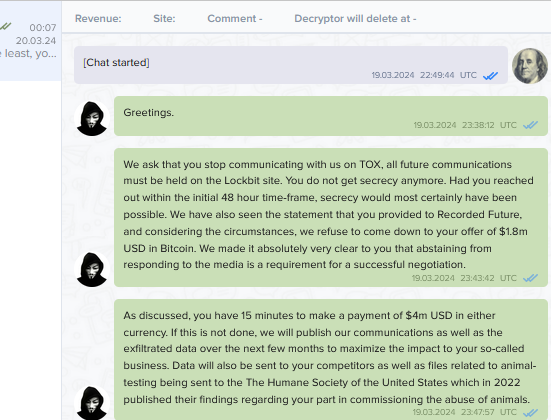
A slightly more purposeful collaborative example can be seen in the case of LockBit and an attack against pharmaceutical company, Crinetics. Despite the company claimed as a victim on the LockBit site, LockBit said that “those responsible for the exfiltration of data belonging to this victim have no association, indirect or direct, with the Lockbit group.” Instead, the independent actors who stole the data apparently approached LockBit in order to use their platform for adding intimidation and helping their negotiations with the victim. Kind of like asking the rich kid in class if you can use their house for your birthday party. It looks more impressive, and you might get better gifts.
The details became known when the negotiations failed and LockBit posted screenshots of their conversation with the victim on their blog. In these screenshots, there is a shift from TOX messenger (apparently used by the original actor behind the attack) to a negotiation chat on LockBit’s portal. While the stolen data hasn’t yet been published on the LockBit forum, it has been listed under Published — suggesting future exposure is possible.
Let’s Work Together — Fostering a Cybercrime Ecosystem
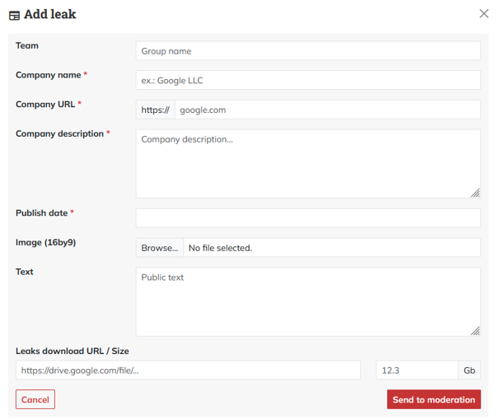
These examples and more show that ransomware and extortion actors are certainly aware that they can do more together than they could do alone. Some operations are even coming right out the gate offering to collaborate with other groups. One example is Rabbit Hole, a new operation designed to support “small to medium-sized attack groups” who don’t have their own websites in posting leaks online. After threat actors include some basic information, moderators will verify leaks, and either publish them under a user profile, or reject them. Like a dating website — but for nefarious threat actors rather than lonely hearts.
Supporting other threat actors by publishing their data to a wider audience is nothing new, as KELA has seen groups such as 8Base and many others noting they are open to helping with negotiations and publishing stolen data. Looks like the criminal community is gaining increasing awareness that they can lift each other up with exposure and support. If it wasn’t awful, it would actually be kind of nice.
Using Cyber Threat Intelligence to Understand the Ecosystem
It’s not all doom and gloom. Just as attackers have their own ecosystem, so do the good guys. By using cyber threat intelligence, security teams can stay aware of the cooperative activities between different ransomware and extortion groups, and understand the various elements and personas at play.
Who is a large threat in and of themselves? Who is merely leveraging a bigger player’s name and reputation to increase intimidation? Who actually has gained a foothold into your organization — and who is just riding on their data coat tails?
As cybercriminals increase their cooperation and support for one another, and the cybercrime community enables leaked data to circulate across platforms — access to accurate and timely information is more important than ever before.
Looking to boost your threat intelligence so you know all the ins and outs of the growing cybercrime ecosystem? Request a Free Trial of KELA’s Cyber Threat Intelligence Platform.