The Fearless CIO: Why "Yes" to AI is the Only Secure Answer in 2026
Control AI adoption and eliminate the 'Productivity Tax' of shadow AI usage. Discover how an Intelligence-Led strategy uses CTI to replace blind restriction with radical enablement, providing a silent safety net for your 'Crown Jewels'
Published February 6, 2026

For decades, the CIO's office was affectionately (or not so affectionately) known as the "Department of No." Security was synonymous with friction. If a tool was risky, we blocked it. If a process was unvetted, we killed it.
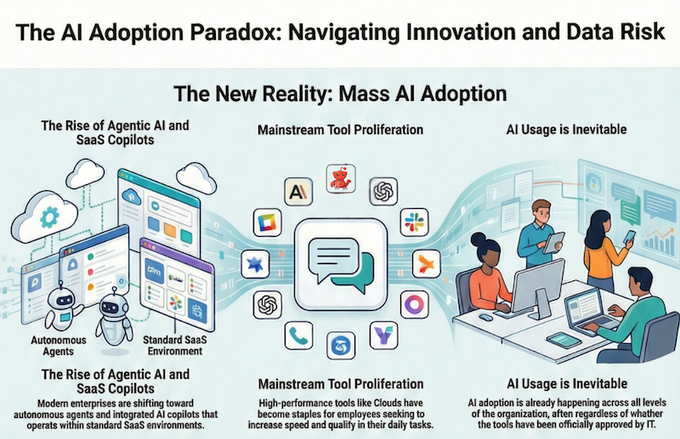
But in 2026, the game has changed. The AI Adoption Paradox has made the "Stop" sign obsolete. Today, the most successful CIOs aren't the gatekeepers ,they are the accelerators.
The Productivity Tax of "No"
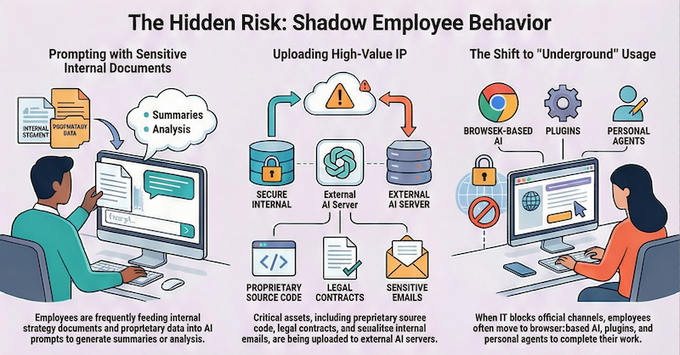
When you block a powerful AI tool, you aren’t actually stopping the risk. You are simply pushing it into the shadows. According to the latest data on shadow employee behavior, the moment IT blocks an official channel, employees move to:
- Browser-based AI and unvetted plugins.
- Personal agents operating outside the corporate firewall.
- Underground usage where high-value IP is uploaded to external servers without any oversight.
The recent widespread adoption of open source tools like openclaw and moltbot open up an even more difficult task when trying to reign in or block these risks.
This is the Productivity Tax: your organization loses efficiency, falls behind competitors, and still remains exposed to data leaks.
The Intelligence-Led Approach: Radical Enablement
The strategic challenge of 2026 is moving beyond the false binary of "IT Block" vs. "Unmanaged Exposure." The solution is an Intelligence-Led Approach.
Instead of building higher walls, we are building better radar. This radar doesn't just look inward at employee behavior; it maps the entire external digital ecosystem where your organization and its partners operate.As a Fearless CIO, your goal is to enable 100% of your workforce with the AI tools they need to be 10x more productive, while using Cyber Threat Intelligence (CTI) as your silent safety net.
A 360-Degree Intelligence Shield
If you give your team the green light to innovate, you need to know the moment something goes wrong. This is where leveraging AI to combat the cyber underground becomes your secret weapon.
Cyber Threat Intelligence: Your safety net
Modern Cyber Threat Intelligence doesn't just watch your network; it monitors the places where stolen data actually ends up.
- Dark Web Monitoring: AI-driven bots scan hacker forums for leaked proprietary code or sensitive internal prompts in real-time.
- Early Warning Systems: CTI identifies "smoke" (like a credential leak in an infostealer log) before it turns into a "fire" (a full-scale breach).
- Surgical Intervention: When a risk is identified, you don’t shut down the department. You intervene surgically—rotating a specific key or securing a single account—while the rest of the company keeps moving at the speed of AI.
External Attack Surface Management (EASM): Mapping the AI Shadow
While CTI identifies the threat, EASM identifies the target. As teams spin up "Shadow AI" projects, your digital footprint expands faster than your inventory can track.
- Asset Discovery: Automatically finds unmanaged APIs, forgotten cloud instances, and sub-domains created by AI experimentation.
- Vulnerability Triage: Prioritizes fixes for the "front doors" that are actually visible and exploitable by attackers.
Third-Party Risk Management (TPRM): Protecting the Supply Chain
You aren’t just adopting AI, you’re adopting your vendors' AI. Intelligence-led TPRM replaces static annual audits with real-time visibility.
- Dynamic Monitoring: Uses CTI to watch for leaked vendor credentials or breach chatter on the dark web before it hits your network.
- Supply Chain Resilience: Provides the early warning needed to sever risky connections or rotate keys before a third-party compromise becomes your catastrophe.
The Bottom Line
In 2026, security is no longer about what you block; it’s about what you see.
By embracing an intelligence-led strategy, you can stop being the "Department of No" and start being the engine of growth. Give your employees the tools they want. Unleash their productivity. And let modern CTI be the watchtower that keeps the "Crown Jewels" safe.
Of course, you should still make every effort to reduce the risks of emerging AI tools. Be it with security measures, process adherence and policies you put in place. But with the flexibility of knowing you have CTI as your safety net.
The most successful CIOs of this era won’t be remembered for the risks they avoided, but for the innovation they enabled.