The Rise of macOS Infostealers in 2025: Tactics, Trends, Defenses
macOS infostealers are surging in 2025, targeting credentials, wallets, and corporate accounts. Enterprises and users alike must rethink macOS security.
Updated November 12, 2025

While once considered the “safer” alternative to Windows, macOS is growing in popularity for attackers. In fact, KELA’s latest research shows a sharp rise in demand and supply for macOS infostealers, malware built to silently exfiltrate credentials, cookies, wallets, and personal data from infected systems.
As macOS adoption continues to grow across enterprises, this shift marks a turning point: Apple’s security ecosystem is no longer a deterrent, but a challenge that threat actors are actively working to overcome.
» Try KELA's cyber threat intelligence for free
What Are Infostealers? (A Refresher)
Infostealers are lightweight, purpose-built malware designed to harvest sensitive data for rapid monetization. Rather than breaking into systems with complex exploits, attackers use credentials and tokens stolen from infected machines to log into victims’ environments directly.
They commonly grab browser passwords, cryptocurrency wallets, and cloud tokens, then sell that data on underground marketplaces.
The rise of Malware-as-a-Service (MaaS) - including its adoption in the infostealer market has significantly professionalized this criminal ecosystem. Developers now offer ready-made infostealer kits complete with web panels, subscription plans, and even customer support, lowering the barrier to entry for threat actors. As a result, even low-skilled operators can rent fully functional macOS infostealers for a few thousand dollars per month.
» Here's everything you need to know about infostealers
Why macOS Users Are Valuable Targets
macOS and iOS users represent a uniquely lucrative demographic. Research cited in KELA’s report shows that Apple device owners typically:
Have higher average incomes and spending patterns.
Maintain accounts with greater financial value, including crypto and banking apps.
Exhibit higher trust in their devices’ security, making them more susceptible to social engineering.
This combination of stored wealth, user confidence, and cross‑device syncing creates an attractive target profile for infostealer operators. A single compromised macOS endpoint can expose SaaS sessions, cloud credentials, and even developer environments - all of which can be resold as “corporate access” on dark web markets when the infected machine is linked to a company environment.
» Find out if darknet markets are going out of business, and what will happen next
macOS Adoption in Enterprises: A Growing Attack Surface
Across both SMBs and large enterprises, macOS adoption continues to climb. According to recent data:
- macOS now represents 27% of SME endpoints, up from 24% in 2024.
- In large enterprises, Apple devices account for about 15% of endpoints, and 73% of IT leaders report their Apple fleet grew in the past year.
For cybercriminals, this trend means that compromising one Mac may open the door to an entire network, from cloud dashboards to VPNs and collaboration tools.
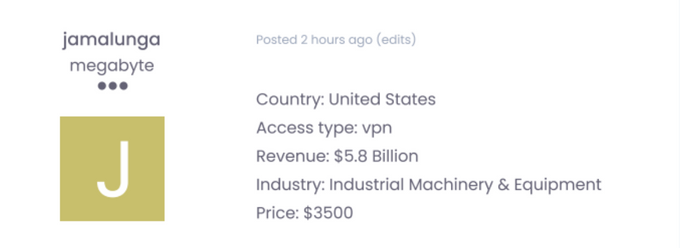
Did you know? KELA’s researchers observed a $3,500 underground listing for VPN access to a U.S. industrial firm, illustrating just how easily stolen macOS credentials can be monetized.
» Here are the most targeted entry points by hackers
The Expanding Market for macOS Infostealers
Since 2023, the underground market for macOS-targeting infostealers has gained momentum. Threat actors are both buying and selling these tools at record levels, with chatter peaking in 2025. Notable examples include:
- AtomicMac Stealer (AMOS): A polished MaaS offering priced at $3,000/month, capable of stealing Keychain data, browser credentials, and over 100 crypto wallets.
- Quark Stealer: A cross-platform infostealer with SaaS-like marketing, Telegram support, and professional changelogs, available for both macOS and Windows.
These examples highlight a new reality: macOS is no longer a niche target. The underground market has matured into a structured, competitive ecosystem where reliable macOS stealers are in high demand - and command premium prices.
Protecting macOS Devices
macOS users and enterprises should no longer rely on reputation alone. Defenses must evolve to match the sophistication of today’s threats. KELA recommends:
Vigilance and awareness: Beware of fake installers, ads, and phishing links that deliver infostealers.
Patch and monitor: Keep software current and watch for abnormal system activity.
Equal priority: Treat macOS security with the same seriousness as Windows - deploy EDR tools, enforce MFA, and monitor for compromised credentials.
Leverage CTI: Use cyber threat intelligence to identify relevant macOS malware campaigns and prevent exploitation before it spreads.
KELA’s full report, “The Rise of macOS Infostealers: 2025 in Review,” dives deeper into all these topics and also covers:
Case studies of AtomicMac Stealer (AMOS) and Quark Stealer
macOS infostealer timelines and market trends
Real underground demand/supply examples
Strategies for macOS defense