Top 8 Deep Web and Dark Web Forums
The deep web contains legitimate private data requiring authentication, while the dark web hosts anonymous forums where cybercriminals trade tools, credentials, and attack intelligence. Understanding these environments helps security teams anticipate threats before they impact operations.
Published November 4, 2025

The deep web and dark web represent distinct layers of the internet that most users never encounter, each serving fundamentally different purposes within the broader cyber ecosystem. While the surface web comprises only about 4% of all online content, the deep web contains the vast majority of internet data—everything from password-protected databases to private medical records—that simply isn't indexed by search engines.
The dark web, a deliberately hidden subset requiring specialized tools like Tor, has become notorious as a marketplace for illicit activities and cybercrime operations. In this blog, we'll examine the top deep web and dark web forums, their distinguishing characteristics, and what makes them valuable sources of threat intelligence. Most of these forums also have clearweb versions, offering limited access without the need for Tor.
» Get started for free with KELA and strengthen your cybersecurity
Deep Web vs. Dark Web: Key Differences
Before discussing the specific forums, it's essential to understand how these two environments differ in their fundamental structure, accessibility, and operational purpose.
| Characteristic | Deep web | Dark web |
|---|---|---|
| Accessibility | Standard browsers (Chrome, Firefox, Safari) with proper authentication credentials like passwords or institutional access | Requires specialized software (Tor Browser, I2P, Freenet) and knowledge of .onion or .i2p addresses |
| Indexing | Content exists but is not indexed by search engines due to paywalls, authentication requirements, or robots.txt exclusions | Intentionally hidden from standard search engines through encryption and requires specific network protocols to access |
| Size | Comprises approximately 96% of internet content, estimated at 500x larger than surface web | Represents less than 0.01% of total internet, with approximately 60,000 active .onion sites at any given time |
| Primary purpose | Legitimate private data storage including academic databases, corporate intranets, medical records, financial systems, and subscription services | Anonymous communication, privacy protection, circumventing censorship, but frequently facilitates illicit marketplaces and cybercrime forums |
| Security level | Standard HTTPS encryption, password authentication, two-factor authentication, and institutional access controls | Multiple layers of encryption (end-to-end + network-level), onion routing, cryptocurrency transactions, and advanced operational security protocols |
| Legal status | Entirely legal when accessed with proper authorization | Legal to access and use anonymization tools, but hosts significant illegal content including stolen data markets, hacking services, and illicit goods |
» Find out if darknet markets are going out of business, and what will happen next
Essential Features of Credible Deep and Dark Web Forums
- Vetting and reputation systems: Forums establish credibility through rigorous member vetting and reputation scoring. Reputation systems track transaction history, information quality, and community engagement over time. These mechanisms create trust hierarchies where established members access exclusive subforums with high-value intelligence.
- Escrow and transaction security: Trusted forums implement escrow services holding funds until transaction completion, significantly reducing fraud. Neutral moderators verify delivery before releasing payment. Advanced platforms offer dispute resolution, transaction insurance, and automated releases based on predefined conditions or cryptocurrency smart contracts.
- Operational knowledge and TTP sharing: Forums facilitate exchange of guides and hacking methods, valuable to both threat actors and security researchers. Discussions include tutorials, demonstrations, and troubleshooting that lower barriers for less sophisticated actors.
- Data quality and verification processes: Credible forums implement verification to ensure information is accurate, current, and actionable. Moderators and senior members challenge claims, request proof-of-concept demonstrations, and flag suspicious posts.
» Read more: Inside the threat intelligence market
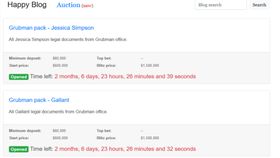
Top 8 Deep Web and Dark Web Forums
» Not convinced? Here are more reasons you need cyber threat intelligence
Gaining Visibility Into Hidden Cyber Threats With KELA Cyber
Organizations cannot defend against threats they cannot see. KELA's cyber threat intelligence platform penetrates the hardest-to-reach cybercrime underground forums and dark web marketplaces, giving security teams the attacker's perspective before threats materialize. Rather than reacting to incidents after they occur, your team gains real-time intelligence on exposed credentials, planned attacks, and threat actor TTPs specific to your organization.
This proactive approach transforms security operations from firefighting mode to strategic defense, enabling you to remediate vulnerabilities before adversaries exploit them.
» Ready to get started? Contact us to learn more about our cyber threat intelligence services
FAQs
What is the main difference between the deep web and the dark web?
The deep web consists of legitimate password-protected content not indexed by search engines, including academic databases and corporate intranets.
The dark web is a deliberately hidden network requiring specialized software like Tor, often hosting cybercrime forums and illicit marketplaces.
Why do cybercriminals prefer dark web forums over surface web platforms?
Dark web forums provide multiple layers of encryption, anonymity through onion routing, and protection from law enforcement monitoring.
These platforms enable cybercriminals to trade stolen data, coordinate attacks, and exchange tactics without revealing their identities.
Can security teams legally monitor dark web forums for threat intelligence?
Accessing and monitoring dark web forums is entirely legal for security research and threat intelligence purposes.
Organizations use this intelligence to identify exposed credentials, anticipate attacks, and understand threat actor capabilities.