Off-the-shelf Ransomware Source Code is a New Weapon for Threat Actors
Published January 15, 2024.

If it looks like a duck, and walks like a duck… you may need to look a little closer. This is an increasingly important lesson, highlighted by the case of threat actors Hunters International, who were wrongly assumed in October 2023 to be a rebrand of Hive ransomware group.
This kind of mistake is becoming increasingly easy to make. After all, 60% of the Hunters International ransomware code matched the Hive ransomware. But early reports from the security community had jumped to incorrect conclusions. They had fallen victim to what the National Crime Agency calls a Frankenstein ransomware variant — one which makes it harder than ever for law enforcement to accurately attribute ransomware to the right criminals.
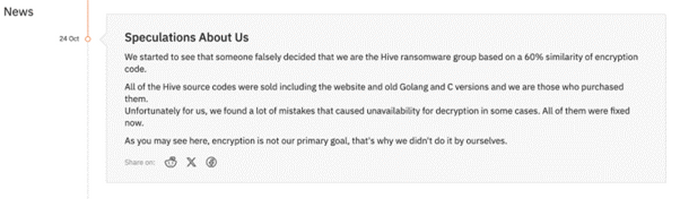
Hunters International’s statement on their blog in October 24, 2023
In this case, Hunters International claimed that as encryption wasn’t their primary motive, the encryptor source code had simply been bought from the Hive developers, off the shelf, a worrying tactic that has become part of the Ransomware-as-a-Service (RaaS) industry status quo.
Threat Actors Recognize That One Group's Trash Could be their Treasure
Traditionally, ransomware and extortion actors turned to the cybercrime ecosystem to buy the information they needed to launch attacks, including pentesting tools, zero-day vulnerabilities and initial access to companies’ networks.
However, we are now seeing a growing trend, shown here by Hunters International use of Hive ransomware and by many other similar attacks. Threat actors are taking RaaS a step further, purchasing source code and infrastructure either directly from former ransomware gangs, or from those with access to their tools.
The Hunters International ransomware is just one example of this worrying pattern.
Another example of “click to buy” approach in RaaS is the case of LockBit, who purchased BlackMatter code, as well as using leaked Conti code for LockBit 3.0. A representative of LockBit admitted that LockBit 3.0 code is based on the BlackMatter source code, with several improvements.
LockBit refers to Conti and BlackMatter in its operation and claims they are ready to buy Alphv and REvil variants too (auto-translated on KELA’s platform)
At KELA, our researchers identified this RaaS affiliate program in July 2021 when BlackMatter were recruiting initial access brokers on Exploit and XSS — two major Russian language cybercrime forums. Looking at LockBit 3.0 and BlackMatter source code, researchers can identify many similarities between the two, including their API harvesting and anti-debugging techniques, how they approach privilege escalation, and even details such as the ransom note name, the wallpaper, and the icon name.
While BlackMatter announced in 2021 that they were shutting their operations down, it’s clear that the infrastructure and source code lives on.
A Complex Landscape: What You See is No Longer What You Get
In a circular turn of events, and showing how complex the ransomware environment has become, LockBit has also been on the receiving end of this trend. When Lockbit leadership came to blows with a member of its development team, the developer in question retaliated by leaking LockBit’s ransomware builder. This is a tool that allows anyone to build an encryptor and decryptor for ransomware attacks.
Two users, possibly the same actor, leaked the files on different platforms. First, an unknown actor named “Ali Qushji” shared the builder via his Twitter account, and subsequently, a user named “protonleaks” shared a copy of the builder with VX-underground.
Another user, known by the handle “Persistent”, leaked the builder on BreachedForums, but it’s not clear if this actor was involved in the incident or whether they were simply sharing already leaked information. In parallel, LockBit addressed the breach in the XSS forum and claimed that they had not been hacked, but that a programmer employed by the Lockbit group is behind the leak.
Lesson learned, criminals — be nicer to your employees.
The results were swift. Within a week, the ransomware group Bl00dy had launched an attack against Ukraine using this leaked builder. According to researchers, Bl00dy “do not appear to develop ransomware independently. Instead, they create encryptors using leaked builders and source code of other ransomware operations.” The message is clear. You no longer need to develop your own ransomware to launch an attack. You only need to be a pro at finding a great deal on the internet. Are you a Prime Day enthusiast interested in turning criminal? Your time is now.
We could go on. Another notable example is the Babuk source code — leaked in 2021. At least 10 ransomware families have been identified that are linked to the leaked source code, all of which target ESXi hosts, including strains such as Cylance, Rorschach and RTM Locker.
When Seeing is No Longer Believing… What Can You Trust?
It’s clear that creating a good ransomware operation is now just a question of good management. A bad actor can hire the right people, pay for the required services, and buy their ransomware ready to go off-the-shelf, all tied up in a bow.
What does that mean for enterprise defenders? We will leave you with a few key points to consider:
- There’s no such thing as a “dead” ransomware variant: The latest example of a leaked source code is the sale of Zeppelin2 ransomware, thought to be defunct as of 2022. As source codes and builders could be leaked at any time, non-operational needs to be considered merely dormant.
- Launching an attack is only getting easier: Zeppelin2’s source code and builder were allegedly sold for just $500, by a forum member known as “RET.” With that price point, and the low development barrier to entry, a curious teenager looking to 10x their babysitting money could launch the next attack.
- Be wary of jumping to conclusions: The only thing we know for sure is that our first impressions may be wrong. The best protection is to make sure you have access to a broad range of intelligence and sources, so that you’re as knowledgeable as possible about potential threats.