Telegram Clouds of Logs – The Fastest Gateway to Your Network
Published August 17, 2023.

What is common between Okta, Uber, and EA Games? All fell victim to cyberattacks enabled by a single access point: compromised employee credentials. In the ever-changing cybercrime landscape, cybercriminals always find ways to put their hands on corporate sensitive data. One of the most popular ways to gather such credentials is using information-stealing malware or simply buying the bots (machines already compromised by info-stealing malware) on botnet markets and Telegram channels.
Recently CISA reported that more than half of all cyberattacks on government entities and critical infrastructure involve valid credentials. That means that cybercriminals are using active employee credentials or default administrator credentials for their attacks. After acquiring login credentials, whether through purchase or by obtaining them for free, threat actors utilize these valuable assets in various campaigns, ranging from phishing to ransomware attacks.
In this blog post, KELA examines the contrast between two methods of acquiring credentials: botnet markets such as Russian Market, Genesis, and TwoEasy (enabling the individual purchase of bots), and “clouds of logs”. Clouds of logs operate on a subscription basis, allowing threat actors to purchase and utilize multiple bots together through platforms like Telegram. The user-friendly Telegram interface, extensive bot sharing, and diverse actors and information-stealing tools collectively enhance the appeal and convenience of this messaging platform for conducting such transactions.
Clouds of logs on Telegram
Telegram is one of the most popular platforms where access to logs is provided via channels with information from many bots. These Telegram channels provide public samples or allow private access to logs based on subscription.
A log file includes all the sensitive data stored on a machine. This includes credentials to different accounts and applications, from login to VPN, RDP and business services to banking accounts and social media and gaming platforms accounts.
Threat actors have obtained logs through the utilization of information-stealing malware like Redline, Raccoon, Vidar, and others. These attackers infect victims’ devices with malware as a means to infiltrate and access highly sensitive data, encompassing both private and corporate credentials.
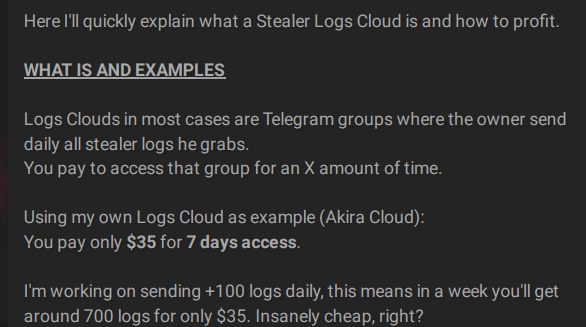
Clouds of logs have gained popularity in the past year over “traditional markets.” Threat actors constantly offer public and private services of logs, sharing and selling high quantities of daily logs on cybercrime forums and Telegram channels. The cybercrime chatter shows the methods actors use to cash out logs very easily and inexpensively.
Actors explain how to profit from clouds of logs with a small investment.
Ease of access to thousands of bots
The big advantage of Telegram channels compared to other botnet markets is its simple and friendly user interface and easy supply chain of such sensitive information. Users can easily download and access Telegram like other messaging applications/platforms, and search for those channels. Once users get access to a channel, they are able to download all the login credentials and passwords in one click.
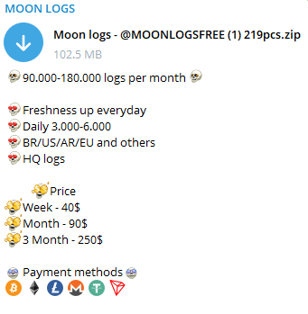
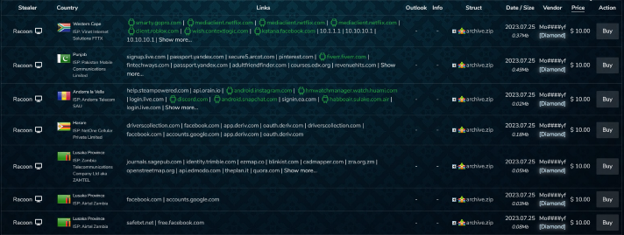
For example, in July 2023, approximately 180,000 bots were made available for purchase on the Russian Market. In contrast, by simply subscribing to five premium channels on Telegram, a user can acquire access to logs from over 500,000 bots within a single month. The user interface is very easy. Users are not requested to register or follow specific rules like in other markets and forums; they can simply join the channel and get access to free samples or pay for private access to logs. Unlike botnet markets, bots are not exclusive to the buyer. Premium channels allow access to several users, and therefore, once a user downloads the bots, other users can still leverage it for cyberattacks.
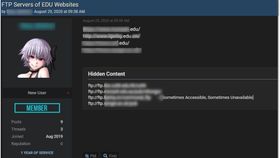
A Telegram channel offers a free sample of credentials of 219 computers.
Russian Market offers bots for sale.
Price of credentials
The payment makes the process easier, users can buy a subscription to a “cloud of logs”, pay an average price of USD 90-USD 150 for an average monthly fee and get around 90,000 – 300,000 logs per month (less than USD 1 per bot). In comparison, on the markets, users would be able to buy a specific bot for an average price of USD 13, not to mention the cost of efforts (buying each bot individually), which makes the supply chain more expensive, complicated, and less scalable.
Supply from various threat actors
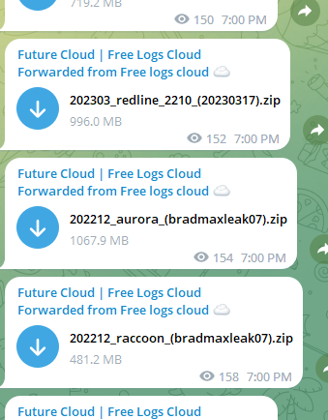
Clouds of logs also advertise logs harvested from a wide range of infostealers. Different teams may be using different information-stealing malware as their initial infection vector to target a wide range of victims. Different types of malware broaden an attacker’s reach from which he can extract sensitive information. KELA observed that on Telegram channels actors can find a diversification of commodity information stealers such as Checklog, Stealc, Aurora, Rhadamanthys, CryptBot and Predator The Thief. StealC, Aurora, Rhadamanthys and CryoptBot appeared in 2022 and 2023, while Checklog and Predator The Thief have been sold for several years. For example, Russian Market started selling bots of Stealc in July 2023, although the Stealc stealer emerged already in January 2023 and logs of the stealer appeared on the Telegram channel since January.
Logs cloud channel shares logs from different stealers.
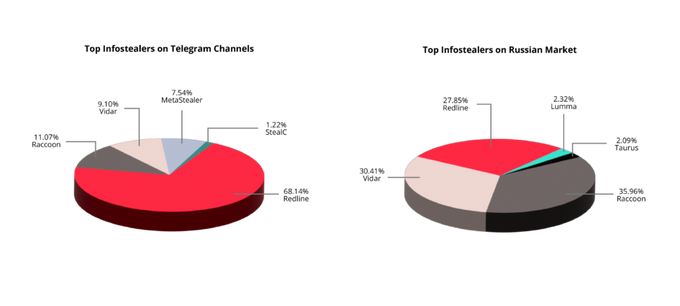
Based on KELA sources, there is a difference between the top infostealers on Clouds of Logs on Telegram channels and on Russian Market. The top infostealer on Telegram is Redline, followed by Raccoon, Vidar, MetaStealer and Stealc. On Russian Market, the top three stealers are Raccoon, Vidar, Redline (with slight variations among those three) Lumma and Taurus.
Targeted vs. opportunistic campaigns
On the markets, users can easily search for a specific domain, country, OS, etc, finding a specific compromised machine or victim. On Telegram actors will get a massive amount of logs and if they aim to target a specific sector or company, they would need to search through the data. However, the quantity on Telegram allows threat actors to target different victims, trying different entry vectors with a fixed amount of money spent on logs.
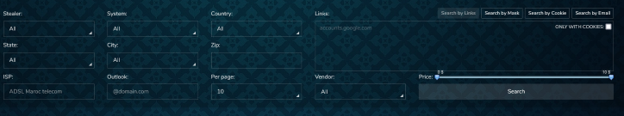
A search bar on Russian Market for filtering bots based on characteristics such as type of stealer, country, domain, etc.
While targeting a specific country or company may be harder on Telegram, it’s not hard to find credentials to compromise sensitive services such as VPN, RDP accounts, Jira, Slack and Okta, which can easily be found both on markets and on clouds of logs channels. On Telegram channels, actors can easily purchase credentials for internal corporate services and reuse the login information to infiltrate a corporate environment.
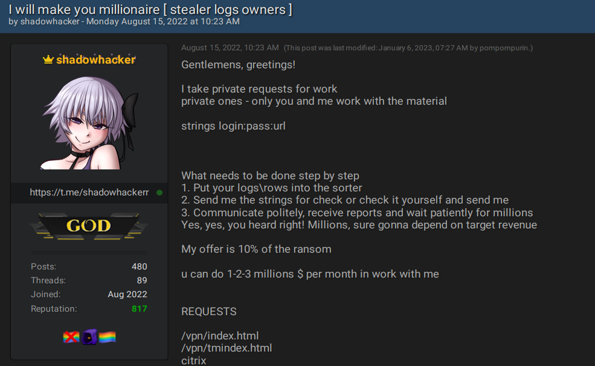
The massive quantity of logs requires actors to know how to find a needle in a haystack — to find the most critical services and their credentials. Therefore, actors not only exchange advice on detecting such resources, but they also sell dedicated tools and services to find specific credentials. For example, on August 15, 2022, an actor offered his services to search sensitive services on logs from stealers. The actor claimed that he could provide a tool for checking sensitive services including such VPNs as Fortinet, Palo Alto, Pulse Secure, Cisco, Citrix and others through the compromised credentials. In addition, the actor claimed that those compromised accounts would be used for ransomware attacks and would pay 10% of the revenue. The actor has been inactive since March 2023, but he is still operating Telegram channels and sharing databases and login credentials.
An actor offered services for finding sensitive accounts from stealer logs.
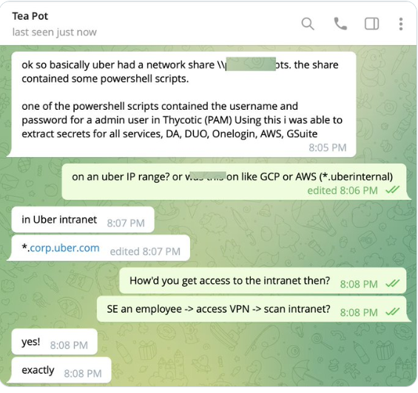
For example, in the Uber attack, Lapsus$ threat actors were able to acquire login credentials from an employee, which they likely bought from botnet markets based on their common TTPs. This allowed them to access the internal company VPN. The actors used PowerShell scripts on Uber’s intranet containing access management credentials that allowed them to allegedly breach Uber’s AWS and G Suite accounts.
The hacker explained how he hacked Uber using credentials.
KELA has been monitoring compromised accounts that are being sold on cybercrime markets and Telegram channels on a daily basis. For example, in the past year, KELA managed to detect a compromised account associated with a critical resource connected to a telecommunication company’s domain. However, the bot was no longer available on the cybercrime market. KELA investigated the malware-infected URLs on the Cybercrime investigations module by pivoting on the bot ID. In the search for unique URLs, KELA detected a WordPress blog that may include the first and last name of the employee and was able to find his profile on LinkedIn. This example shows the importance of disabling past employees’ company credentials.
The large number of logs on the clouds, along with the friendly user interface, easy payment, and the ability to remove any registration barriers make Telegram clouds of logs a perfect mine for cybercriminals and at the same time impairs the value of other botnet markets. Therefore, it’s crucial to implement these measures to protect sensitive services:
- Multi-factor authentication (MFA): Implement MFA across all company’s accounts to ensure that even if passwords are compromised, unauthorized access is significantly more challenging.
- Regular password updates: Enforce a policy that requires employees to update their passwords periodically. This practice reduces the risk of exposure of credentials in case of a breach.
- Employee cybersecurity training: Educate employees about the risks and threats of phishing attacks and social engineering campaigns.
- Monitoring cybercrime sources: Monitor cybercrime activities to identify cybercriminals’ attacks, actors’ TTPs, and potentially compromised accounts.
- Disable ex-employees credentials: Implement a protocol and process to delete an ex-employees credentials immediately upon their departure.
Past breaches have taught companies a crucial lesson: They must protect sensitive information from unauthorized actors; otherwise, their company is at risk. The KELA platform allows visibility into millions of bots, allowing organizations to track these compromised services and enabling them to respond immediately. That in turn, can reduce the chances of their corporate credentials being exploited in a future cyberattack.
Get notified about threats targeting your organization in real-time. Try KELA’s Cyber Threat Intelligence Platform for Free.