USA Unemployment Fraud: It’s Easier Than You Think
Published May 26, 2021.
Unemployment systems have been challenged with responding to millions of unemployment claims over the last year, with thousands of those being fake claims made by cybercriminals. The US Pandemic Unemployment Assistance (PUA) and other assistance programs that were launched in response to the COVID-19 outbreak opened the doors to many cybercriminals searching for further ways to make money. Nearly 36 billion dollars have been taken away from US citizens in unemployment benefits, and that number will continue to rise as cybercriminals are persistent on taking advantage of those benefits. The cybercrime underground ecosystem has become an excellent hub for trading various unemployment fraud services. Many of the services that our research has identified capitalize on identity theft basics and methods that have been circulating in underground platforms for years and therefore welcome cybercriminals who do not necessarily possess advanced technical skills. KELA has been closely tracking criminal actors across the cybercrime underground ecosystem and has identified significant levels of interest in PUA fraud schemes, which arm cybercriminals with the necessary information to illegally obtain US citizens’ unemployment benefits. The top three non-technical services we’ve identified interest for were: 1. Fullz, which are bundles of information that belong to real people and contain personal information that would assist fraudsters in carrying out identity theft. 2. Step-by-step guides (aka “methods” or “sauces”) on how to carry out these attacks. 3. Targeting of the ID.me identity service – used for citizens’ access to digital government services – aiming to bypass it.
A Good Operation Starts with a Good Set of Fullz
“A good operation starts with a good set of Fullz,” says one of the fraud methods guides that was posted to a popular cybercrime forum a few months ago. PUA claims are no exception, as obtaining a set of “Fullz” is one of the first steps toward a successful “identity theft” and a fraudulent unemployment claim. The typical Fullz refers to a bundle of stolen information that belongs to real people. Fullz may contain a person’s full name, date of birth, home address, email address, SSN and account numbers, among other personal details. Stolen Personally Identifiable Information (PII) allows cybercriminals to take over accounts, apply for credit cards or bank accounts, hijack sim cards, take out a loan, commit tax return fraud, make fraudulent credit card purchases – or in this case, perform fake unemployment claims. There is no one direct route to collecting PII though. For example, threat actors use multiple phishing tactics that lure victims into sending their PII to them; those details are then used directly by the threat actors or resold through different underground platforms. These details can generally be purchased for quite a low cost ranging from just a few dollars per piece (PII of one person can be sold for $2.50) to up to $40, depending on the amount of data available in the stolen identity. Below we’ve shared just a few of the many posts our research team has identified of cybercriminals selling Fullz belonging to US citizens:
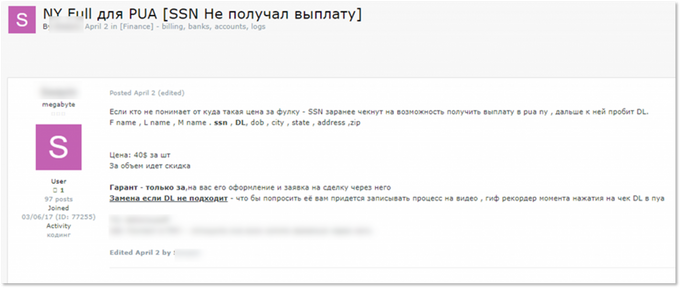
A Russian-speaking threat actor is offering Fullz of New York State residents – SSN, DOB, address, driving license details. The actor offers to sell this data for $40 per “piece” and states he checks that the SSN is eligible for PUA in NY.
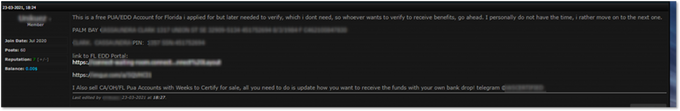
A threat actor, who sells Fullz of California, Ohio and Florida citizens, offers here full details of an alleged California PUA account.
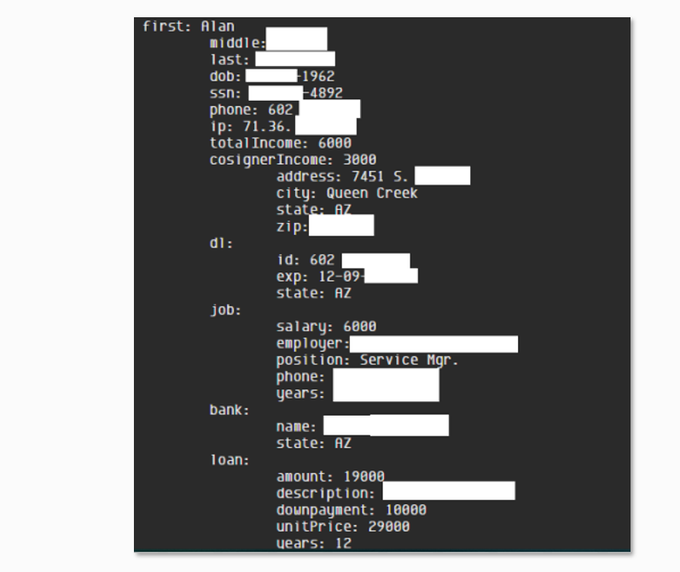
A sample of US Fullz that was posted by a threat actor on a hacking forum.
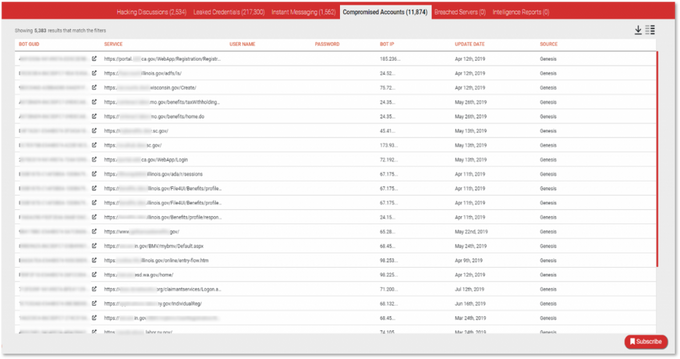
Another method used by criminal actors to obtain PII is by sourcing information from malware-bound information stealers or banking trojans, which provide the potential attacker with a nice trove of data to abuse. KELA has access to some prominent botnet trading platforms that sell access to data and personal information harvested from botnet-infected machines all over the world. We commonly refer to these as compromised accounts, which are essentially credentials, cookie sessions and additional technical fingerprints which are offered for sale on automated underground marketplaces such as Genesis and more. These accounts are breached and stolen from victims’ computers generally via infections by banking trojans or other stealers. By using KELA’s cybercrime research and investigation tool, DARKBEAST, we were able to detect more than 10,000 accounts with access to Unemployment Insurance Offices portals across all states in the US.
Accounts found in malware infected machines whose data is sold in underground botnet markets (as seen in KELA’s DARKBEAST platform)
Once obtained, these criminals actors have the first and critical piece of information necessary to begin their fraudulent claims.
Unemployment Fraud Step-by-Step Guides
Obtaining “Fullz” is the basis required in order to perform an unemployment claim, but it doesn’t end there. Cybercriminals are constantly looking for clear written out methods for submitting fraudulent PUA claims. In response, numerous criminal actors are constantly sharing step-by-step tutorials across a plethora of cybercrime forums and closed Telegram groups where they explain how to file an application for unemployment benefits. Guides are sold starting from tens of dollars and are promoted alongside “proofs” of their effectiveness. At times, cybercriminals can even get their hands on an all-inclusive package where they can purchase both the guides alongside “Fullz” that match the targeted US state. A few examples of the guides being offered across various closed Telegram groups can be seen below:
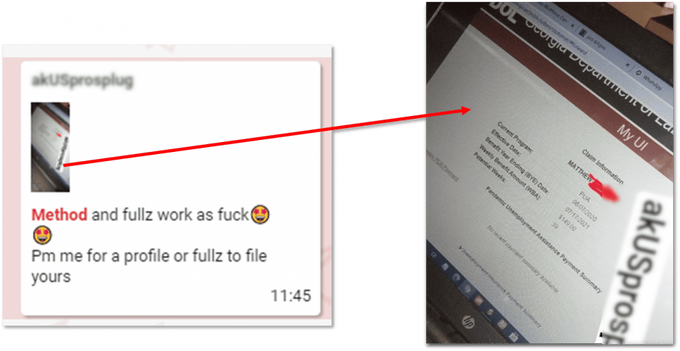
A post in a Telegram group where an actor shows a screenshot of a fraudulent unemployment claim from the state of Georgia.
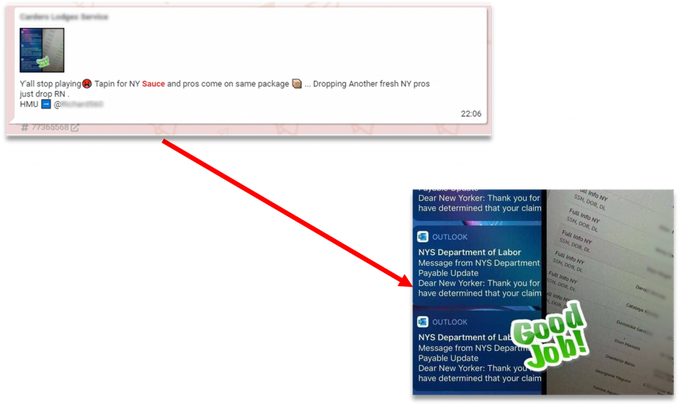
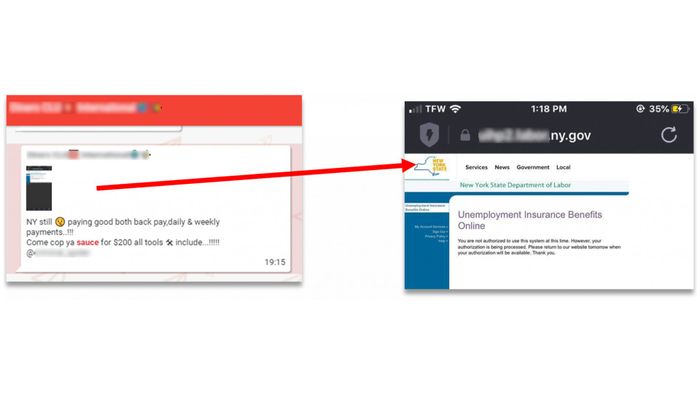
A post in Telegram whereby a threat actor offers “sauce” (methods) for unemployment claims to NY state.
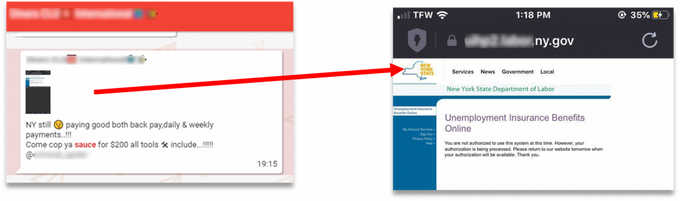
A Telegram post by a threat actor who sells New York “sauce” (method) for unemployment claims.
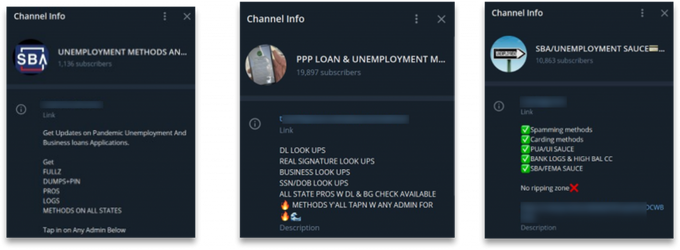
These tutorials have been circulating in Telegram communities for several months already – some including specific details of PUA benefits that are provided by each state, and others even including links to file the claims as well as details to the minimum and maximum amounts paid out by each state. Among these various communities, we also identified numerous Telegram channels, with thousands of members, that are dedicated specifically to those interested in unemployment fraud methods. Below are examples of some of these groups:
Telegram groups and channels dedicated to PUA-related fraud methods in April 2021.
Bypassing the ID.me Identity Service
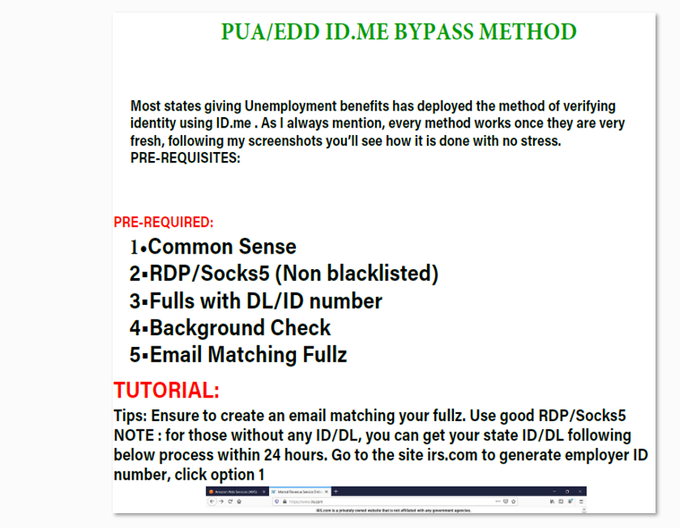
Chatter related to another type of PUA fraud has been growing tremendously over the last few months as cybercriminals pushed efforts towards abusing US citizens’ unemployment benefits. Cybercriminals have been seen sharing methods and services that help bypass the ID.me identity service, which is used by citizens to access digital government services. Among our research, we obtained a 15-page document, titled “PUA/EED ID.ME BYPASS METHODS,” which continues to be exchanged between actors in prominent fraud-related Telegram channels.
An id.me bypass guide circulated online by threat actors.
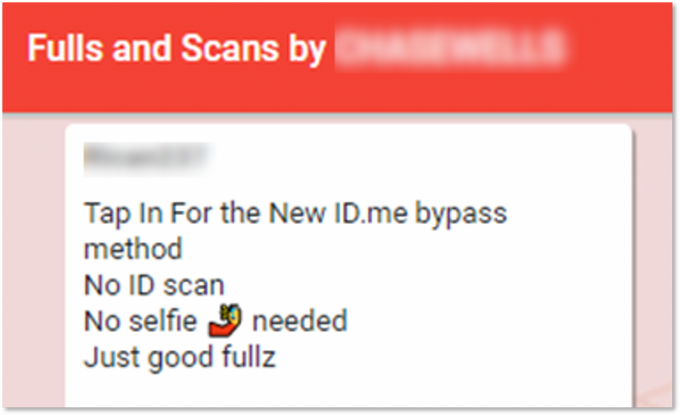
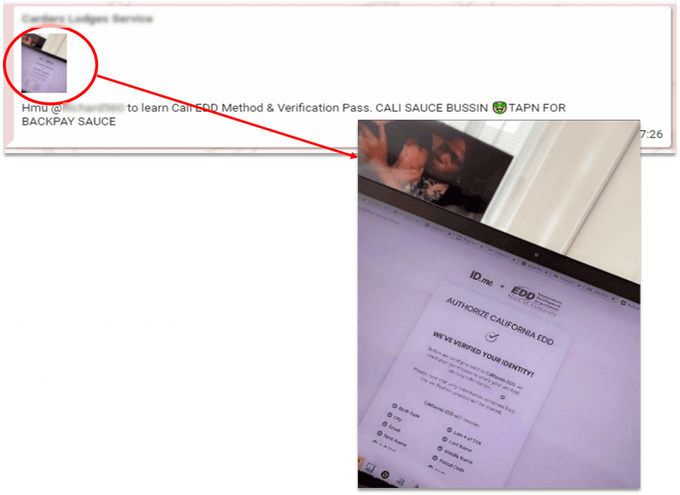
This step-by-step explanation guide contains instructions on how to file a fraudulent unemployment claim in the states that use ID.me for an additional layer of identity verification and fraud protection. In continuation of the previous methods mentioned, this also requires just minimal technical skills and “Fullz” that should contain a Driver’s License or Employer ID number (EIN) to bypass the ID.me protection layer. Similar to other guides that we previously mentioned, the ID.me bypass guide does not refer to any technical “bypassing,” but rather explains the use of identity theft to create a request for an ID.me account. Once created, the fraudsters can easily begin applying for benefits. In addition to the guides, threat actors post messages and pictures that allegedly prove that their “methods” (aka “sauce”) are valid and are sold for $50-$400.
A post in a Telegram channel offering to sell an id.me bypass method.
Bottom Line, It’s Easy…
Unlike some more sophisticated cyberattacks, executing a fake unemployment claim proves to be a simple route for cybercriminals looking to make quick and easy money. The combination of stolen personal identifiable information (Fullz) that is harvested by cybercriminals and shared online, with accessible how-to guides for claiming fraudulent unemployment applications is making this type of scheme easy to carry out, especially for fraudsters with minimal technical skills. Underground platforms have become booming markets for these “products,” where “how-to” guides have been circulating for months back already, providing fraudsters with almost everything they need to capitalize on the pandemic and steal money from the US government. In most states, these unemployment benefits continue to be in place. Here, the awareness and security of the human factor plays a big role. Every individual must be aware of the possibility of having their identity stolen and must be cautious of who they choose to provide their details with. Criminal actors in the cybercrime underground can and will take advantage of any opportunity that rises, including the COVID-19 unemployment benefits. US citizens are actively being targeted not only by US-based fraudsters, but as seen above, by Russian-speaking ones as well. Individuals’ information that is already exposed and circulating in the cybercrime underground is at risk, and every US citizen – whether eligible for unemployment benefits or not – must take the necessary precautions to defeat these cybercriminals before they cause harm.