Catch Me If You Can: The LockBit Edition – Explained
Updated May 9, 2024.
It’s Not Over, Yet…
Law enforcement has once again targeted LockBit, the notorious ransomware gang, but the end of this group remains uncertain. Despite multiple high-profile crackdowns, LockBit’s operations continue unabated, illustrating their resilience against law enforcement efforts. This ongoing challenge is highlighted by insights from KELA’s threat researchers, recently featured on Wired.com. As we delve deeper into LockBit’s history and recent takedown attempts, it becomes clear why a full shutdown might still be a distant goal.
The Rise of LockBit From Stealth to Spotlight
LockBit initially emerged in 2019, discreetly operating under the radar by leveraging the Maze ransomware blog to post victim information under the alias “provided by LockBit.” This early period also saw them establishing a presence on cybercrime forums, primarily for affiliate recruitment. By 2020, LockBit had launched their own victim-shaming blog, marking a step up in their visibility, although their activity levels remained comparatively low. The significant turning point came in 2021, when they ramped up their operations, actively publishing victim data and expanding their affiliate program, thereby transitioning to a full-fledged ransomware-as-a-service (RaaS) model.
LockBit Reigns Supreme as Most Active Ransomware Group
LockBit’s ransomware has undergone several iterations to enhance its effectiveness and evade detection, and several versions appear to have been in the use by its affiliates now. The group employs a strategic affiliate model, enticing hackers with a share of the ransom profits, which has proven effective in expanding their operations globally. This model not only maximizes their reach but also diversifies their risk, making the group more resilient to countermeasures.
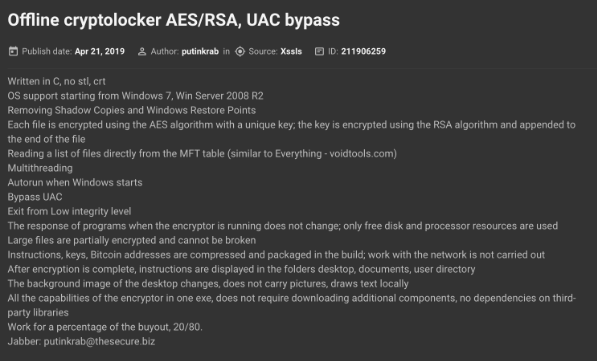
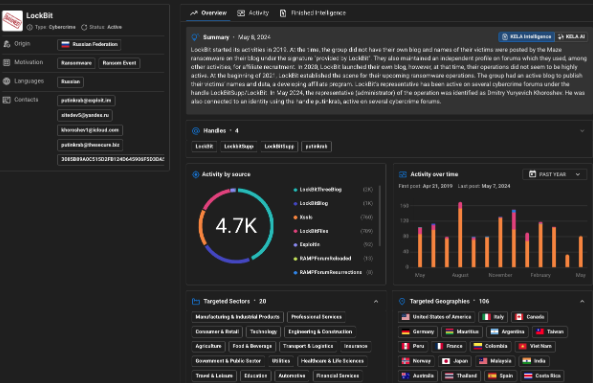
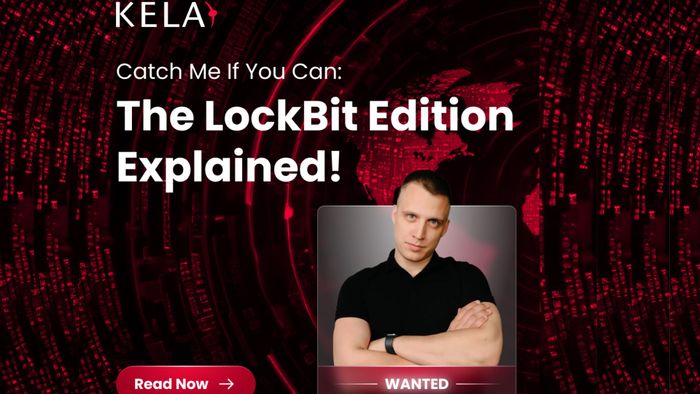
Between 2023 and 2024, LockBit established itself as the most active ransomware group, outpacing others in terms of the number of disclosed victims. he group maintained a robust presence on cybercrime forums, engaging heavily under various aliases, including LockBitSupp and LockBit. Based on the data disclosed by operation Cronos, the group’s administrator was also active under the handle putinkrab. During this period, LockBit made its first public announcement about its transition to a ransomware-as-a-service (RaaS) model under the alias putinkrab, a pivotal moment auto-translated and analyzed by KELA’s platforms. Their blog served as a vital communication channel, showcasing their relentless activity and evolving tactics.
LockBit’s first announcement about RaaS under the handle putinkrab (auto-translated by KELA platform)
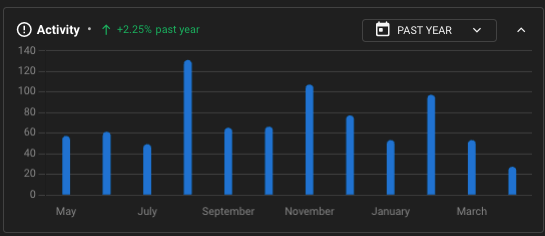
LockBit’s blog activity in May 2023-May 2024
Law Enforcement Crackdown - Operation Cronos
The international response to LockBit’s rise has been formidable, with collaborative efforts from law enforcement agencies across 11 countries, alongside Europol. The pinnacle of these efforts was Operation Cronos in February 2024, which resulted in the seizure of several LockBit ransomware domains. This action temporarily disrupted their operations; however, KELA’s close monitoring revealed that some domains remained active under LockBit’s control.
Following a notable security breach on February 19, 2024, due to these vulnerabilities, LockBit acknowledged the lapses and alleged that the FBI orchestrated the attack to prevent the release of sensitive information. Despite these challenges, LockBit swiftly recuperated, launching new domains that mirrored the previously blocked ones. They not only restored information about prior victims but also added over 150 new ones.
Continued Tensions in May 2024
The cyber community watched closely as law enforcement agencies updated notices on the seized LockBit group’s Tor website about plans to reveal the identities of its operators on May 7, 2024, and intentions to shut down the website by May 10, 2024. Skepticism was prominent; on Twitter, a representative of LockBit claimed that law enforcement’s statements were misleading and insisted that their operations were still active.
True to their word, on May 7, law enforcement disclosed the identity of Dmitry Yuryevich Khoroshev, also known as LockBitSupp and putinkrab. Following this revelation, the US Department of State announced a $10 million reward for information leading to Khoroshev’s capture, with the US, UK, and Australia imposing sanctions. Detailed analysis of the seized data revealed 7,000 unique ransomware builds, over 2,110 negotiation instances, and 194 active affiliates.
Reactions Within Cybercrime Forums
The cybercrime community’s reaction to these developments was mixed. While some predicted the decline of LockBit, others showed continued support, discussing the resilience of their operations and the implications of law enforcement actions. Following the announcement about Khoroshev, skepticism about the accuracy of the identification prevailed in forums, with some dismissing it as mere publicity. There was also speculation about Khoroshev’s potential cooperation with Russian law enforcement.
With the recent identification of Dmitry Yuryevich Khoroshev as a key figure behind LockBit has marked a pivotal moment in the saga. However, the disclosure has not crippled the group’s operations. On the contrary, it appears to have had a limited impact on their activities, as evidenced by their continued victim postings and recruitment. Looking ahead, the evolution of ransomware tactics and the persistence of groups like LockBit suggest that the fight against cybercrime will remain a complex and ongoing endeavor.
What’s Next for LockBit - The KELA Perspective
Kela Platform’s Analysis of LockBit’s Continuous Risk
While recent law enforcement actions made headlines, our analysis at KELA suggests dismantling LockBit will be a marathon, not a sprint.
Their core operations remain unscathed, affiliates seem unshaken, and they continue to add victims. LockBit even refuted the disclosed administrator identity, casting doubt on its accuracy and highlighting their ability to adapt. We believe a full takedown is far from certain, and LockBit may continue to pose a significant threat in the foreseeable future. In the narrative of cybercrime, LockBit’s journey transcends mere incidents; it symbolizes the perpetual struggle against advancing digital risks and the endeavors to curb them. Despite significant law enforcement interventions, LockBit’s tenacity underscores the imperative for constant watchfulness and the adoption of sophisticated cybersecurity strategies.
As we peer into the future, LockBit’s resilience echoes the enduring presence of cyber threats, emphasizing the paramount significance of proactive cybersecurity defense measures.
If you’ve read this far, thank you! We invite you to explore KELA’s platform with a free trial to see how we can help you stay ahead in cybersecurity.