What Is a Threat Intelligence Platform and Why Do You Need One?
Threat intelligence platforms help teams focus on high-impact cyber threats, track threat evolution, and improve their ability to anticipate attacks. They provide external context that other tools lack, facilitating stronger threat detection & prioritization, reduced alert fatigue, and stronger regulatory compliance.
Published July 21, 2025

A threat intelligence platform (TIP) is a specialized solution that collects, aggregates, enriches, and operationalizes threat data from multiple sources, such as open-source intelligence, dark web activity, and internal telemetry. It transforms unstructured data into actionable intelligence, giving organizations visibility into external threats and adversary behavior.
The primary goal of a TIP is to equip security operations, incident response, and threat hunting teams with the context needed to detect, prioritize, and mitigate threats effectively. TIPs complement tools like SIEMs and SOAR platforms by enhancing external threat visibility and enabling a more proactive, intelligence-driven defense strategy.
» Ready to level up your threat intelligence? Get started with KELA
What Is a Threat Intelligence Platform?
Organizations today face a mix of opportunistic and targeted threats, from large-scale phishing campaigns to zero-day exploits and nation-state-backed intrusions. However, many security teams are still overwhelmed by raw feeds and generic indicators.
In simple terms, here’s what a TIP helps clarify:
- Who is behind a threat (threat actor groups, motivations)
- How they operate (TTPs, attack infrastructure, malware families)
- Where data is being sold or shared (dark web, Telegram, forums)
Instead of sifting through isolated alerts, teams using a TIP can focus on high-impact threats, track threat evolution, and improve their ability to anticipate attacks, rather than just react to them.
Key point: Threat intelligence platforms help teams cut through the noise by transforming scattered indicators into clear, contextual insights. Instead of reacting blindly, organizations can focus on the most relevant threats and anticipate attacker behavior with confidence.
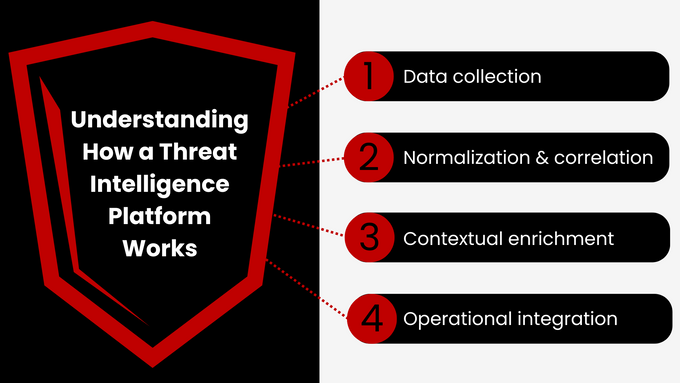
How a Threat Intelligence Platform Works
A Threat Intelligence Platform (TIP) acts as the engine behind effective cyber threat intelligence by transforming raw data into usable, contextual insights. It supports every stage of the CTI lifecycle, from gathering data to delivering intelligence directly into your security tools for action.
1. Data Collection
TIPs aggregate information from threat feeds, forums, paste sites, malware repositories, telemetry, and darknet marketplaces. This wide range of sources ensures early visibility into emerging threats and adversary activity that may not yet be detectable within internal systems.
2. Normalization & Correlation
Collected data is formatted into a standard structure (e.g., STIX), then cross-referenced to detect relationships between IOCs, campaigns, and actors. This process removes inconsistencies across data formats and enables automated correlation that reveals broader attack patterns.
3. Contextual Enrichment
The TIP overlays TTPs, MITRE ATT&CK mapping, actor profiles, and timeline data to deepen understanding. By adding this context, security teams can quickly assess threat severity, understand attacker behavior, and prioritize response efforts accordingly.
4. Operational Integration
Actionable intelligence is distributed to downstream systems (SIEM, SOAR, XDR) for alerting, blocking, and automated response. This ensures that intelligence doesn’t just sit in dashboards, as it directly fuels detection logic, automated workflows, and faster decision-making.
Use Cases of Threat Intelligence Platforms Across Industries
Threat intelligence platforms offer tailored value across various sectors, helping organizations proactively identify, contextualize, and respond to emerging threats.
Key examples of how TIPs support security efforts in specific industries include:
- Finance: TIPs monitor dark web marketplaces and infostealer logs for leaked credentials, enabling early fraud prevention and account protection.
- Healthcare: They offer visibility into ransomware activity and exploited vulnerabilities, allowing teams to prioritize defenses and safeguard patient data.
- Government: TIPs help track nation-state threats and phishing infrastructure, empowering agencies to preempt attacks and protect public services.
- Enterprise: They detect supply chain risks and brand impersonation attempts, allowing for swift remediation and stronger partner security.
Main takeaway: TIPs deliver specialized value across industries by detecting relevant threats early, reducing risk and protecting critical assets specific to each sector.
» Learn how to prevent phishing attacks
TIP vs. SIEM, SOAR, & EDR: What’s the Difference?
Understanding the distinctions between a threat intelligence platform (TIP) and other common security tools, like SIEM, SOAR, and EDR, is essential for building a well-rounded cybersecurity strategy. While these tools often work together, each plays a specific role in the broader security ecosystem.
1. TIP (Threat Intelligence Platform)
Centralizes, enriches, and operationalizes external threat intelligence. Helps threat intelligence analysts understand who, why, and how behind threats, supporting proactive defense. TIPs also connect internal events with external indicators, like dark web chatter or active malware campaigns, to enhance decision-making and threat prioritization.
2. SIEM (Security Information and Event Management)
Aggregates and analyzes log data from internal sources in real-time to detect anomalies or potential incidents. It offers visibility into network and system behavior but lacks deep context about external threats unless paired with a TIP.
3. SOAR (Security Orchestration, Automation, and Response)
Automates workflows and responses based on input from SIEMs, TIPs, or other tools. Designed to streamline and scale incident handling, SOARs rely heavily on the quality of intelligence they ingest, making TIP integration key for smarter automation.
4. EDR (Endpoint Detection and Response)
Focuses on detecting and responding to threats at the endpoint level using behavioral analysis and attack signatures. EDR is strong at identifying suspicious activity on devices but often lacks the broader threat context that TIPs provide.
Primary Focus | External threat intelligence | Log aggregation & correlation | Workflow automation | Endpoint detection & response |
Focus Area | Outside the perimeter | Inside the environment | Across multiple tools | Endpoints |
Key Input | Threat feeds, dark web, OSINT | Internal logs, network data | TIPs, SIEM, playbooks | Endpoint telemetry |
Contextual Enrichment | Yes (actor, campaign, TTPs) | Limited | No (depends on TIP) | Minimal |
Best At | Threat context & prioritization | Event visibility | Response speed & consistency | Detecting endpoint compromise |
Here’s a quick breakdown of which solution fits which use case, so your team can respond with the right tool at the right time:
- Want to know who’s targeting your industry or leaking your data on the dark web? → Use a TIP
- Need to collect and correlate internal logs for signs of suspicious activity? → Use a SIEM
- Looking to automate your incident response and reduce manual effort? → Use a SOAR
- Trying to detect malicious behavior on endpoints and stop lateral movement? → Use an EDR
Benefits of Using a Threat Intelligence Platform
- Stronger threat detection & prioritization: TIPs collect and enrich threat data from diverse sources, helping security teams identify and focus on the most relevant and high-risk threats.
- Reduced alert fatigue & smarter workflows: Filtering noise and scoring threats based on risk allows TIPs to reduce false positives and streamline workflows through integrations with SIEM, SOAR, and other tools.
- Proactive defense capabilities: TIPs enable predictive threat analysis and dark web monitoring, allowing organizations to act on leaked data, exposed vulnerabilities, and attacker movements before breaches occur.
- Improved efficiency & analyst well-being: Automation and centralized intelligence free up time for strategic tasks, reducing burnout and enabling security teams to work more effectively and sustainably.
TIPs and Regulatory Compliance
Threat intelligence platforms help organizations meet regulatory requirements by providing visibility into threat activity, supporting risk mitigation, and offering audit-ready documentation:
- NIST compliance: Supports identification and analysis of threats as outlined in the NIST Cybersecurity Framework, helping guide proactive defense strategies.
- ISO/IEC 27000 alignment: Aids in implementing best practices for information security risk management, including threat detection and ongoing evaluation.
- GDPR readiness: Helps detect data leaks and supports timely breach notification, crucial for meeting GDPR’s data protection requirements.
- Audit support: Centralizes threat data and incident history for streamlined regulatory reporting and stakeholder transparency.
- Cyber resilience: Improves the ability to anticipate and respond to evolving threats through continuous intelligence gathering and threat tracking.
Future-Proofing With TIPs
Modern cyber threats are evolving rapidly, making it essential for organizations to adopt tools that can predict, adapt, and respond in real time. Threat intelligence platforms (TIPs) play a key role by transforming dynamic threat data into actionable insight:
- AI-powered threats: TIPs help detect and correlate indicators tied to AI-generated malware, phishing lures, and emerging attack patterns.
- Dark web monitoring: TIPs scan hidden marketplaces for exploit kits, leaked credentials, and insider chatter, providing early warnings.
- Predictive defense: With machine learning and TTP mapping, TIPs support proactive mitigation and faster response to future threats.
» Not convinced? Read more about protecting your organization from future cybercrime
Why CaaS Demands Better Threat Visibility
Cybercrime-as-a-service (CaaS) has made it easier than ever for unskilled attackers to launch sophisticated campaigns using ready-made tools. From ransomware kits to access credentials and phishing platforms, these services lower the barrier to entry and multiply the number of active threat actors.
TIPs provide the visibility needed to monitor this underground activity, identify emerging threats early, and prevent attackers from gaining a foothold.
» Learn more: What is ransomware?
Using KELA's Threat Intelligence Platform for Modern Threats
KELA’s Threat Intelligence Platform is designed for today’s fast-moving threat landscape, offering real-time visibility into dark web forums, malware ecosystems, and attacker infrastructure. It goes beyond static threat feeds by delivering contextual intelligence that helps teams detect, prioritize, and respond before threats escalate.
Their integration with tools like MISP or Wazuh supports unified threat management, while automation features minimize manual tasks and analyst burnout. These often-overlooked benefits translate into faster response times, reduced stress, and stronger overall resilience.
» Ready to get started? Try KELA for free or learn more about our cyber threat intelligence platform