CTI Market is Changing: 5 Things you Need to Know
The CTI market is undergoing rapid transformation, driven by AI advances, regulatory pressure, and industry consolidation. This post breaks down five critical shifts that are redefining how threat intelligence is created, consumed, and used to drive real security outcomes.
Updated June 12, 2025

Don't have time to read? Listen here:
Since 2017, cyber threat intelligence (CTI) has evolved from a niche cybersecurity function to a core pillar of security operations. Once reserved for elite security teams, CTI is now a mainstream capability, integrated into security programs across industries.
With over 200 vendors in the space, ongoing acquisitions, and AI-driven intelligence reshaping how organizations consume and operationalize intelligence, 2025 marks a critical turning point for the CTI market. However, the expansion of all-in-one security platforms, increasing reliance on automation, and the role of AI introduce both opportunities and challenges for practitioners.
In this blog, I’ll explore the five things that threat analysts and security teams need to know to stay ahead in this evolving industry.
» Skip to the solution: Try KELA's cyber threat intelligence for free
1. CTI is Powering the Next Phase of Threat Detection
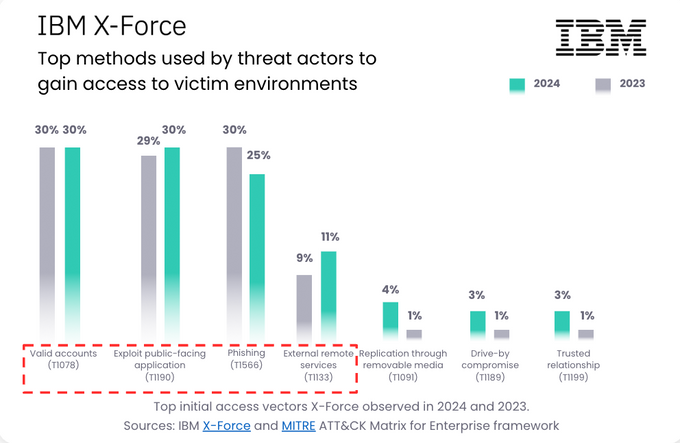
Recent data from IBM X-Force shows that 96% of cyber attacks in 2024 start from four key initial access vectors:
Valid account compromise: 30% (MITRE ATT&CK T1078)
Exploit public-facing application: 30% (MITRE ATT&CK T1190)
Phishing: 25% (MITRE ATT&CK T1566)
External remote services: 11% (MITRE ATT&CK T1133)
These are not just isolated tactics; they're part of a broader, well-organized cybercrime supply chain. Infostealer malware has become a powerful enabler, fueling a surge in Initial Access Brokers (IABs) who harvest and sell compromised credentials on underground forums. This ecosystem makes it easier than ever for ransomware operators, fraudsters, and espionage groups to gain entry into targeted environments without ever writing a line of code.
Enter CTI—a critical security tool and foundational capability to stay ahead of attackers, make informed decisions, and reduce the impact of attacks. By thwarting credential compromise and phishing attacks, CTI helps defenders significantly reduce adversary behavior and ultimately breaches.
Threat intelligence is no longer an optional add-on. It's becoming the connective tissue between siloed security tools, providing the context needed to close visibility gaps and disrupt adversaries earlier in the attack chain.
» Here's everything you need to know about cyber threat intelligence
2. Investment Cycles, M&A Activity Create Opportunities and Challenges
Over the past five years, threat intelligence has gone through distinct phases of investment, consolidation, and renewed momentum. From 2019 to 2022, CTI became a major investment area for cybersecurity firms and financial investors. Companies recognized that intelligence wasn’t just an add-on but a fundamental part of enterprise security.
Some of the Most Notable Acquisitions Included:
Mandiant acquired by Google ($5.4B, Sept 2022)
Digital Shadows acquired by ReliaQuest ($160M, June 2022)
Flashpoint acquired by Audax Private Equity (Feb 2022, Undisclosed)
Additionally, CrowdStrike entered the CTI market in 2021, signaling that endpoint security providers saw intelligence as a must-have. In 2023, cybersecurity funding slowed down due to macroeconomic factors, rising interest rates, and increased investor scrutiny.
This affected all tech sectors, including threat intelligence, forcing vendors to shift focus from growth to profitability.
But despite the 2023 slowdown, 2024 saw a resurgence in investments and acquisitions, driven by both strategic buyers and financial investors:
Recorded Future acquired by Mastercard ($2.65B, Sept 2024)
Cybersixgill acquired by BitSight ($115M, Nov 2024)
CyberInt acquired by Check Point (Oct 2024, Undisclosed)
SOCRadar raised $25M (May 2024)
ZeroFox acquired by Haveli Investments ($350M, May 2024)
Some of these acquisitions were strategic, as cybersecurity firms integrated threat intelligence into their existing platforms. Others were financial, with investment firms betting on the long-term potential of CTI.
This consolidation, however, presents a challenge: as independent intelligence providers become part of larger security ecosystems, neutrality may be compromised. Intelligence priorities could shift toward business interests rather than pure intelligence-driven objectives.
Security leaders must ask: is the intelligence I’m getting complete, unbiased, and actionable? Or is it tailored to serve a vendor’s broader portfolio?
For security teams that rely on fast, neutral, and deep intelligence to make decisions, the wave of consolidation means it’s more important than ever to evaluate the independence, coverage, and focus of your CTI providers. The right intelligence partner should enhance—not dilute—your ability to understand and respond to threats in real time.
» Read more: Benefits of automating CTI into SOC activities
3. A Shift to All-in-One Security Platforms has Pros and Cons
Another major trend in 2025 is the integration of CTI into broader security platforms, merging it with Digital Risk Protection (DRP), External Attack Surface Management (EASM), and Third-Party Risk Management (TPRM).
For example, EASM and Breach and Attack Simulation (BAS) platforms are using CTI to model adversary behaviors, map likely attack paths, and simulate real-world threats based on known TTPs. Also, DRP vendors are integrating CTI feeds to monitor for leaked credentials and exposed assets across dark web marketplaces—proactively identifying risks before they're exploited.
While the integrations present new opportunities for consolidated tech stacks, the shift to all-in-one security solutions also introduces critical challenges:
More data, less validated intelligence: Many vendors prioritize data aggregation over deep intelligence gathering.
Over-reliance on automation: Machine-driven alerts replace analyst verification, increasing false positives.
Surface-level insights: Broad visibility does not always translate to deeper threat understanding.
Organizations adopting all-in-one platforms must evaluate whether they are truly enhancing security outcomes or just expanding their tech stack.
4. AI Impacts Threat Intelligence
Artificial Intelligence is transforming the way threat intelligence is collected, analyzed, and acted upon—but its integration into cybersecurity workflows comes with both benefits and challenges.
On the upside, AI significantly accelerates intelligence collection, enabling the rapid processing of vast amounts of open-source and dark web data that would take human analysts far longer to analyze. It also enhances detection capabilities by identifying subtle correlations between disparate data points, uncovering threats that might otherwise go unnoticed. AI plays an increasingly important role in automating response efforts, allowing security teams to react more quickly to emerging threats. Additionally, new tools like Digital Cyber Analysts are transforming how security teams consume, prioritize, and act on threat intelligence.
However, the use of AI in threat intelligence is not without drawbacks. One major issue is the risk of false positives, as AI-generated intelligence can lack the nuanced judgment of human analysts, leading to alert fatigue and wasted time. Many AI-powered tools also suffer from redundant functionality, often duplicating tasks already handled by existing CTI platforms. And perhaps most concerning, the rise of AI-powered cyber threats, such as deepfakes, AI-generated malware, and adversarial prompt injections, has created new vulnerabilities and attack surfaces.
In fact, over the past year, KELA observed an increase of 200% in the mentions of malicious AI tools such as WormGPT, WolfGPT, DarkGPT, FraudGPT and others in cybercrime communities compared to 2023.
The key takeaway here? While human expertise remains critical, threat intelligence operations must embrace next-generation AI tools to stay ahead of AI-powered threats. It’s no longer just about enhancing efficiency—it’s about leveling the playing field. In today’s threat landscape, the only way to combat adversaries using AI is to fight AI with AI.
» Learn more how AI is transforming cybersecurity
5. Cyber Intelligence Regulations Drive CTI Adoption
Governments around the world are ramping up regulatory requirements for cybersecurity reporting, pushing organizations to improve their operational resilience and risk management frameworks.
In the EU, two key regulations are leading this charge: the Digital Operational Resilience Act (DORA) and the NIS2 Directive. DORA emphasizes the need for enhanced cybersecurity resilience within the financial sector, while NIS2 expands incident reporting obligations and raises the bar for risk management across critical industries.
As these regulations take effect, CTI is becoming a core pillar of compliance strategies—providing the visibility, context, and early warning capabilities needed to meet these mandates. For threat intelligence teams in EMEA, adopting advanced CTI tools is no longer optional, it’s essential to staying compliant, resilient, and ahead of evolving regulatory expectations
» Not convinced? Here are more reasons you need cyber threat intelligence
The Road Ahead for Threat Intelligence
The future of threat intelligence isn't just about collecting more data, it's about turning that data into decisions. As organizations face more sophisticated attacks, tighter regulatory requirements, and a rising wave of AI-powered threats, CTI must evolve from a supportive function to a strategic enabler.
The organizations that thrive in 2025 and beyond will be those that treat intelligence not as an add-on, but as a core operating system for cybersecurity.
» Ready to get started? Contact us to learn more about our cyber threat intelligence services