Work Smarter in 2025: 7 Benefits of Automating CTI into SOC Activities
Updated February 5, 2025.

“Get stronger without any physical effort.” No, unfortunately we’re not talking about that new year’s weight-lifting resolution you scribbled on a napkin — we’re focused on your cybersecurity posture.
It might sound too good to be true, but there’s one way to strengthen your cybersecurity without adding headcount to the SOC team or finding more hours in the day — and that’s automating Cyber Threat Intelligence (CTI) into day-to-day Security Operation Center (SOC) processes.
This article looks at seven business benefits of making this shift, and describes how organizations can see measurable value while making SOC operations leaner and more agile, by integrating CTI within existing SIEM and SOAR solutions.
Improved Threat Detection and Threat Hunting
By continually ingesting threat feeds and intelligence automatically, and correlating these with internal logs, alerts and events, SOC teams can detect threats faster and place them in the right context. Automation makes it easier to proactively identify and hunt for emerging threats as well, particularly when augmented with machine learning that identifies patterns and anomalies.
Faster Response Times and Mitigation
When SOC teams automate CTI, incidents can be automatically prioritzed based on their contextual threat level, so that analysts can immediately get to work on high-risk issues. By using playbooks and predefined workflows, automated responses such as modifying SIEM detection rules or triggering actions in SOAR can be automated when a threat is known, which can reduce response time down to near real-time.
Enhanced Decision Making
With greater context, the SOC team has more information at their disposal when making critical time-sensitive decisions. Depending on your CTI platform, information can include Indicators of Compromise (IOC), attacker TTPs, Phishing Domains or patterns which are invisible without machine learning in place. Organizations can also set up an automated risk scoring profile, so that teams can strategically prioritize at a glance.
Support for Lean SOC Teams
Automating correlation, prioritization and other SOC analyst tasks reduces the volume of alerts that make it to the human analysts workbench. This has a positive impact on minimizing alert fatigue. In addition, routine tasks in the analysts day — from malware analysis to data enrichment and IOC validation can all be automated to free up time for higher value tasks and investigation. (And maybe even the odd coffee break ☕.)
Organizational Efficiency
Like the number of bands you don’t recognize, threat intelligence data is growing in volume every day. Automation gives SOCs the ability to manage the increasing load without increasing headcount, and adapt to new intelligence feeds or integrate with various tools and platforms using webhooks and APIs. Standardized automated processes ensure a uniform response to threats, and that everyday repetitive tasks are performed consistently.
Cost Reduction
By reducing the need for manual effort, automation naturally optimizes resource utilization and lowers operational costs for the business. Zooming out, automating CTI into the SOC’s everyday work helps to mitigate threats faster, and reduces the impact of an incident when it occurs — providing a higher return on investment for CTI tools and SOC operations as a whole. More bang for your buck? Yes please.
Intelligence Sharing
When CTI tools automatically collect intelligence from a wide range of diverse sources, including external threat feeds, the Deep and Dark Web, honeypots, or even other security vendors, this can be rapidly disseminated to enhance collective security, facilitating the seamless sharing of intelligence to anyone from external partners to industry peers or government agencies.
Leveraging KELA to Automate CTI into Everyday SOC Tools
At KELA, we know how crucial it is to incorporate CTI into your SOC processes, and how integral SIEM and SOAR tools are to the way your SOC functions. While SIEM collects, normalizes and analyzes vast amounts of log and event data, SOAR extends this with incident response, orchestrated workflows and pre-defined playbooks to handle threats effectively. At KELA, we like to think of our cyber threat intelligence as the missing MVP of the team.
To support the SOC team, at KELA we have built specific SIEM and SOAR integrations and playbooks that empower organizations to consistently scale security operations and accelerate threat response to defend against modern threats.
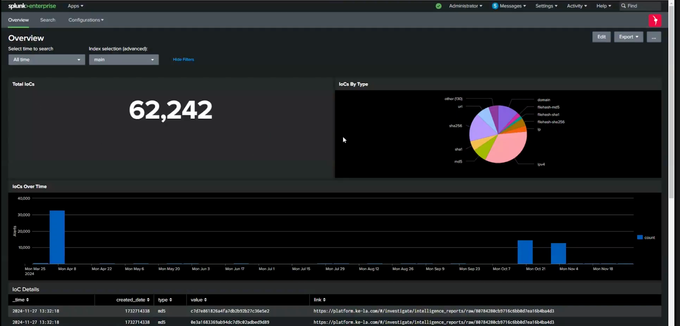
One example is our KELA apps for Splunk, IOC and Monitor, which are built to increase your effectiveness inside Splunk SIEM. Monitor allows security teams to view and analyze critical security events pulled from the KELA platform, monitoring identity and credential-based events, risks and vulnerabilities which directly impact your organization and its network infrastructure. From the Splunk dashboard, SOC teams can view compromised accounts, specific leaked credentials, network vulnerabilities, and Dark Web insights and discussions from hacker groups. This information can be organized by severity, geographic distribution and more.
The KELA IOC app adds a proactive touch, enabling SOC teams to identify and track potential threats ingested from KELA’s vast data lake into Splunk. Indicators of Compromise will automatically populate your Splunk dashboard, keeping you two steps ahead of an attack, and linking back to the original source for more information where necessary. SOC teams can view context-rich information for each IOC, including IP addresses, file hashes, and domains. Data is formatted using Splunk standards, allowing for easy integration into any custom-built dashboard, blending in seamlessly with your existing workflows.
Make Automate your 2025 CTI Buzzword
When Cyber Threat Intelligence is automated into your everyday SOC tasks, the seven benefits outlined above become business-as-usual. KELA’s SOAR and SIEM integrations, as well as custom playbooks for monitoring and response allow SOC teams to discover and act decisively against real-time risks and vulnerabilities, including:
Getting immediate visibility into compromised credentials, sensitive data and exposed assets, and proactively identifying potential threats.
Understanding when and where data and account leakage has occurred to take corrective and protective action to protect your customers and employees.
Investigating IOCs faster with deep context, resulting in fewer false positives and reduced alert fatigue.
Monitoring malicious activity on a global scale, and taking preemptive steps to fortify defenses and reduce risk before an attack can occur.
Accelerating remediation by pinpointing the sources of attacks and vulnerabilities — tailored to your organization.
Speak to one of our experts about your current SOC workflows, and learn how KELA can seamlessly automate CTI into the way you work. Your SOC team will thank you for it.