Data Breach or Infostealer - What’s the Real Culprit?
KELA has uncovered what may be a growing phenomenon where attackers claim to have infiltrated company networks, when in reality they are leveraging compromised credentials that have been harvested through logs from infostealer malware.
Updated May 13, 2025

No time to read? Listen to the article here:
“The greatest trick the devil ever played was convincing the world he doesn’t exist.” Well, today — the real trick may be convincing the world that a data breach does exist, when actually, credentials and other data is likely to have been stolen by infostealer malware. Let’s break down this new tactic, and how it works to help threat actors welcome in their next pay day.
Don’t Take an Attacker’s Word For a Data Breach
Newsflash: just because a threat actor says something, that doesn’t make it true. KELA has uncovered what may be a growing phenomenon where attackers claim to have infiltrated company networks, when in reality they are leveraging compromised credentials that have been harvested through logs from infostealer malware.
Infostealer malware is built to infiltrate systems and steal sensitive information — from login credentials to network information. Infostealers can extract information from many sources, including web browsers, password managers, and clipboard data, to name just a few. However, an infostealer attack is not the same as a data breach. In a data breach, millions of records can be disclosed or leaked, and information pertaining to an entire company can be at risk through lateral movement across a network. In the case of infostealer malware, a single machine is infected. Of course, this machine could include credentials to sensitive services of the company, which means the impact could still be extremely dangerous.
Examples of This Data Breach Lie in the Wild: OpenAI and CheckPoint
Let’s look at two recent examples which explain how this tactic works. First up, in February 2025, the threat actor “emirking” posted on BreachForums, claiming they have access to more than 20 million account access codes for OpenAI. By analyzing the sample that the threat actor shared of 30 OpenAI credentials, and cross-referencing them with our own data lake of compromised accounts which were obtained from infostealer malware, KELA identified that all of the credentials shared by emirking originated in these compromised accounts.
Overall, KELA can assert with a high level of confidence that the compromised credentials offered for sale by emirking are not related to a breach of OpenAI systems, but rather part of a larger dataset scraped from a mix of sources where infostealer logs are sold. As the affected individual’s credentials were taken from different infostealer campaigns — this shines a light on the wide threat of infostealers and the need for proactive defense. Altogether in 2024, KELA collected more than three million compromised accounts related to OpenAI users. If an attacker bundled them all together, that would look like quite the data breach indeed.
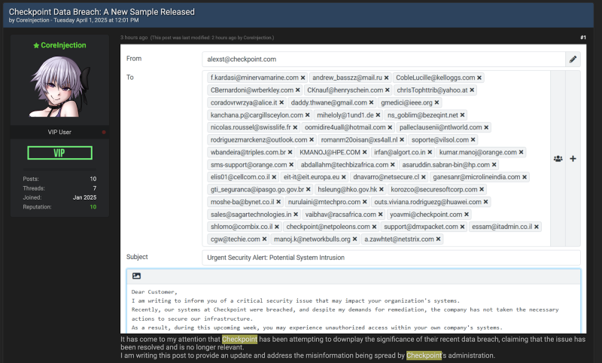
More recently in April 2025, threat actor “CoreInjection” claimed on BreachForums that they had successfully breached CheckPoint, and exposed the data of over 18,000 users, despite CheckPoint announcing that these were false claims. To ‘prove’ their claim, the attacker shared a link with 350+ user records that were obtained during the breach, alongside the screenshot below — a draft email ready to be sent from a CheckPoint email address to multiple recipients.
After reviewing the sample, KELA found it to contain 380 lines of credential information to usercenter.checkpoint.com, structured in a URL: Username: Password format. However, comparing this data against KELA’s data lake revealed that these lines were old samples of credentials that had originated in infostealer malware infections, making this “breach” similar to the fake attack claimed against OpenAI.
Why Would Attackers Claim a Data Breach Anyway?
On the threat actor’s side of the table, claiming that they have successfully completed a data breach against a company sounds more dramatic and dangerous to outsiders, giving their attack credibility and impact, and getting more attention from the media, potential victims, and buyers on forums. Even the claim of a breach, (if it fools people) can provide your average hacker with some serious street cred.
Claiming a breach can also help threat actors to hide the real infection source, which is individual machines, and make it harder for the victim to trace the origins of an attack or understand the scope of what’s happening. Confusion works in their favor.
Finally, a data breach is also more profitable. If buyers will believe that the data is fresh and large scale, then of course it is worth more than some random logs bundled together from multiple infostealers. That allows attackers to maximize profits.
How Can Organizations Protect Themselves?
Heard of the boy who cried wolf? Well, the vast number of infostealer logs available in cybercrime forums makes it easy for attackers to become “the threat actors who cry data breach”, time and time again. This tactic can make businesses panic, thinking an attacker has more access than they really have. This could cause decision makers to act rashly, such as paying a ransom without any real need.
However, as well as taking a pause for thought — it should also make you think about how you can better protect your company against credential exposure and address any potential vulnerabilities that leaked credentials may create.
Our latest report looks in detail at the spiralling infostealer threat in 2025, and dives into the data under the hood of 300 infected machines to help identify the individuals most vulnerable to these threats, and to uncover common risk profiles and behavioral patterns. Our advice includes:
Active monitoring: Early detection of compromised credentials on cybercrime forums means that your organization can block potential security threats quickly by changing passwords or revoking access.
Proactive access management: Actively manage access levels and privileges across the organization, promptly revoking access when employees exit, and regularly auditing roles and permissions.
Enforcement of Multi-Factor Authentication (MFA): MFA should be implemented on all accounts, especially those with access to sensitive data or critical systems, such as VPNs, remote desktop services, and administrative accounts.
To read our full research on the Infostealer Epidemic, and to access more ideas for protecting your organization, download the report here.
And of course, to start understanding your own exposure, start your free trial of KELA’s proactive real-time threat intelligence solution here.