Effective Threat Hunting With APT Profiling: Leveraging MITRE Framework
Master effective threat hunting by profiling APT groups and utilizing the MITRE ATT&CK framework. Strengthen your defense and detect threats before they strike.
Published September 4, 2025

When it comes to threat hunting, understanding the behaviors of APT actors is crucial. Profiling these groups and tracking their tactics, techniques, and procedures (TTPs) helps organizations anticipate potential attacks. By leveraging frameworks like MITRE ATT&CK, businesses can proactively identify patterns and strengthen their defenses.
However, effective profiling requires more than just mapping known threats—it also involves integrating real-time intelligence and continuously adapting to evolving adversary tactics.
» Start with KELA and stay ahead in identifying advanced threat actors and operations
What Is an APT Group?
An advanced persistent threat (APT) group is a highly skilled and resource-rich threat actor, often sponsored by nation-states. These groups use advanced technology and techniques to conduct targeted cyber attacks. Their operations are stealthy, often remaining undetected for long periods using zero-day exploits and custom malware.
An APT’s primary goal is to:
- Steal sensitive data, including intellectual property, state secrets, and financial information.
- Conduct politically motivated operations, such as espionage and election disruption.
- Demonstrate power or exert influence through cyberattacks.
4 Threat Actors to Keep an Eye On
1. Kimsuky
Kimsuky is a North Korean state-sponsored advanced persistent threat (APT) group that focuses on cyber espionage, targeting government institutions, think tanks, and experts in South Korea, Japan, and other regions.
Recent activity
- Throughout early to mid-2025, Kimsuky conducted sophisticated spear-phishing attacks targeting diplomatic missions worldwide, particularly embassies in South Korea and various European countries. These attacks imitated trusted diplomatic contacts and used GitHub as a covert command-and-control platform.
2. Lazarus Group
Lazarus Group is a notorious North Korean cybercrime and espionage collective that has been active since at least 2009, known for executing both financially motivated and politically driven operations.
Recent activity
- In February 2025, the Lazarus Group carried out a major attack on the Dubai-based cryptocurrency exchange Bybit, stealing over $1.5 billion worth of Ethereum by exploiting vulnerabilities in the platform’s multi-signature wallet setup. This allowed them to gain unauthorized access to private keys and move the funds through untraceable channels, continuing their focus on financially motivated operations to support the North Korean regime.
3. APT41
APT41 is a Chinese state-sponsored group that combines espionage activities with financially driven cyberattacks across multiple sectors, including government, logistics, media, and technology.
Recent activity
- Released a novel malware called TOUGHPROGRESS in late 2024, which uses Google Calendar as a covert command-and-control channel to hide malicious activity within legitimate cloud traffic.
- Leveraged cloud abuse techniques alongside zero-day exploits, employing advanced persistence mechanisms such as UEFI bootkits and custom TLS implementations to maintain access.
4. Salt Typhoon
Salt Typhoon is a Chinese cyberespionage group responsible for deeply infiltrating U.S. state-level networks and critical infrastructure sectors.
Recent activity
- In December 2024, it was revealed that Salt Typhoon had infiltrated eight U.S. telecom providers, with evidence suggesting the attacks had been active for one to two years.
- By February 2025, new reports showed the group was still active, focusing on internet-facing Cisco network devices used by telecom operators.
» Learn about the difference between leaked credentials and compromised accounts
Key Elements of an Effective APT Profile
- Overview: A brief description containing the APT's aliases and known objectives. This sets the foundation for understanding the group’s history and goals, helping security teams focus their detection strategies.
- Motivation: This section highlights the APT’s motivations—whether they are engaged in espionage, political objectives, hacktivism, or financial gain. Understanding their motivation allows teams to anticipate potential attack vectors and behaviors.
- Identified campaigns: Here, operations and campaigns attributed to the APT are outlined, along with timelines, targeted sectors, and any changes in tactics. This historical context helps security teams recognize patterns and adapt defense mechanisms accordingly.
- TTPs: The section covers the tactics, techniques, and procedures (TTPs) used by the APT. This information is crucial for formulating targeted defense strategies, and using frameworks like ATT&CK and D3FEND ensures comprehensive protection against threats.
- Malware and tools: Highlighting the malware and tools used by the APT gives security teams insight into what to look out for. This can be directly incorporated into detection rules, such as Sigma Rules and Yara Rules, to bolster the organization's defenses.
- Region and sectors: Understanding the regions and sectors targeted by the APT helps in adapting defenses to specific threats that an organization may face. This allows security teams to prioritize and tailor security measures based on geographical or industry-specific trends.
- Additional information: Additional insights, such as communication methods or information gathered from deep dark web forums, can provide critical clues about the APT's methods and behaviors. This aids in further refining threat-hunting strategies and anticipating future attacks.
» Learn more: Reasons you need cyber threat intelligence
Challenges in Tracking Advanced Threat Actors
Complex Attribution
APTs disguise their origin by routing traffic through multiple countries or setting up infrastructure elsewhere. This makes it difficult to pinpoint their true source and anticipate future attacks.
Constantly Evolving Tactics
Their TTPs change frequently, exploiting vulnerabilities and evading detection with new tools and techniques. Traditional defenses struggle to keep pace with these adaptations.
Use of Third-Party Tools
APT actors leverage common third-party tools, making it harder to distinguish malicious activity from legitimate operations within a network.
What Is the MITRE ATT&CK Framework?
The MITRE ATT&CK provides a taxonomy for describing cyberattacks used by adversaries. This framework helps cybersecurity professionals better understand and defend against threats.
The framework is designed to categorize adversary behavior to help understand and defend against cyberthreats and be used in adversary emulation exercises.
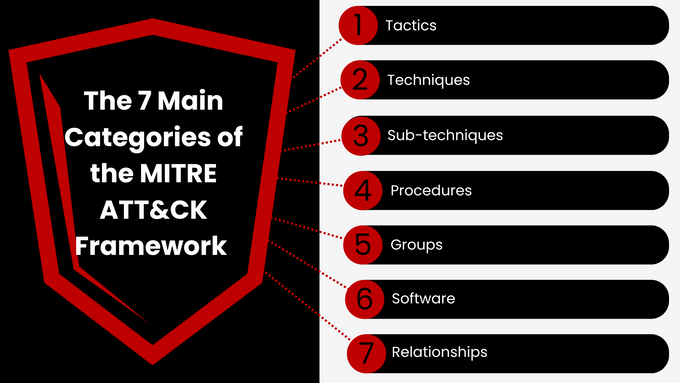
The 7 Main Categories of the MITRE ATT&CK Framework
1. Tactics
Tactics classify the technical objectives that adversaries aim to achieve during an attack. There are 14 different tactics, each representing a distinct phase of an attack and comprising various techniques:
- Initial access: Gaining entry to the victim’s environment.
- Execution: Running malicious code on the target system.
- Persistence: Maintaining access to the victim's environment.
- Privilege escalation: Gaining higher-level privileges.
- Defense evasion: Avoiding detection by security measures.
- Credential access: Obtaining credentials to further access the environment.
- Discovery: Gathering information about the target system and environment.
- Lateral movement: Moving through the environment to reach other systems.
- Collection: Gathering data of interest for exfiltration.
- Exfiltration: Removing the data from the victim’s environment.
- Impact: Damaging or disrupting the victim’s environment.
- Command and control: Communicating with compromised systems.
- Reconnaissance: Gathering information about the target before launching the attack.
- Resource development: Preparing infrastructure for future attacks.
2. Techniques
Techniques describe the specific methods adversaries use to accomplish their objectives. They represent how a particular goal is achieved within the scope of a tactic.
3. Sub-techniques
Sub-techniques provide more detailed information about a specific technique. They help further define how adversaries execute their attacks.
4. Procedures
Procedures outline step-by-step instructions for carrying out a particular technique or sub-technique. These instructions detail how an attack is performed in real-world scenarios.
5. Groups
Groups refer to sets of related intrusion activities that are tracked under common names. These groups are often associated with specific threat actors or adversary campaigns.
6. Software
Software includes the tools, malware, and utilities that adversaries use to execute behaviors modeled in the ATT&CK framework. These tools enable various attack techniques.
7. Relationships
Relationships define the connections between different tactics, techniques, procedures, and software. They map how adversaries operate and link different elements of an attack.
» Discover how KELA’s Threat Actors Hub can help you uncover your adversaries
» Learn how you can prepare your organization for the future of cybercrime
5 Steps to Take for Effective MITRE ATT&CK Utilization
- Understand the framework: Familiarize yourself with the MITRE ATT&CK framework, which maps a variety of TTPs used by cyber adversaries across three domains: Enterprise, Mobile, and ICS.
- Identify threat actor groups: Organizations must assess the adversaries most likely to target them based on risk factors such as geography, industry, and technology stack. Historical attack data and threat intelligence provide valuable insights into potential threats.
- Gather threat intelligence: Analyze known TTPs of targeted adversaries through OSINT, vendor reports, and internal forensic investigations. Understanding attack patterns helps security teams anticipate and mitigate threats effectively.
- Identify vulnerabilities: With collected intelligence, assess weaknesses in your security posture. Determine which tactics and techniques are hardest to monitor and pose the greatest risk to your environment.
- Prioritize mitigation efforts: Focus on addressing the most critical vulnerabilities first. Identify areas of over- or under-investment in security to allocate resources efficiently and strengthen defenses.
» Understand how threat actors breach and exploit your data
Enhancing Defense Against Threat Actor Groups With KELA Cyber
Tracking APT groups and operations requires more than just the MITRE ATT&CK framework. KELA enhances its capabilities by integrating diverse intelligence sources, including OSINT, incident response data, and real-time alerts. This integration allows organizations to identify key adversary groups, gaining valuable insights into their tactics and techniques.
By aggregating intelligence and prioritizing the most critical threats, KELA can help your organization refine its defense strategies, ensuring it stays ahead of evolving APT threats and minimizing their potential impact.
» Ready to begin? Contact us to try KELA for free