Espionage Exposed: Inside a North Korean Remote Worker Network
Thousands of North Korean IT workers are operating under fake identities in the global freelance economy, securing jobs at major companies to fund state weapons programs and conduct espionage.
Updated October 10, 2025

Thousands of North Korean IT workers are hiding in plain sight, blending into the global freelance economy, building your apps, or even designing your infrastructure. Behind their fake LinkedIn profiles and AI-generated headshots lies a state-backed scheme funding weapons programs and espionage.
In this blog, KELA reveals how North Korean operatives infiltrate global companies, the tools and tactics they rely on, and what this means for organizations across industries. The full report, including exclusive and full details not covered in this blog, is available to KELA customers.
» Strengthen your cybersecurity with KELA's expertise
Background: How North Korea’s Remote Work Scheme Operates
Since at least 2018, North Korea has deployed thousands of skilled IT workers abroad as part of a state-backed effort to generate foreign currency and support its sanctioned weapons program.
Operating under fake identities, often from China, Russia, Hong Kong, Southeast Asia, or even within North Korea via controlled internet access tools, these workers use VPNs, VPSs, Western accomplices, and “laptop farms” to conceal their origins and bypass verification. They secure freelance or full-time jobs on major platforms by leveraging stolen or rented identities, AI-generated photos, and fraudulent portfolios, ultimately infiltrating companies across technology, crypto, transportation, and critical infrastructure sectors.
Once inside, they either quietly funnel salaries back to the regime or exploit their access to deploy malware, steal data, or conduct extortion. Microsoft tracks these networks under clusters like Jasper Sleet and Moonstone Sleet, estimating over 10,000 operatives active worldwide. Beyond IT, KELA also identified North Korean remote workers in the architecture field, highlighting broader risks spanning espionage, sanctions evasion, safety concerns, and unauthorized access to sensitive infrastructure designs.
In recent years, as North Korea’s remote worker scheme has expanded, security researchers have increasingly exposed their tactics, making detection easier. Groups like TheRavenFiles, North Korean Internet, and the Chollima Group, along with independent researchers on X, have revealed that DPRK operatives rely more on social engineering and deception than on technical intrusions to infiltrate companies.
Recent data leaks of worker email addresses showed frequent use of Gmail and recurring patterns (birth years, animals, colors, tech terms, mythology, or Western/Russian identities) often with simple, reused passwords. These findings highlight how North Korean operatives disguise themselves and secure jobs through low-tech but effective methods.
» Learn about the common threats and vulnerabilities that lead to data breaches
Infostealer Evidence
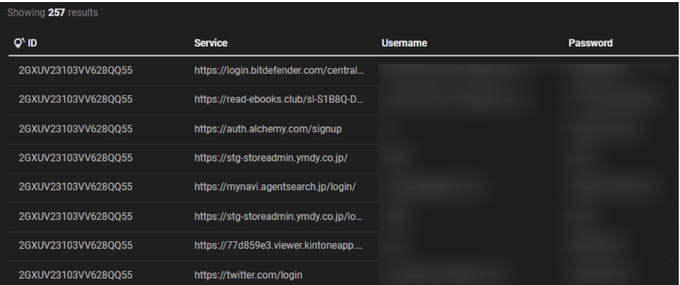
In 2025, TheRavenFiles and Chollima Group uncovered dozens of North Korean-linked email addresses, which KELA traced in infostealer logs from machines in Japan, Russia, Hong Kong, and the United States. These machines appeared as developer workstations with common tools like Python, Node.js, and JetBrains IDEs, but also showed unusual entries such as Chinese apps (QQPC Manager, QQPlayer), suspicious executables (“Call.exe”, “Time.exe”), Protect_2345Explorer, Qihoo’s 360bpsvc, and NetKey, a DPRK-owned VPN.
Compromised accounts spanned job and freelance sites (Indeed, Upwork, LinkedIn), developer and collaboration platforms (GitHub, GitLab, AWS, Slack), financial and e-commerce services (Amazon, Stripe, Binance), social media (Twitter, YouTube, Instagram), and educational or productivity tools like Codecademy, Apple ID, and Zoho.
» Here's everything you need to know about infostealers
Case Study: North Korean Operator in Architecture and Design
KELA’s investigation into a North Korean operator began with public reporting exposing multiple aliases across LinkedIn and GitHub. KELA found that North Korean remote workers are also active in the industrial design and architecture field for work in multiple U.S. states. Their involvement could pose risks related to espionage, sanctions evasion, safety concerns, and access to sensitive infrastructure designs.
The operator’s GitHub activity demonstrated alleged technical skills, including AI and machine learning, web development, automation, and programming. Repositories created in 2023 contained various Google Drive links and uploaded files. Analysis of these files revealed spreadsheets with hundreds of email addresses, likely used for registering accounts on platforms such as Google, Fiverr, Upwork, and GitHub. One spreadsheet even contained a full identity, including names and emails, for each U.S. state.
» Don't get confused: The differences between vulnerability vs. threat vs. risk
Further examination of the Google Drive files uncovered multiple compressed archives with distinct purposes. Folders named “CJC”, and “Info” archives contained the most sensitive information. Within these, KELA found resumes categorized by profession, proposal templates for client outreach for interior and outdoor designs, and folders corresponding to multiple online platforms, including freelancer marketplaces.
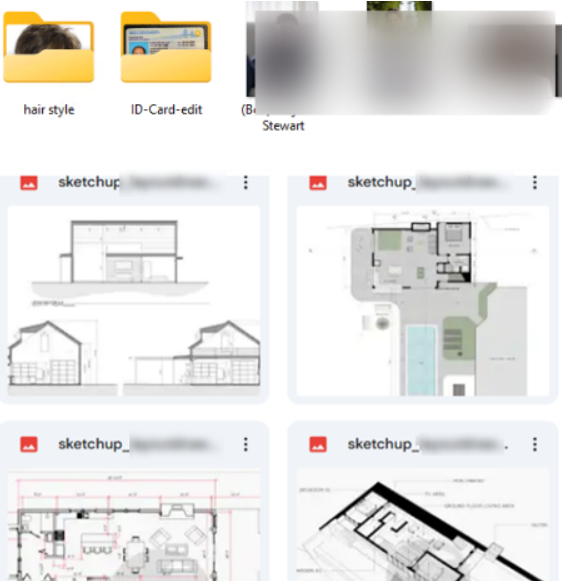
Other folders appeared to relate to fabricated personas, with personal photographs, KYC documentation, and identity-editing files, suggesting preparation for cryptocurrency platform use or online impersonation. The Info archive included credentials for numerous services, virtual phone numbers, proxy configurations, and additional LinkedIn profiles, highlighting a systematic approach to maintaining multiple online identities.
Among the files recovered, a folder contained images specifically for editing hairstyles, likely intended to modify profile photographs for online accounts. Subfolders included ID-card edits and other facial adjustments, suggesting the operator used these images to create or alter digital personas. Some of the edited hairstyles corresponded to profile photos found on public platforms, indicating that these resources were actively applied to maintain professionally fabricated identities across multiple accounts.
» Understand why you need cyber threat intelligence for your organization
The operator’s workflow also showed highly structured identity management using IxBrowser. Different email addresses were used specifically for platform registration, client communication, or internal account management. Analysis revealed the receipt of freelance job offers, particularly in structural engineering, primarily from U.S.-based clients. The actor’s digital habits reflected operational security, using cryptocurrency wallets, proxies, and frequent translation from Korean to English to maintain engagement with English-speaking targets. Geolocation data from some accounts pointed to Russia, particularly the Khabarovsk area near China, where North Korean IT workers have previously been reported.
» Learn about five trends shaping Initial Access Broker activity
Conclusion: An Expanding Threat Beyond IT
The investigation into North Korean remote workers reveals a highly organized, state-backed network that extends far beyond IT roles. KELA’s analysis shows that these operatives are active not only in technology and cybersecurity but also in industrial design, architecture, and interior design, accessing sensitive infrastructure and client projects under fabricated identities. They maintain multiple personas, use developer workstations with legitimate tools, and exploit simple but effective methods to secure work and remain undetected.
» Get started for free with KELA and strengthen your cybersecurity
Takeaways for Businesses
KELA’s investigation highlights that North Korea’s remote worker program is not only expanding in scale but also diversifying into non-traditional fields such as architecture and industrial design. This broadens the potential impact from cyber intrusion to risks involving infrastructure security, sanctions evasion, and even espionage. For organizations, the threat is no longer limited to IT departments—it now touches hiring, HR processes, and cross-functional oversight.
What to Watch For:
Suspicious freelancer profiles: Limited work history, unverifiable portfolios, AI-generated headshots, or recurring email/address patterns (e.g., birth years, animals, colors, mythological names).
Identity inconsistencies: Resumes with mismatched details, multiple personas linked to the same “worker,” or unusual geolocation data when verifying candidates.
Unexpected skill overlaps: Candidates offering expertise across disparate fields, such as software development and structural engineering, may indicate fabricated or pooled identities.
What Security Teams Should Be Doing:
Partner with HR and recruiting. Security awareness can’t stop at the SOC - companies should educate HR and recruiting staff on common red flags tied to DPRK operatives. This includes training to spot falsified identities, running enhanced background checks, and integrating vetting tools into the hiring pipeline.
Extend monitoring to third-party access. Contractors, freelancers, and vendors should be included in identity and access management reviews, ensuring that account provisioning, MFA enforcement, and offboarding are consistently applied.
Treat hiring as part of the threat surface. Just as phishing awareness is taught company-wide, the risk of state-backed remote workers should be acknowledged as a potential attack vector, one that can be mitigated through stronger cross-department collaboration.
By viewing recruitment and contracting through a threat-intelligence lens, organizations can close a blind spot that North Korean operatives have been exploiting for years.
» Worried about infiltrators in your workforce? Get KELA's threat intelligence