4 Holiday Shopping Scams Businesses Must Watch This Season
Holiday shopping scams surge during peak sales, from fake websites to phishing and counterfeit vouchers. Awareness and verification are key.
Published November 4, 2025

The holiday season brings excitement and deals, but it also attracts cybercriminals looking to exploit shoppers. From Black Friday to Christmas sales, scammers use fake websites, phishing emails, counterfeit vouchers, and fraudulent order confirmations to steal personal and financial data. People lost over $3 billion to scams that started online, compared to approximately $1.9 billion lost to more “traditional” contact methods like calls, texts, or emails.
In this blog, we’ll explore the most common types of holiday shopping scams, real-world examples like IKEA, Temu, and Amazon, and provide actionable ways to protect yourself and your business.
» Looking for an effective security solution? KELA provides the comprehensive support you need
Security Challenges in Peak Shopping Seasons
The combination of human behavior and heightened commercial activity creates an ideal environment for organized fraud. The following are some main driving factors that increase organizational risk during the holiday shopping season:
- Leveraging consumer urgency: Customers are often pressured by the fear of missing out (FOMO) to skip important security checks and ignore obvious red flags. It has been observed that around one in five shoppers intending to participate in the sales say they are willing to take the risk of being scammed just to clinch a better deal.
- Peak financial activity and stakes: The high number of transactions and the high average value during festivities guarantee great returns to fraudsters; hence, these dates serve as prime targets. The average scam purchase claim is over £700.
- Sophisticated threat technology: Modern fraud campaigns have become harder to distinguish from legitimate marketing, using incredibly convincing fake websites and pinpoint phishing attacks. The use of advanced techniques is being aided by AI technologies, especially large language models, which are used to create scam emails and fake websites that look more realistic.
- Vulnerability across digital channels: Vulnerability across digital channels: Criminals target shoppers on social platforms, where 47% of users have fallen victim to shopping scams.
» Learn how to prevent phishing attacks before they catch you
Indicators of Emerging or Active Shopping Scam Operations
Security teams should stay alert to both technical and behavioral warning signs that indicate active scam campaigns during peak shopping events.
Technical Indicators
- Fake shopping websites closely resembling legitimate ones, often with slight URL or domain name misspellings.
- New domain registrations tied to retail keywords such as Black Friday or Cyber Monday.
- Sites missing trust elements like HTTPS, contact details, or clear privacy and return policies.
- Short-lived websites hosted on low-reputation or rapidly changing hosting services.
- Malicious ads and phishing links distributed through social platforms — 72% of purchase scams originate from social media.
Behavioral Indicators
- Campaigns designed to trigger urgency or FOMO, leading users to make quick, unverified purchases.
- Unrealistically low prices or “too good to be true” offers used to collect payment data.
- Sudden traffic spikes or engagement on posts or ads promoting fake offers.
The Most Common Holiday Shopping Scams
1. Fake Shopping Websites (Phantom Retailers)
Threat actors create false “phantom” retail sites that imitate trusted brands using typo-squatted domains and polished designs to trick shoppers into fake purchases. These sites aim to collect sensitive data during checkout and are often hosted on unregistered or nonstandard Top-Level Domains (TLDs).
Key indicators:
- Suspicious domains and URLs: Fake sites often include small spelling errors, extra characters, or misplaced symbols in domain names that closely resemble real retailers. Checking for minor differences like “.co” instead of “.com” can reveal fraudulent activity.
- Missing security and trust markers: The absence of “https” encryption, contact details, or privacy and refund policies is a strong sign of a scam. These sites typically have minimal transparency about business location or ownership.
- Unusual domain registration patterns: Many fraudulent sites appear on new or low-trust TLDs and disappear quickly. Monitoring these registrations can expose coordinated scam campaigns early.
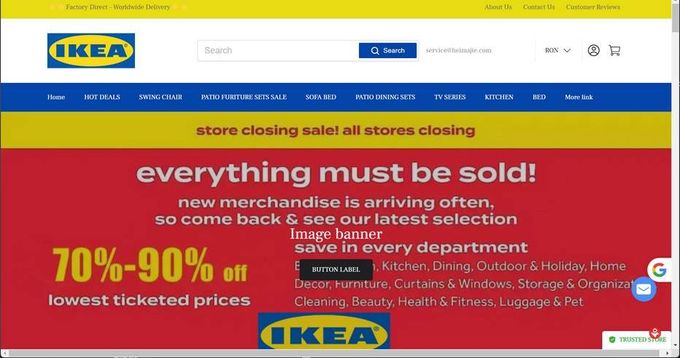
Real-world example: IKEA
During past Black Friday periods, fake IKEA websites such as “ikeaa-sale.com” and “ikea-blackfriday.shop” appeared online, mimicking the official ikea.com interface with copied product images, logos, and discount banners.
These websites lured shoppers in with “up to 90% off” deals on furniture and homeware", only to steal credit card data at checkout. Once flagged, the sites were quickly taken down — but not before hundreds of users had shared their personal and payment details.
Preventive measures: Organizations should educate consumers about verifying domains, promote secure payment channels, and implement brand monitoring to identify rogue sites using their name or logo.
» Make sure you understand how threat actors breach and exploit your data
2. Phishing (Account Verification and Credential Theft)
Cybercriminals exploit the Black Friday rush by sending emails or SMS messages that appear to come from trusted retailers, claiming that accounts need verification or have been locked. Victims are redirected to fake pages designed to steal credentials. In 2023, there were 3,500 phishing messages reported daily during Black Friday, with one in four Americans targeted by such scams.
Key indicators:
- Subtle domain or sender variations: Attackers register lookalike domains or alter legitimate company email formats slightly, such as replacing letters with similar-looking numbers.
- Urgent or emotional messaging: Messages often use fear or urgency, claiming accounts will be suspended or orders canceled unless action is taken immediately, leading users to click without verifying authenticity.
- AI-enhanced visuals and wording: With the growing use of AI, phishing attempts now feature flawless grammar, realistic branding, and accurate layouts, making manual detection more difficult and requiring stronger email filtering.
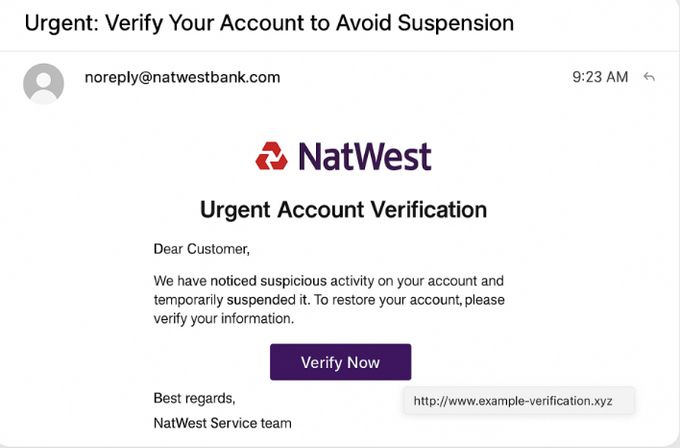
Real-world example: NatWest
In the UK, Action Fraud reported 151 cases of fraudulent emails sent to NatWest customers within just two weeks. The emails claimed that a customer’s online banking contact number had been changed, prompting recipients to click a link to “cancel the request.” That link redirected victims to a fake banking page where their financial details were stolen, giving fraudsters full access to their accounts.
Preventive measures: Consumers should never click links in unsolicited messages and verify details directly through retailer websites. Retailers should promote MFA adoption, strengthen email authentication, and warn customers about phishing tactics through visible communication channels.
» Make sure you understand the difference between leaked credentials and compromised accounts
3. Fake Coupons and Vouchers
Scammers frequently circulate fake discount codes or voucher links, particularly around major events like Black Friday, to attract clicks. These offers often spread through email or social media and redirect users to malware sites or phishing forms.
Key indicators:
- Unrealistic discount values: Offers with massive, round-number savings (like “90% off all items”) or deals inconsistent with known brand pricing often signal fake promotions.
- Unofficial communication channels: Fraudulent vouchers usually appear on social media pages or group messages rather than verified brand accounts, using links that differ from official domains.
- Visual inconsistencies: Scam vouchers often have poorly aligned logos, incorrect color schemes, or outdated design elements that subtly differ from authentic marketing materials.
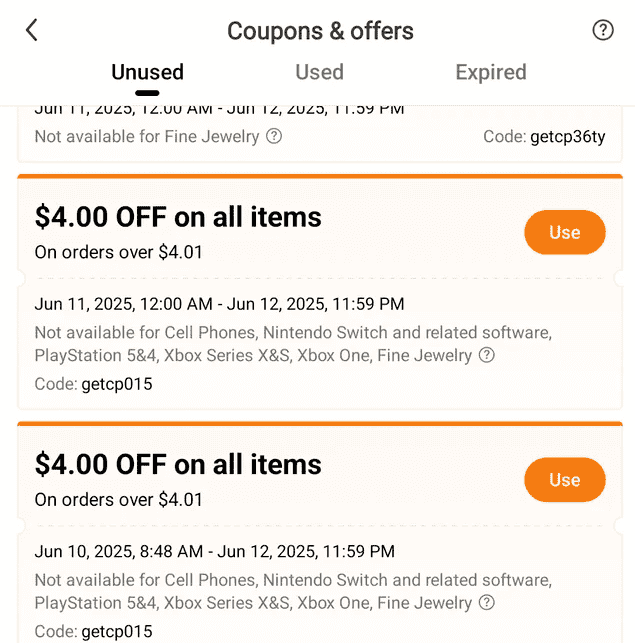
Real-world example: Temu
Fraudsters have impersonated popular marketplaces such as Temu, circulating “exclusive” coupon codes and deep-discount vouchers on social platforms and in DMs that redirect users to phishing pages or prompt downloads.
These fake promotions mimic Temu’s look and messaging to build trust quickly, then harvest payment or login data when users attempt to redeem the offer.
Preventive measures: Consumers should confirm offers through the retailer’s official website before engaging. Retailers should establish clear guidelines for verifying promotions and monitor social media for misuse of brand materials.
The NCSC advises shoppers to resist urgency-based deals and take time to verify authenticity before clicking.
» Learn more: How to reduce damage from info-stealing malware
4. Fake Order Scams (Confirmation Phishing)
This scam relies on spoofed “order confirmation” or “delivery update” emails that mimic legitimate retailers to create panic. Victims are urged to click a link to confirm or cancel their purchase, which instead leads to phishing or malware pages. These messages erode trust and can cause widespread reputational harm to real businesses.
Key indicators:
- Unexpected order confirmations: Messages confirming purchases the recipient never made, or with vague product details, are strong red flags.
- Sender and link discrepancies: Fake confirmations use misleading sender names or links that redirect to domains unrelated to the real retailer, often mixing legitimate brand elements with false addresses.
- Urgent tone and mismatched formatting: The message design might look professional, but text alignment, font use, or embedded images can differ slightly from official communication templates.
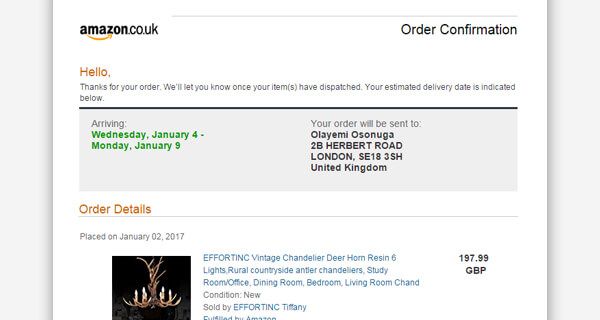
Real-world example: Amazon
Scammers frequently impersonate Amazon, sending emails about orders that were never placed. These messages may mimic Amazon’s logos, layout, and tone, creating the appearance of legitimacy. Amazon advises users to always check their actual order history via the official “Your Orders” page, and to use the Message Center to verify any email correspondence. If an email does not appear there, it was not sent by Amazon.
Preventive measures: Companies should increase brand spoofing detection, issue scam alerts during high-risk periods, and remind customers how to identify genuine communications.
Automated Holiday Shopping Scams: Detection and Defense
Countering AI-Driven and Automated Campaigns
Scammers increasingly use AI and automation—such as cloned websites, fake product listings, and chatbots—to scale attacks during high-volume shopping periods.
With online fraud losses of $12.5 billion in 2024, organizations must adopt proactive, intelligence-led defenses.
Key strategies:
- Technical barriers: Require MFA for all customer and internal accounts to block unauthorized access often exploited by automated phishing campaigns.
- Advanced intelligence gathering: Deploy autonomous systems to infiltrate dark web marketplaces and instant messaging groups. These systems uncover valuable artifacts like private APIs, hidden SIM gateways, and infrastructure links that refine detection of specific fraudulent operations.
- Continuous system refinement: Integrating targeted intelligence into detection systems improves the identification of sophisticated, automated scams that generic monitoring cannot catch.
» Read more: How cybercriminals exploit the power of generative AI
Adapting Post-Holiday Fraud Monitoring
Many victims only discover scams after the holidays, often during Q1 or tax season. Organizations must adjust post-holiday auditing and incident response workflows to reflect this lag.
Key strategies:
- Proactive customer due diligence: Monitor accounts, bank statements, and credit cards weekly, extending beyond the holiday rush.
- Immediate credit protection: Freeze compromised accounts to prevent further identity theft.
- Extended threat monitoring: Track social platforms, forums, and dark web marketplaces for emerging scam infrastructure or leaked personal data.
- Workflow adjustment: Post-holiday processes should integrate delayed reporting patterns, ensuring ongoing vigilance until fraud activity is fully accounted for.
» Not convinced? Here are the reasons you need cyber threat intelligence
How KELA Protects Your Business From Holiday Shopping Scams
KELA's threat intelligence platform monitors the cybercrime underground in real time, detecting the fake shopping sites, phishing campaigns, and fraudulent vouchers that surge during holiday sales events. Our automated systems infiltrate dark web marketplaces and instant messaging channels where scammers coordinate attacks against businesses like yours.
With KELA, your organization shifts from post-holiday damage control to real-time prevention, protecting both revenue and customer trust during the most critical shopping season.
» Ready to enhance your security this holiday season? Contact us to learn more or try KELA for free
FAQs
What makes holiday shopping scams more dangerous than regular phishing attempts?
Holiday scams exploit urgency and high transaction volumes when consumers are less cautious. Attackers use AI tools to create convincing fake websites that closely mimic legitimate retailers.
The combination of time pressure, attractive discounts, and professional-looking fraud makes consumers more likely to overlook warning signs.
Can my business be liable if scammers impersonate our brand during the holidays?
While direct liability varies by jurisdiction, brand impersonation damages customer trust and reputation.
Victims often associate fraud with the impersonated brand, leading to negative reviews and lost sales. Proactive monitoring and swift takedown actions minimize reputational harm.
What should our security team prioritize during peak shopping periods?
Monitor for brand impersonation across social media and new domain registrations, track stolen credentials appearing in dark web marketplaces, and establish rapid response protocols for confirmed fraud attempts.