Ransomware Threat Actor Profile: Qilin
This comprehensive analysis examines the Qilin ransomware-as-a-service group, which has emerged as a major cyberthreat since 2022. The post documents their aggressive campaign from August-September 2025, during which they executed 70 ransomware attacks in just 30 days across diverse industries and geographies.
Updated December 7, 2025

Qilin, also known as Agenda, is a ransomware-as-a-service (RaaS) cybercriminal group that has been active since 2022. Operating as a RaaS platform, Qilin provides affiliates with tools to carry out ransomware and extortion attacks. This business-like approach allows them to scale, target multiple geographies, and maintain a steady cadence of attacks.
Their arsenal includes ransomwxare variants that can strike Windows, Linux, and ESXi systems, giving them reach across diverse environments. Combined with a mix of initial access techniques, such as exploiting public-facing vulnerabilities, phishing campaigns, and leveraging stolen credentials, Qilin continues to expand its footprint. The motivation is clear: financial gain through ransom and extortion, but the strategy reveals a well-structured criminal enterprise.
» Get started for free with KELA and strengthen your cybersecurity
Notable Campaigns & Victims
In just one month (August 21 – September 21, 2025), Qilin launched 70 ransomware attacks, underscoring both the aggressiveness and sophistication of their affiliate model.
The group hit governments, healthcare providers, schools, manufacturers, financial institutions, and more, with victims spanning North America, Europe, Asia, Africa, and Latin America. Targets ranged from large organizations, such as Lee Enterprises (Media & Publishing), to municipal offices, including Spartanburg County, SC (Government & Public Sector), and even non-profits, like Kenya’s Office of the Registrar of Political Parties.
This mix of victims shows that Qilin is not focused on a single industry but casts a wide net that is disrupting critical infrastructure, local governance, and commercial sectors alike. By striking such diverse organizations, Qilin amplifies its global reputation and maximizes extortion leverage.
» Discover how the Qilin Ransomware Gang’s shift to affiliate-led ransom payments could signal a new threat
» Read more: Reasons you need cyber threat intelligence
Geographic & Sector Trends
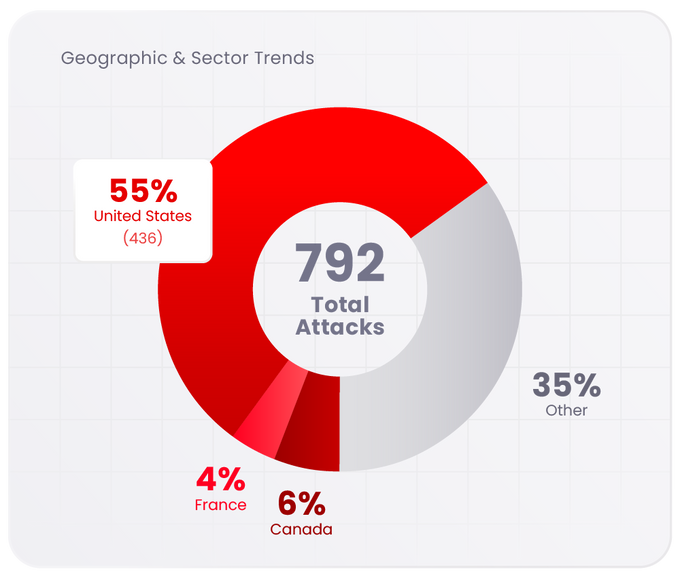
As of September 21, 2025, Qilin has claimed responsibility for 792 attacks since emerging in 2022, with the United States making up more than half of all victims (436). Other heavily targeted countries include Canada (6%) and France (4%), reflecting both the global reach and the preference for mature economies with high-value targets.
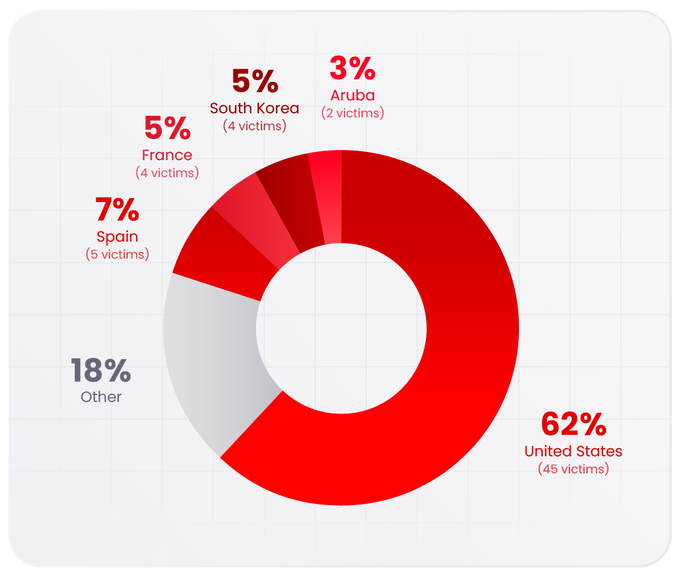
In the Last 30 Days, the United States Remained the Top Targeted Geography: The Breakdown Includes:
- United States (45 victims)
- Spain (5 victims)
- South Korea (4 victims)
- France (4 victims)
- Aruba (2 victims)
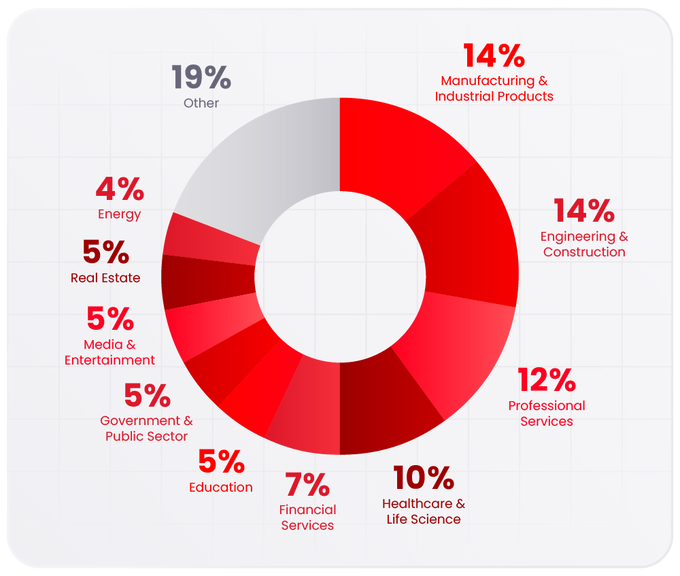
In the Last 30 Days, the Top Targeted Industries Included:
- Manufacturing & Industrial Products (14%)
- Engineering & Construction (14%)
- Professional Services (12%)
- Healthcare & Life Science (10%)
- Financial Services (7%)
When viewed over the long term, Professional Services and Manufacturing remain consistent top targets—likely because these organizations often balance sensitive data, limited security maturity, and high pressure to resume operations quickly.
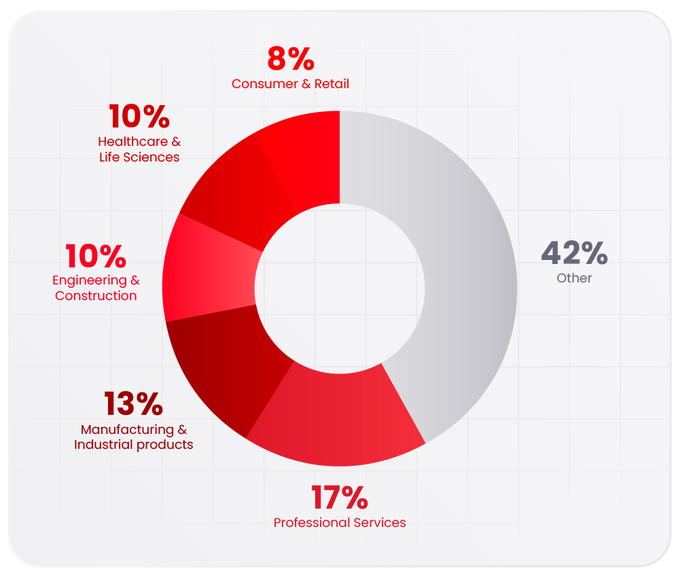
The Top 5 Sectors Since 2022 Include:
- Professional services (17%)
- Manufacturing & Industrial products (13%)
- Engineering & Construction (10%)
- Healthcare & Life Sciences (10%)
- Consumer & Retail (8%)
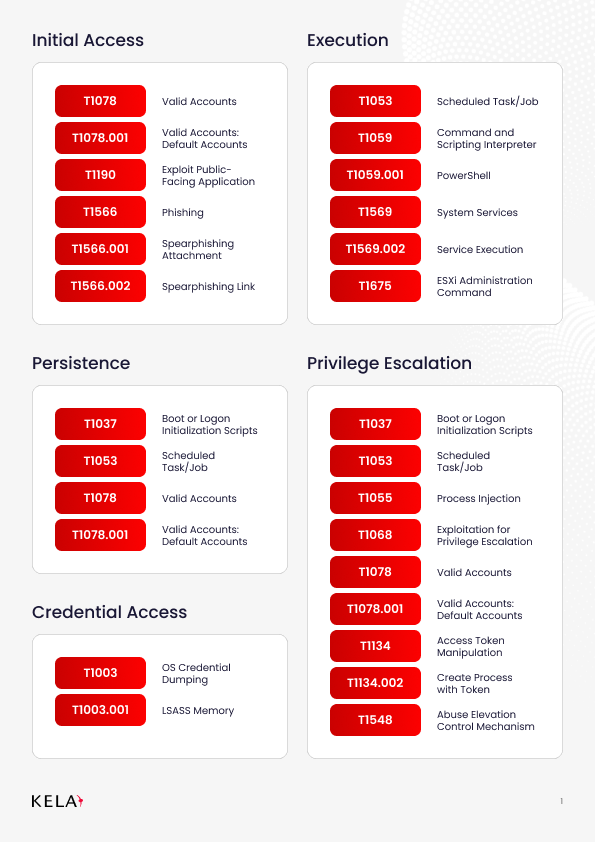
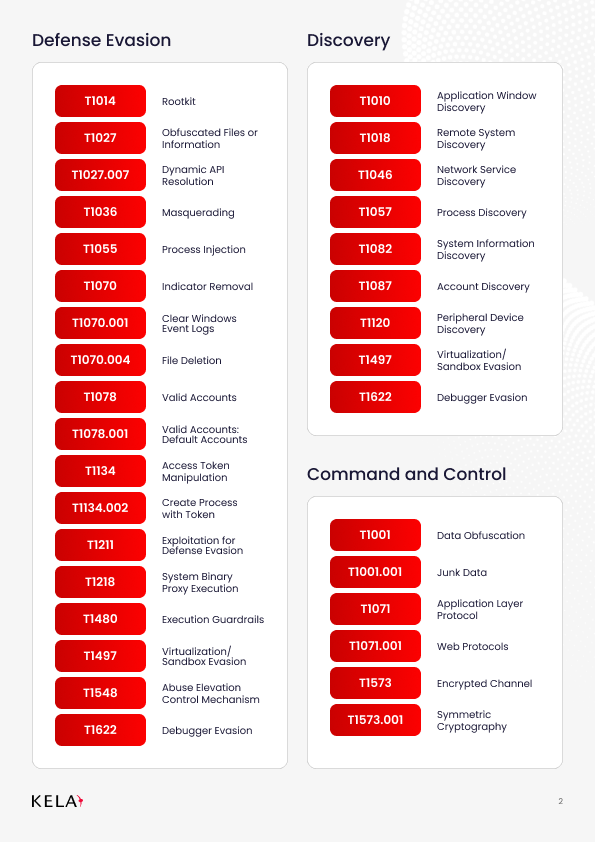
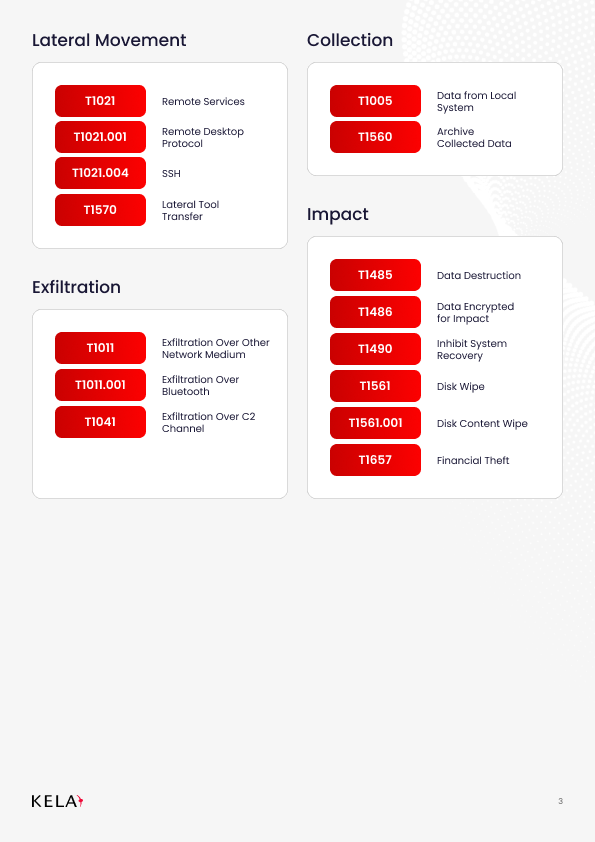
TTP Breakdown MITRE ATT&CK Aligned)
Qilin affiliates leverage a broad range of MITRE ATT&CK techniques, making them adaptable adversaries. Following is the full list:
» Make sure you understand the most targeted entry points by attackers
Toolset & IoCs
Analysis of Qilin’s toolkit highlights both open-source utilities and customized malware:
- Credential and privilege tools: Themida-packed Mimikatz, DonPAPI, NetExec, PowerHuntShares.
- RATs: XenoRAT, MeshCentral.
- Exploit tools: Targeting CVEs such as CVE-2021-40444 and CVE-2022-30190.
- Loaders: SmokeLoader, NETXLOADER to stage further payloads.
- Cryptocurrency infrastructure: APIs linked to exchanges like Thailand’s Bitkub, supporting ransom payment flows.
Indicators of compromise (IoCs) span IPs, hashes, domains, and onion sites, underscoring the global infrastructure supporting their campaigns.
Why It Matters
Qilin’s significance lies in its combination of scale, sophistication, and reach. With the ability to hit Windows, Linux, and ESXi environments, the group ensures no enterprise is out of scope. Their victim list, from global corporations to small municipal offices, shows how ransomware can impact any organization.
Qilin mirrors the complex dynamics of the ransomware ecosystem: affiliate disputes, competitive pressures, and operational security slip-ups all play into how groups evolve. Monitoring Qilin is not only about defending against a single group, but also about understanding how RaaS models shape the broader threat landscape.
» Read more: Ransomware groups are selling network access directly
Mitigation & Defensive Measures
To reduce exposure to Qilin and similar RaaS groups, organizations should:
- Deploy multi-factor authentication (MFA) across all accounts, especially for remote access tools like RDP and SSH.
- Patch systems regularly to avoid exploitation of known vulnerabilities.
- Monitor and restrict the use of administrative tools such as PsExec and PowerShell.
- Implement endpoint detection and response (EDR) solutions to identify malicious activities.
- Restrict use of default accounts and monitor account activity for discovery and misuse.
- Conduct network segmentation to limit lateral movement.
- Employ rigorous backup and disaster recovery strategies, including offline backups.
- Educate employees on phishing awareness and social engineering tactics.
When combined, these measures form a layered defense that reduces the likelihood of compromise and mitigates damage if a breach occurs.
» Ready to get started? Contact us to learn more or try KELA for free